1. The Need for Effective Patch Management
Today’s computer systems and networks are under
an unprecedented level of threat, ranging from viruses and worms to
malicious insiders. Patch management, when properly implemented as part
of a defensive strategy, can help organizations adopt a security posture
and mitigate vulnerability in their systems. Consequently, patch
management is becoming an increasingly important topic for both
management who are anxious to demonstrate corporate responsibility to
shareholders and for the IT manager, whose job it is to maintain and
keep running secure systems.
Trojan Horses, Viruses, and Worms
According
to the joint 2003 Computer Security Institute/Federal Bureau of
Investigation Computer Crime and Security Survey, 82 percent of
respondents detected an attack related to a virus, which was defined as a
virus, a Trojan horse, or a worm. The average reported loss due to
virus activity was $199,871 per organization. The past 12 months have
seen two fast-spreading and debilitating worms: SQL Slammer and MS
Blaster. Before that there were Code Red and Nimda. Many organizations
had to expend considerable resources defending against and cleaning up
after these attacks against their infrastructure.
As alarming as this state of affairs is, what is
perhaps more alarming is that in each case updates were available to
remove the vulnerability exploited by each worm. Figure 1
shows the time from release of an update to discovery of an exploit in
the wild for some of the more damaging of the recently discovered Trojan
horses, viruses, and worms.
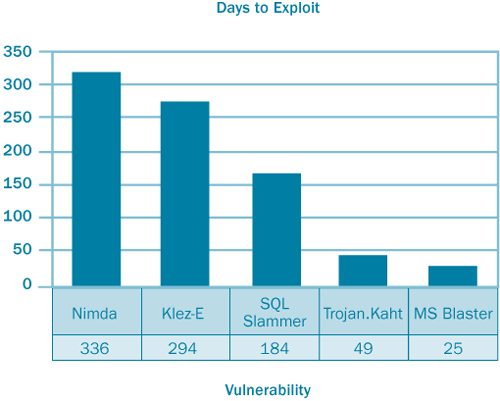
As the chart shows, the trend is moving towards
zero-day exploits, where an exploit is discovered on the same day that
Microsoft releases an update to remove the vulnerability. The
diminishing window between update and exploit is perhaps one of the more
compelling arguments for an organization to implement a patch
management process, one that’s capable of deploying updates quickly,
reliably, and efficiently.
2. Introduction to the Patch Management Process
This process, introduced in MSM 2.5, uses a
four-phase approach of Identify, Evaluate & Plan, and Deploy and
was based on several MOF functions. Also discussed is the implementation
of an SMS 2003 infrastructure and its functions in patch management and
deployment, along with instructions on responding to patch emergencies
and accelerated timelines.
The Microsoft Operations Framework (MOF)
There are many approaches to planning and
implementing patch management solutions. The preferred approach is to
base a solution upon an existing operations framework, such as MOF. MOF
was designed to provide prescriptive guidance to organizations about how
to manage their IT operations. MOF consists of three models:
The process model
The team model
The risk model
Of specific interest to patch management, the MOF
process model is a functional
model of the processes performed by operations teams when managing and
maintaining IT Services. It’s based upon the Office of Government
Commerce’s IT Infrastructure Library (ITIL), a widely accepted body of
practice for operations management. The team model and risk model
might also be of interest, as they provide guidance on the formation of
patch management teams, including duties and responsibilities, and a
structured approach to managing risk, which is useful when evaluating
alerts of vulnerability and software updates and determining the best
course of action.
The MOF process model defines four quadrants of management, as shown in Figure 2. The quadrants are Changing, Operating, Supporting, and Optimizing. Each quadrant has a mission of service.
In the Changing quadrant the mission is to introduce new service
solutions, technologies, systems, applications, and processes. The
mission of the Operating quadrant is to perform and manage the daily
tasks associated with running IT Services. As the name suggests, the
Supporting quadrant’s mission is to resolve incidents, problems, and
inquiries as they arise. Lastly, the Optimizing quadrant’s mission is to
examine the environment the IT Services run in and drive changes to
optimize cost, performance, capacity, and availability.
