BitLocker encryption was introduced with Windows
Vista and Windows Server 2008. Unlike EFS, which can be used to encrypt
files and folders, BitLocker can be used to encrypt the entire hard
drive. BitLocker Drive Encryption is used for internal hard drives and BitLocker To Go is used to encrypt external or USB flash drives.
You can use BitLocker to protect the data on the drive or protect the system.
Protect the data
Any data drive
(non–operating system drive) can be encrypted with BitLocker to protect
against unauthorized access. BitLocker can be configured to unlock the
data with a password, a smart card, or automatically each time you log
on to the computer.
Protect the system
If you use BitLocker
to protect the operating system drive, BitLocker will check the system
for suspicious events before unlocking the drive. For example, if
hardware components are modified, BitLocker will not unlock the drive
until a recovery key is used.
1. BitLocker with a TPM
A Trusted Platform Module (TPM)
is a microchip that is located on the motherboard of the system. If
your system has a TPM, you can fully protect the operating system's
drive and the critical startup process. TPM version 1.2 and BIOS support
are required to support BitLocker fully.
When a TPM is available,
the operating system drive can be locked with BitLocker using the TPM.
Each time the system is turned on, TPM will verify that the system
hasn't been tampered with before unlocking the drive. BitLocker can use
any of the following methods to unlock the drive:
TPM only
No user interaction is required. As long as TPM doesn't detect anything suspicious, the drive is unlocked automatically.
TPM with startup key
An encryption key is
stored on a USB flash drive. This USB flash drive with the encryption
key is referred to as a startup key. As long as TPM doesn't detect
anything suspicious and the startup key is inserted, the system will
start.
TPM with PIN
A personal identification
number (PIN) can also be used with TPM. The system uses TPM, and the
user must also enter the PIN to unlock the volume.
TPM with startup key and PIN
TPM can also be used with
both a startup key and a PIN. This provides multifactor protection. An
attacker must have the startup key and know the PIN to gain access to
the drive.
NOTE
Authentication can be
based one or more of three factors: something you know, such as a
password or PIN; something you have, such as a smart card or startup
key; and something you are identified with—biometrics. Requiring both a
startup key and a PIN uses two factors: something you have and something
you know. Any authentication method that uses more than one factor is
referred to as multifactor authentication.
2. BitLocker without TPM
It's also possible to
lock the operating system drives on systems without a TPM. For systems
without a TPM, the only option available is the use of a startup key.
The encryption data is stored
on a USB flash drive. This USB flash drive is then referred to as a
startup key. The flash drive must be inserted in the system for the
computer to start. A startup key doesn't provide full protection over
the system's boot process.
3. BitLocker and Data Drives
BitLocker can be used to
protect data drives. A data drive is any drive that doesn't hold
operating system files. This can be an internal fixed drive, an external
hard drive, or a USB flash drive. When using BitLocker to protect the
data drives, you can use one of three options:
Password
Users will be required to enter the correct password before the drive is unlocked.
Smartcard
A smart card is a small
credit card–sized card that has one or more embedded certificates. A
certificate is used to lock the drive, and the smart card must be
inserted to unlock the drive. Many organizations require the use of
smart cards to log on. This same smart card could have a certificate to
unlock the drive.
Automatically Unlock With Logon
It's possible to
configure the drives to unlock automatically when the user logs on to
Windows. This option is available for any removable drives. It can be
used with internal fixed data drives only if the operating system is
also protected with BitLocker.
4. BitLocker Recovery Keys
One of the challenges
with using BitLocker is that legitimate users can be locked out of their
data. This can occur if one of the following events occurs:
The protected drive is moved to a different system.
The TPM is modified. This includes replacing the motherboard or flashing the BIOS.
The startup key is lost or destroyed.
The smart card is lost or destroyed.
The PIN is forgotten.
Depending on the value of
the data protected by BitLocker, the loss could be substantial.
BitLocker will either enter BitLocker recovery mode or simply remain
locked.
BitLocker allows you to use
one of several methods to recover the data. It's important to realize
that you must implement a plan to use these methods before a failure
occurs. If a BitLocker drive enters recovery mode and a recovery method
wasn't implemented earlier, it's too late. The data will remain locked.
The following methods are available to recover data using recovery keys.
Recovery key or recovery password
If the smart card is not
available or the user has forgotten the password, a 48-digit recovery
password can be used to unlock the drive. A recovery key can also be
used in place of a password. This key is stored on removable media, such
as a USB flash drive. It can also be printed out and stored in a secure
location.
Data recovery agent
A data recovery agent (DRA) can be configured in Group Policy using the Computer Configuration => Policies => Windows Settings => Security Settings => Public Key Policies =>
BitLocker Drive Encryption node. When a DRA is designated, the DRA can
recover the drive. The following link shows the process to create
certificates for the DRA and designate a DRA: technet.microsoft.com/library/ee424312.aspx.
