After SharePoint has been installed, the next step is
to configure the PPS service application. You must complete this step
regardless of the installation type you selected.
In this example, you select
to do a server farm installation in preparation for future expansion.
The SharePoint farm starts as a single application server deployment.
However, additional web and application servers can be added later to
scale for future growth and expanding data requirements.
In this type of installation, the administrator needs to complete the following tasks in the order shown here:
1. | |
2. | |
3. | |
4. | Configure
all other service applications that will be useful in the deployment,
such as Excel Services or SQL Server Reporting Services Integration.
|
Configuring the Secure Store Service
The Secure Store Service is a
service that encrypts selected data stored within it. A user-generated
encryption key is required to ensure that the data is secure. This is a
new addition to the SharePoint feature set in SharePoint 2010.
Note
For security reasons, PPS
requires the Secure Store Service to be manually configured before it
can be used. This ensures that passwords are not stored as plain text in
the database.
The data that is encrypted is
To configure the Secure Store Service, follow these steps:
1. | Launch
SharePoint Central Administration from the Start menu. Select Start,
All Programs, Microsoft SharePoint 2010 Products, SharePoint 2010
Central Administration.
|
2. | From Application Management, select Manage Service Applications.
|
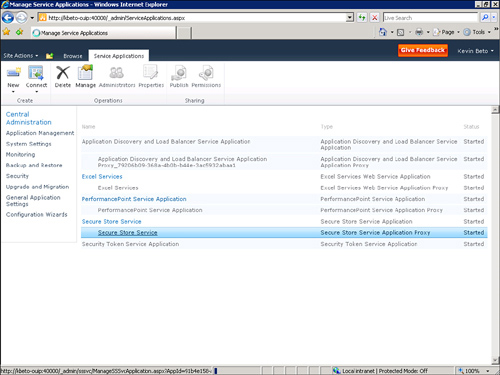
3. | Scroll to find and select Secure Store Service, and then click Manage on the ribbon (see Figure 1).
Tip
Two different types of
Secure Store Service objects are created for you: the Secure Store
service application and the Secure Store proxy. Both of these objects
have links that should lead to the same page, which means that you may
select either link.
|
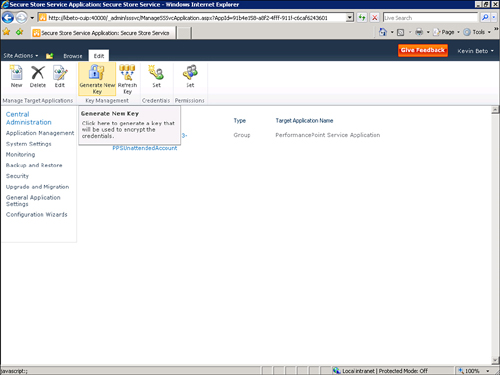
4. | From the Secure Store Service configuration page, select Generate New Key (see Figure 2).
|
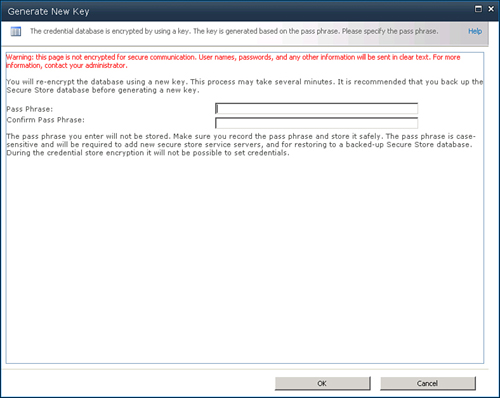
5. | Enter a secure passphrase in the dialog box (see Figure 3).
Because it is protecting potentially sensitive data, make sure this is a
strong password. Accept the check to Re-encrypt the Database Using the
New Key, and then click OK. The database will be encrypted.
Note
Wikipedia suggests the following guidelines for creating strong passwords:
Include numbers, symbols, and upper- and lowercase letters in passwords. Password length should be between 12 and 14 characters. Avoid
any password based on repetition, dictionary words, letter or number
sequences, usernames, relative or pet names, or biographical
information.
(“Password Strength” from Wikipedia, the free encyclopedia, http://en.wikipedia.org/wiki/Strong_password#Examples_that_follow_guidelines)
Caution
To
increase security, you should first configure the Central
Administration pages to use Secure Sockets Layer (SSL). Alternatively,
you need to ensure that the browser is running directly on the server so
that Internet traffic is not going through a proxy server. If you do
not do this, the passphrase you enter here can be viewed by a packet analyzer.
A packet analyzer is a hardware or software utility that intercepts
network traffic and allows an unauthorized user to see the password you
are setting. The password appears in plain text on the HTTP packet. The
packet analyzer can pick up the password you are sending to the server
to configure the Unattended Service Account.
|
6. | When
the Secure Store Service key is generated successfully and the database
is encrypted, click Home to return to the Service Application
Management.
|