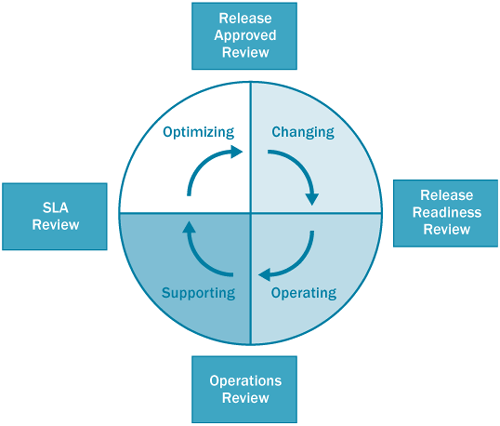
Within each quadrant are major management review
processes. These are necessary checkpoints used to guarantee success of
the management processes. The reviews are split into two categories:
time-based and release-based. The Release Readiness Review and Release
Approved Review are release-based reviews and take place before and
after a release into the computing environment. The Operations Review
and SLA (Service Level Agreement) Review, both time-based reviews,
should occur at regular intervals to assess the performance of the
internal operations and the agreed-upon customer service levels.
Any comprehensive patch management solution will
touch on all four quadrants of the MOF process model—for example, an
organization is focused on auditing systems for patch compliance and
monitoring alerts for vulnerability and software updates in the
Operating quadrant, on assessing and planning response to alerts and
downloading and evaluating any updates in the Supporting quadrant,
packaging and testing updates in the Optimizing quadrant, and
distributing and installing updates as well as auditing and rolling back
the update if required in the Changing quadrant.
The Microsoft-Recommended Patch Management Process
Introduced
in Microsoft Solutions for Management 2.5 and based on the MOF Change
Management, Release Management, and Configuration Management service
management functions, the Microsoft-recommended patch management process
is a four-phase approach to managing updates to software. The four
phases are Assess, Identify, Evaluate & Plan, and Deploy. The
process and its four phases are shown in Figure 3.
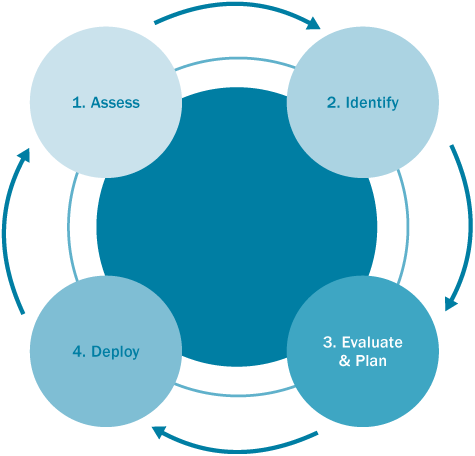
Defined events trigger movement through the
phases of the process. Beginning with the Assess phase, the triggering
event that causes a move to the Identify phase is notification that a
software update exists. The event that causes a move from the Identify
phase to the Evaluate & Plan phase is the submission of a formal
Request for Change (RFC). The triggering event for a move to the Deploy
phase from the Evaluate & Plan phase is the receipt of approval to
deploy the software update into the production environment. Finally, the
move from the Deploy phase to the Assess phase and the beginning of the
process cycle again is triggered by completion of the release of the
software update.
Within each phase there are discreet steps that
together implement the patch management process. These steps, and the
phases they belong to, are described in Table 1.
Table 1. Steps in the four-phase patch management process
| Phase | Steps |
|---|
| Assess | Inventory/discover existing computing assets. Assess security threats and vulnerabilities. Determine the best source for information about new software updates. |
| | Assess the existing software distribution infrastructure.Assess operational effectiveness. |
| Identify | Discover new software updates in a reliable way. Determine whether software updates are relevant. Obtain and verify software update source files. Determine nature of software update and submit RFC. |
| Evaluate & Plan | Determine the appropriate response. Plan the release of the software update. Build the release. Conduct acceptance testing of the release. |
| Deploy | Deployment preparation. Deployment of the software update to targeted computers. Post-implementation review. |
Although
no technology solution can automate the entire patch management
process, they can help somewhat, and SMS 2003 integrates well into patch
management processes.