5. UAC Virtualization
By
default, UAC virtualizes requests for protected resources to provide
compatibility with applications not developed for UAC. This is
important, because many applications written for Windows XP and earlier
operating systems assume that the user has administrative privileges and
attempt to write to protected resources such as the Program Files or
System folders.
UAC virtualization redirects requests for the following resources to safer, user-specific locations:
When a user process attempts to add a file to a
protected folder, UAC redirects the request to the
\AppData\Local\VirtualStore\ folder in the user’s profile. For example,
if a user named MyUser runs an application that stores a log file at
C:\Program Files\MyApps\Logs\Log.txt, the file write attempt will
succeed. However, UAC will actually store the file at
C:\Users\MyUser\AppData\Local\VirtualStore\Program
Files\MyApps\Logs\Log.txt. The application will be able to access the
file at C:\Program Files\MyApps\Logs\Log.txt, but the user will need to
browse to her profile to access the file directly because virtualization
affects only the application process itself. In other words, if the
user browses to open the log file from within the application, it will
appear to be under %Program Files%. If the users browses to open the log
file using an Explorer window, it will be under her profile.
The first time an application makes a change to a
virtualized resource, Windows Vista copies the folder or registry key
to the location within the user’s profile. Then, the change is made to
the user’s copy of that resource.
UAC virtualization is designed to allow
already-installed applications to run successfully with standard user
privileges, even if they store temporary files or logs in a protected
folder. UAC virtualization does not allow users to install applications
that make changes to these resources; users will still need to provide
administrative credentials to do the installation.
When an executable has a requested execution
level manifest, Windows Vista automatically disables UAC virtualization.
Therefore, virtualization should never be a factor for applications
designed for Windows Vista. Native 64-bit applications are required to
be UAC-aware and to write data into the correct locations, and thus are
not affected. Virtualization also does not affect applications that
administrators run with elevated privileges.
If you plan to run applications that would
support virtualization, and you specifically want to prevent UAC from
virtualizing requests from the application, you can disable
virtualization by using the Application Compatibility Toolkit to mark
the application. Setting the NoVirtualization marking
makes applications easier to debug (because you don’t have to worry
about file and registry requests being redirected) and it reduces the
attack surface by making it more difficult for malware to infect an
application (because that application’s files would not be moved into
the relatively unprotected user profile).
6. UAC and Startup Programs
By default, UAC blocks startup applications
located in the Startup folder or identified in the Run registry key that
require elevated privileges for both standard and administrative users.
It would simply be too annoying to have multiple UAC prompts when
logging on, and forcing users to confirm the prompts would require them
to blindly elevate processes they did not explicitly launch—a bad
security practice.
Instead of a UAC prompt, UAC displays a
notification bubble stating that Windows has blocked some startup
programs. The user can click the bubble to view and launch the blocked
programs within Windows Defender (Windows Defender provides the user
interface, but is not itself responsible for blocking startup programs).
As an administrator, you should ensure that no startup programs require
elevated privileges.
Startup applications launched from the RunOnce
registry key or specified in a Group Policy setting are unaffected by
this feature; UAC will still prompt the user for administrative
credentials. This allows applications that must make changes after
restarting the computer to complete installation successfully.
7. Compatibility Problems with UAC
For applications to receive the Certified For
Windows Vista logo, the application must be designed to work well for
standard users unless the tool is specifically intended for use by
administrators. However, many applications were developed prior to
Windows Vista and will not work correctly with UAC enabled. Some of the
more significant applications that might experience problems with
specific features include:
Microsoft SQL Server Desktop Engine (MSDE) MSDE is not supported on Windows Vista, but SQL Server 2005 Express is.
Microsoft Visual Studio 6.0 and Microsoft Visual Studio 2003 Microsoft currently has no plans to support these versions of Microsoft Visual Studio on Windows Vista.
Microsoft Visual Studio 2005 Windows Vista Service Pack 1 must be installed for compatibility with Windows Vista.
Additionally, some older antispyware, antivirus,
firewalls, CD/DVD-authoring, disk-defragmentation, and video-editing
tools designed for Windows XP will not work with Windows Vista.
Typically, most features of an application will
work correctly with UAC enabled, but specific features might fail. You
have several ways to work around this:
Run the application with administrative credentialsYou can specify that an application always requires administrative credentials.
Modify permissions on the computer
If an application requires access to a protected resource, you can
change the permissions on that resource so that standard users have the
necessary privileges. Instructions on how to isolate the protected
resources are provided later in this section.
Run Windows XP (or an earlier version of Windows) in a virtual machine
If the application fails with administrative privileges or you do not
want to grant the application administrative privileges to your
computer, you can run the application within a virtual machine. Virtual
machines provide an operating system within a sandbox environment,
allowing you to run applications within Windows XP without requiring a
separate computer. You can maximize virtual machines so that they
display full-screen, providing a similar experience to running the
operating system natively. Virtual machines perform slightly slower than
applications that run natively within Windows Vista, however. Virtual
PC is a free download from Microsoft, and Windows Vista Enterprise and
Windows Vista Ultimate include the right to install Windows XP in a
virtual machine without paying additional fees.
Disable UAC
You can disable UAC to bypass most application-compatibility problems
related to the permission changes in Windows Vista. However, this
increases the security risks of client computers when running any
application, and therefore is not recommended. To disable UAC, read “How to Configure User Account Control” later in this section.
To isolate the protected resources accessed by an application, follow these steps:
1. | On a Windows Vista computer with UAC enabled, download and install the Microsoft Application Verifier from http://www.microsoft.com/downloads/details.aspx?FamilyID=bd02c19c-1250-433c-8c1b-2619bd93b3a2.
|
2. | |
3. | Start the Standard User Analyzer. On the App Info tab, click Browse and then select the application’s executable file.
|
4. | Click
Launch, and respond to any UAC prompts that appear. The Standard User
Analyzer will start the application. Use the application, especially any
aspects that might require elevated privileges, and then close the
application.
|
5. | Click the View menu and select Detailed Information.
|
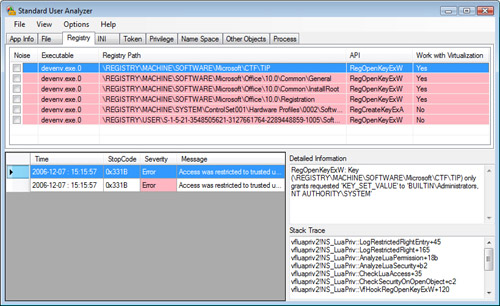
6. | Wait a few moments for the Standard User Analyzer to examine the application log file, as shown in Figure 6.
Browse the different tabs to examine any errors. Errors indicate that
the application attempted to perform an action that would have failed if
it were not run with administrative privileges.
|
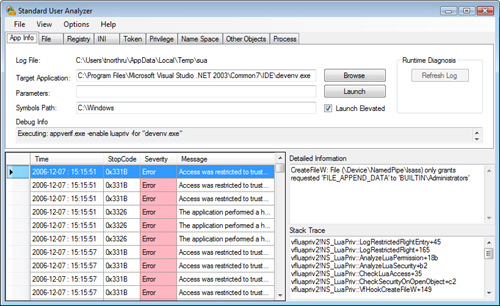
On the File tab and Registry tab (as shown in Figure 7),
notice the Work With Virtualization column. If the column is Yes, that
particular error will not cause a problem as long as UAC virtualization
is enabled. If UAC virtualization is disabled, the error will still
occur. If the column is No, it will always be a problem unless the
application is run as an administrator.