Microsoft Software Update Service (SUS) and Windows Update Service (WUS)
SUS has been Microsoft's initial
attempt to provide a tool to automate the download and application of
security patches, service packs, and other updates to servers and
workstations. Currently, the new WUS has not been released.
Software Update Service (SUS)
When a SUS server is identified, the SUS software is
installed. This server is configured to download from Microsoft's
Windows update site periodically (default is 3 a.m. daily). The SUS is
then enabled through a Group Policy, where you specify the name of the
SUS server. The clients that the policy applies to download the updates
periodically and either notify the user of their availability or
automatically apply them (optional).
The SUS server is domain-independent. Thus, if you
have several domains, you can have a single SUS server to serve all
computers in all domains. You can also specify a hierarchy of SUS
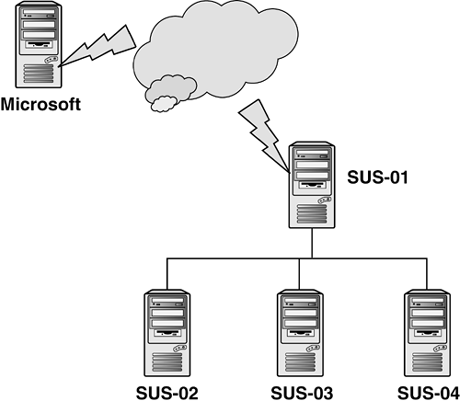
servers, as shown in Figure 7.
In this example, the top-level SUS server, SUS-01, gets the downloads
from Microsoft. The second-level servers, SUS-02, SUS-03, and SUS-04,
download from SUS-01. Because they are located via HTTP, they are
domain-independent and can be placed at convenient locations in the
network for best performance in serving clients.
Some of the features of the SUS include
You can download from Microsoft or other SUS servers.
The Administrator can configure the download schedule.
The
Administrator can configure patches, service packs, and so on to be
automatically applied at the client or to require Administrator approval
before deploying to the client.
Clients can be configured to automatically install the updates or to notify the user, like the normal update service does.
Clients
can be configured to automatically reboot when the updates are applied
or to be rebooted manually. (Thus, you can fully automate SUS so that
patches are automatically downloaded from Microsoft, distributed to the
clients, installed, and the clients rebooted without manual
intervention—or with intervention as desired.)
SUS works across domain boundaries using the HTTP service.
The SUS server can be managed from any computer via a browser by specifying the server name in the format http://servername/SUSAdmin, where servername is the name of the SUS server.
Works on DCs or servers.
It's free!
Some of the drawbacks include
It's free (you get what you pay for).
There's
no good way to determine whether the updates worked or not. You have to
drill down in the event logs of the client to determine whether they
were applied.
There's no way to report
which clients have been updated. You can put the patches on the
machines, but you don't know whether they have been applied.
Still
requires a lot of manual intervention. It's still a long way from what
Administrators really need and have been begging for—an automated way to
determine vulnerabilities in the system and to apply the patches
proactively.
Although the SUS made life somewhat easier in patch
management, it's not the answer Administrators are looking for. The
better solution is the WUS, which is in beta at this writing.
Windows Update Service (WUS)
Because this product is in beta at this writing,
there is not a lot of detail on how it works or actual deployments. I
have summarized some of the features that Microsoft is promising. Make
sure you check Microsoft's Web site for details after WUS is released.
One big change is the addition of the Microsoft Update (MU) service. SUS
used the Windows Update (WU) service, but this service only included
Windows OS updates. MU hosts services that host all Microsoft updates
for all Microsoft products. Note that WUS get updates from MU.
The WUS takes a big step in enterprise patch management with the following features:
An SQL (Structured Query Language) database or MSDE (Microsoft Data Engine) holds all data other than content.
Uses .NET Framework.
Scriptable through exposed APIs (Application Program Interfaces) for server and client.
Manages all Microsoft product patches—not just Windows.
Can configure to manage other products' patches.
Can build hierarchy of WUS servers.
Easier to configure than SUS.
WUS Client Automatic Updates are controlled by policy.
Built-in security features.
Validates all downloaded content for Microsoft certificates.
All content download locations are secured by ACLs.