1. Configuring Exchange Databases
Exchange Server 2010
stores mailboxes and public folders in Exchange databases. Mailbox
servers can contain both public folder and mailbox databases. Each
database is stored in a single Extensible Storage Engine database (.edb)
file. The database file in which a particular message is stored does
not change, regardless of the type of client that sends or reads the
message.
Note:
CREATING AND CONFIGURING EXCHANGE DATABASES
You must be assigned
the Organization Management role to enable you to create and manage
mailbox or public folder databases on any Mailbox server or the Server
Management role to create databases on a specific server in an Exchange
organization. Users assigned the View Only Organization Management role
can view database properties but cannot modify any of those properties.
Each
database has a single set of transaction logs that record changes to
the database, including messages sent to or from the database.
Transaction logs can be used in disaster recovery scenarios if
high-availability features
are not implemented. However, their primary function is to ensure that
Exchange Server 2010 follows the Atomicity, Consistency, Isolation, and
Durability model for databases. Each individual database and its
transaction logs are by default stored in the same folder but in a
different folder from all other databases. By default, the folders that
hold the databases are stored in the folder path C:\Program
Files\Microsoft\Exchange\Server\v14\Mailbox, as shown in Figure 1.
A single folder by default
holds both the database and its transaction logs. You should, however,
consider storing transaction logs in separate folders and on a different
hard disk from the databases. Because transaction logs can be used in
disaster recovery in situations where high-availability solutions are
not implemented, you might be unable to restore to the point of failure
if you lose both the database and its transaction logs in the same disk
crash.
Note:
Exchange Server 2000
and Exchange Server 2003 enabled multiple databases to share a single
set of transaction logs through the use of storage groups. Exchange
Server 2007 also offered this functionality but only for databases that
did not have high-availability features enabled. In Exchange Server
2010, each database must have its own set of transaction logs. If you
see an answer in the 70-662 examination that proposes shared transaction
logs or a storage group, then you can reject this answer.
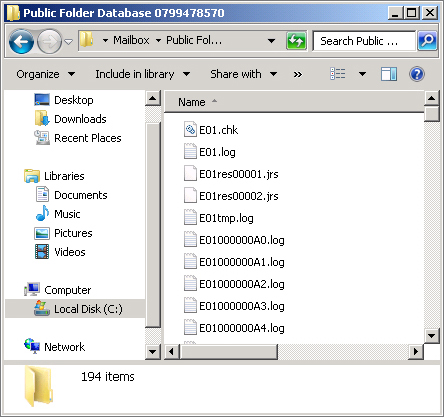
The folder that contains an Exchange database (.edb) file can also contain other types of files. Figure 2 shows the files in a public folder database folder. The possible file types in an Exchange database folder are as follows:
Checkpoint file (.chk) Determines which transactions in the current transaction log need to be committed to the database.
Current transaction log file (exx.log)
The file into which new transactions are written. When this file
reaches its storage limit of 1 megabyte (MB), Exchange Server 2010
closes the log file, renames it, and creates a new current transaction
log file.
Closed transaction log file (.log)
Closed transaction log files have the same file type (.log) as the
current transaction file but have a longer file name. For example, a
current transaction file E00.log might be named E000000000001.log when
its size reaches 1 MB.
Reserved transaction log files (.jrs)
Exchange Server 2010 uses these files as emergency storage when the
disk becomes full and it cannot create a new transaction log. The
database is taken offline, and any transactions that cannot be written
to the current log are written to a reserved transaction log file.
Reserved transaction log files are 1 MB in size.
Temporary workspace file (<log prefix>tmp.log) The transaction log file for the temporary workspace (for example, E00tmp.log). The size of this file cannot exceed 1 MB.
Exchange database file (.edb)
Stores content for mailbox and public folder databases. The size limit
for this type of file is 64 terabytes (TB), although in practice a lower
size limit will probably be imposed by disk size restrictions.
Detailed
instructions for configuring a mailbox database are given later in this
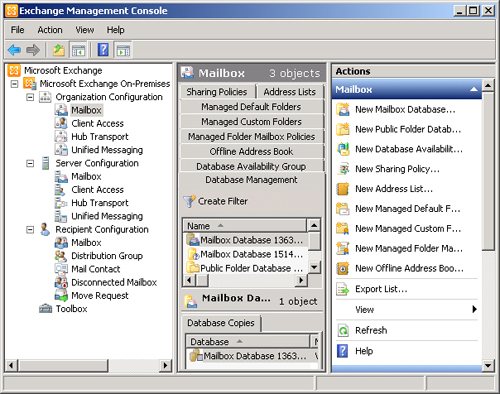
lesson. However, for high-level configuration of database options in
the EMC, click Mailbox under Organization Configuration and select the
Database Management tab, as shown in Figure 3.
Right-click the database you want to configure and click Properties.
This accesses the General, Maintenance, Limits, and Client Settings
tabs.
The General tab gives
information about the database, such as its backup status, when it was
last modified, the server on which it is mounted, the path to the
database file, and servers that have a copy of the database.
|
Circular logging can be
used in situations where limited storage capacity is an issue. However,
Microsoft recommends that Exchange Server 2010 databases not be
configured to use circular logging if you also plan to use the Volume
Shadow Copy Service to enable third-party backup and recovery
operations.
If
circular logging is enabled, transaction logs in the same directory as a
database may be deleted when that database is restored so that only
point-in-time recovery operations are possible. Also, incremental and
differential backup operations are not permitted if circular logging is
enabled.
Finally, if circular logging
is enabled while you are performing a backup or recovery operation, the
restoration of individual databases will be prohibited.
|
On the Client Settings tab, you
can specify the default public folder database and, if appropriate, the
default offline address book for all mailboxes in a database.
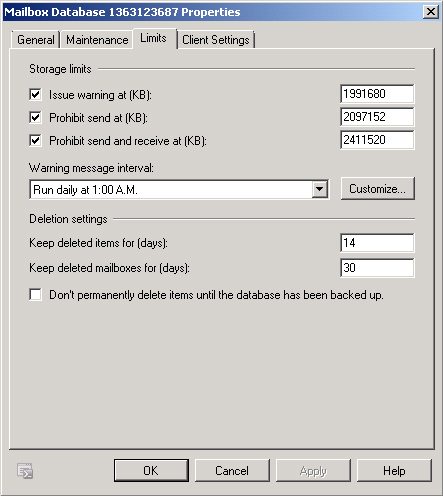
The Limits tab, shown in Figure 4,
lets you specify the storage limits for the database, at what database
size a warning is issued, and the database file sizes at which Send and
Send and Receive are prohibited. You can configure the notification
schedule for sending messages to users who have exceeded these limits.
The tab permits you to specify deletion settings that determine how long
the database retains mailboxes and deleted items within mailboxes after
a user deletes them.
Note:
RECOVERABLE ITEMS AND THE DUMPSTER
For more information about recoverable items and single item recovery, access http://technet.microsoft.com/en-us/library/ee364754.aspx and follow the links.