Backup of keys in Active Directory Domain Services
For systems in a domain,
you can store recovery keys in Active Directory Domain Services (AD DS).
This is configured via Group Policy in the Computer Configuration => Policies => Administrative Templates => System => Trusted Platform Module Services node. The setting is Turn On TPM Backup To Active Directory Domain Services, as shown in Figure 1.
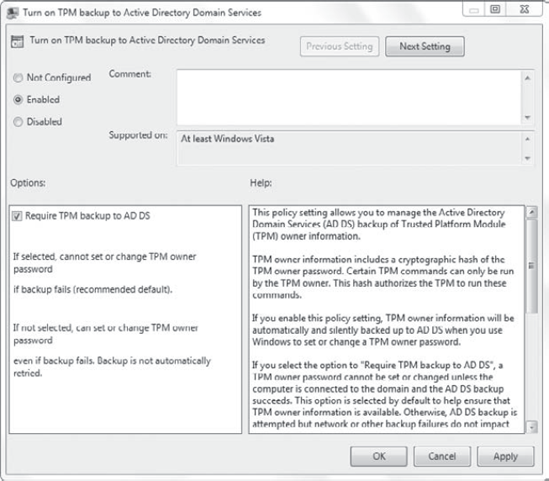
Before you can store BitLocker recovery data in AD DS, you'll need to ensure that some prerequisites have been met.
5. Storing BitLocker Recovery Data in AD DS
If the domain is using Windows
Server 2008 domain controllers, you'll automatically be able to store
the BitLocker recovery data in AD DS. However, if you have domain
controllers running earlier operating systems, or upgraded from earlier
operating systems, you'll need to take a few extra steps.
These are the overall steps to prepare your domain:
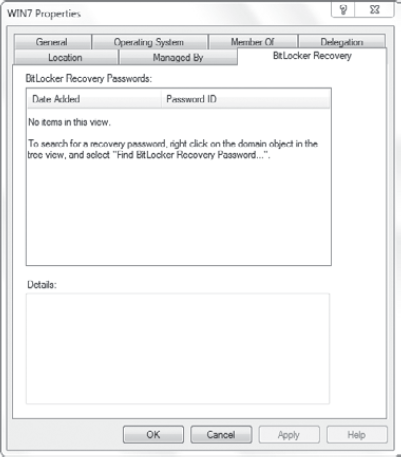
6. BitLocker Active Directory Recovery Password Viewer Tool
Another feature that is
available is the BitLocker Active Directory Recovery Password Viewer
Tool. If BitLocker keys are stored in AD DS, you can use this tool to
retrieve them. When this tool is installed, you can access the
properties of a computer in Active Directory Users and Computers. Select
the BitLocker Recovery tab, as shown in Figure 2.
|
After adding the Active
Directory Recovery Password Viewer Tool, you also need to extend Active
Directory Domain Services. This is done by running the following command
using an account with Enterprise Admins permissions: regsvr32 bdeaducext.dll. This will enable the BitLocker Drive Encryption (BDE) extensions for Active Directory Users and Computers.
|
|
Log on to the Windows 7 computer, and launch the GPMC via the Administrative Tools menu.
Browse to the Default Domain Policy. Right-click the Default Domain Policy and select Edit.
Browse to the Computer Configuration => Policies => Administrative Templates => System => Trusted Platform Module Services node.
Double-click
the Turn On TPM Backup To Active Directory Domain Services setting.
Select Enabled. Ensure that Require TPM Backup To AD DS is selected and
click OK.
Launch a command prompt with administrative permissions. Execute the following command to refresh Group Policy:
Gpupdate /force
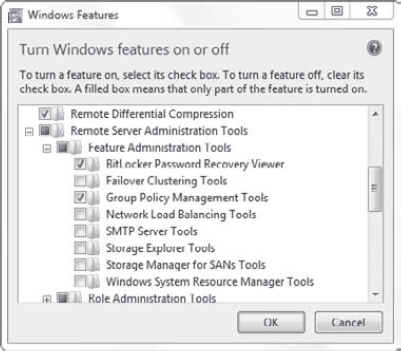
Click Start => Control Panel. Type Features in the Search Control Panel box. Click Turn Windows Features On Or Off.
Expand
Remote Server Administration Tools and Feature Administration Tools.
Select BitLocker Password Recovery Viewer, as shown in the following
graphic.
Scroll down to the Role Administration Tools. Expand Role Administration Tools => AD DS => AD LDS Tools =>
AD DS Tools. Select AD DS Snap-ins And Command-line Tools. Click OK.
This will install Active Directory Users and Computers and some other
management consoles.
Log
on to the domain controller using an account with administrative
permissions. Launch a command prompt with administrative permissions and
execute the following command:
regsvr32 bdeaducext.dll
Return to Windows 7. Launch Active Directory Users and Computers via the Administrative Tools menu.
Browse
to the location of a computer object. Right-click the computer object
and select Properties. The BitLocker Recovery Password tab will now be
present.