The IT industry long ago saw the issue of
network vulnerability due to problematic computers connecting to the
network coming and has been furiously investigating solutions to enforce
company security policies physically. Network Access Control (NAC) was
created to combat this very issue. NAC provides a framework for vendors
to produce services and features that can interrogate a computer prior
to a connection to the secure, internal network and ensure a computer’s
compliance with stated health requirements and security settings.
Microsoft has introduced its version of
controlling network access with NAP, which provides an enforcement
service for health requirement policies prior to network access. NAP
offers services, components, and an application programming interface
(API) that provide an inherent solution for ensuring the health of
servers and networks running Windows Server 2008 as well as of computers
running Windows Vista and Windows XP Service Pack 3 as clients.
1. Network Access Protection Overview
Network Access Protection (NAP) provides a
platform for validating the health of computer systems prior to allowing
access to protected networks. In doing so, a level of assurance can be
attained that a computer has at least been “inspected” prior to
accessing the private network every time a new connection is made. The
validation a computer undergoes can now be logically enforced.
Prior to NAP, a typical connection from an
external computer would involve a client connecting across a public
network such as the Internet, using a VPN connection. The client
connection would initially pass through a firewall or be forwarded by a
proxy using the appropriate communication ports required by the chosen
security protocol. An authentication service would then examine the
credentials of the remote access client. If the credentials were
successfully authenticated, the client would be connected to whatever
portion of the protected network the connection was previously set up to
accomplish.
This
scenario has a major flaw. If the remote access client is exactly who
it purports to be, provides all the necessary credentials appropriately,
and performs only the tasks on the private network that the connection
was set up to do, would there still be a problem? Maybe. Suppose the
remote access client performs unintended service requests, discovery,
research, or—worse—invasive software installations without the knowledge
of the user of the computer making the remote access connection. This
has become one of the primary reasons for implementing a NAP solution.
|
Paul Mancuso
After spending a considerable amount of time,
effort, and money, you have deployed across an entire network the
following security services:
A top-of-the-line perimeter firewall device An antivirus module inside the firewall device whose services you have configured to check for updates once every hour An
automated update service for workstations and servers to call upon
periodically for updates to the operating system and installed
applications An enterprise anti-malware
service that installed anti-malware agents on all client workstations
and servers within the environment, with centralized management for
setting and configuring changes and updating installed software and
agents on deployed computers
Feeling that the enterprise has a reasonable
level of security, you go home and think that tomorrow should now be a
relatively peaceful day.
In the evening, a salesman visiting a branch
office connects his laptop to the protected network. The salesman’s
laptop is considered safe merely because it is corporate property. A
worm that was released into the wild that day had infected the corporate
offices of another corporation, where the salesman had plugged the
laptop in while delivering a presentation. The worm can now perform
functions inside the network from a device considered to be a secure
system. Tomorrow comes, and virus reports are coming out of the
woodwork.
Several factors could have caused the salesman’s
laptop to become infected. First, it is presumed that the salesman does
not alter the basic security settings of either the security software
or the operating system. Also, the laptop is part of the domain;
internal group policies were set to ensure the timely scheduling of
updates to either the operating system or the security software on all
computers, including those the salesman uses. This last presumption
leads to missed updates when the salesman is traveling and not connected
to the network.
These periodic lapses in acquiring updates
provide opportunities for infections when the salesman connects the
laptop to unknown environments. The salesman’s laptop can acquire all
kinds of Trojan horse programs, viruses, and worms. The salesman travels
back to the office, plugs the infected laptop into the protected
network, and unknowingly unleashes the malicious programming on the
laptop into the protected network. The salesman has bypassed all the
security precautions the enterprise administrator has painstakingly set
up in the network.
|
With a NAP solution, the possibilities of a
traveling employee or guest unleashing an infection into your secured
network are lessened. The standard communication flow from a computer
being introduced to a network for its initial connection to the network
would be altered to pass through a perimeter network as the components
of the NAP platform engage. The NAP platform would now involve an entire
NAP ecosystem with the connection request of an external client now
referred to as a NAP client. The perimeter network would still include
the same security services and devices as before, but now the NAP
client’s request for access takes a detour as the various components of
the NAP platform engage to determine the health status of the connecting
client. Figure 1 shows the difference between a traditional remote access connection and one involving a NAP platform.
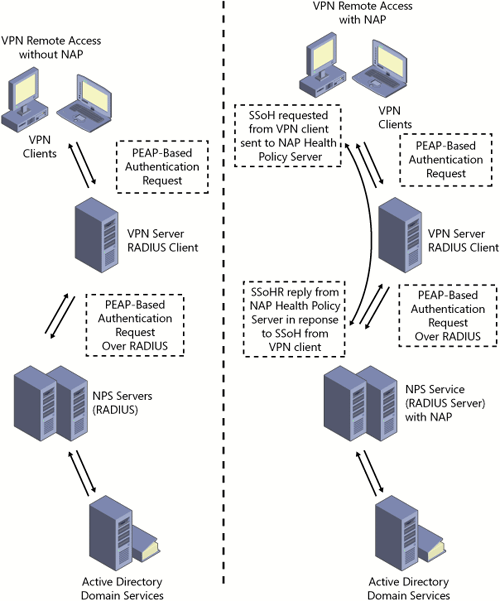
Figure 1
shows that not only are NAP components now involved in the
communication flow, but also that the NAP client might be restricted to
an external network referred to as the remediation network, where
additional servers using health resources update the client and bring it
into compliance.
A complete NAP solution involves three distinct features:
Health state validation
Health policy compliance
Limited access
Health state validation is the process of
validating a computer’s health and determining its compliance. If the
NAP platform is configured for a remediation network, a noncompliant
computer is restricted to only the remediation network’s subnet until it
meets compliance. If the NAP platform has been implemented initially
with logging only to quantify compliance issues, the health compliance
of a computer is logged, and it is allowed to proceed with the normal
connection routine.
To monitor and possibly enforce health policy
requirements, administrators create health policies. The health policy
component is the heart of a NAP solution. Health policies mandate the
level of software updates, operating system build, antivirus revision,
and firewall features implemented among many other possible health
compliance factors.
When computer systems do not meet the level of
health compliance necessary to connect to the private network, an
administrator can mandate one of two outcomes, either to allow the
connection and log the noncompliant issues or to shunt the connection to
a remediation network to configure and update any noncompliant aspect
of the computer. This is the limited-access feature of NAP.
Note: Network Access Quarantine
Limited access has some similarities to Network
Access Quarantine Control, but only in one principal feature: limiting
access for noncompliant computers when making dial-up and VPN
connections. Limited access when implemented with a NAP platform
provides much capability and a standardized structure. This structure
facilitates the addition of third-party enhancements and services. NAP
also extends beyond VPN and dial-up communication to include protection
when computer systems connect on the LAN. For more information, please
visit the Cable Guy article on Network Access Quarantine at http://technet.microsoft.com/en-us/library/bb877976.aspx.
Overview of NAP Infrastructure
The NAP infrastructure for all types of enforcement provides a similar architectural overview as displayed in Figure 2. Only the devices and regions of interest to a NAP solution are pictured.
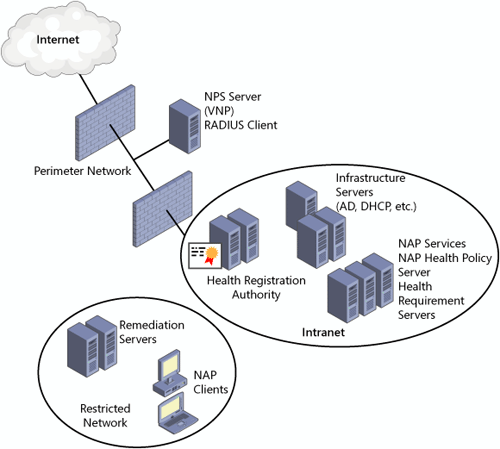
The
Internet lies outside the perimeter network and is separated by the
perimeter firewall. VPN clients access the internal network from this
region.
The perimeter network is segregated by a perimeter and internal firewall.
VPN
servers reside here and provide the initial point of enforcement for a
NAP VPN enforcement point. For security purposes, no other NAP service
is needed in this location.
The
restricted network is logically separated from the intranet for
computers that, although having passed authentication for the NAP
enforcement points that require authentication, have not yet acquired
the necessary authorization to access the secure intranet. Servers
deployed here can include quite a range of NAP support services:
The
usual DNS, Windows Internet Name Service (WINS), Active Directory
domain controllers, and DHCP servers along with other supporting network
infrastructure devices can be deployed.
Servers supporting software updates such as Windows Server Update Services (WSUS) can be deployed.
For wired switches employing 802.1x enforcement, any switch ports can be associated logically with the restricted network.
For
wireless access points employing 802.1x enforcement, the entire access
point might be logically associated with the restricted network because,
at any time, it can be servicing compliant and noncompliant computers.
Where NAP Works
NAP can be implemented in any scenario in which a
computer or network device has left a network and requires a new
connection when brought back to the network. Following are specific
scenarios of this type of event.
Desktop computers that have been dormant for periods of time
Laptops for roaming users
Personal desktops and laptops of corporate users when connecting to the network to retrieve e-mail and other data
Laptops of guests
Laptops and desktops from users of partner firms connected by an extranet
This list comprises the general
categories in which a NAP solution would provide a level of assurance of
the health of a connected computer. Due to the diversity of these
categories, the same level of enforcement of noncompliant computers
might not be possible in all situations. Computers that are unmanaged,
such as partner computers, home computers, laptops, and those of guests
would be sent to the restricted network and, might not be required to
undergo remediation, but also would not be allowed into the private
network. Managed computers provided by the corporation could institute
automatic remediation for any of its computers moved into the restricted
network. Options to remediate would vary, depending on the situation.