2. Leveraging MAK activation
When KMS activation doesn't meet your needs,
Multiple Activation Key (MAK) activation can be used. MAK activation is
similar to retail product activation in that each workstation must be
activated against the Microsoft activation server. This process may be
performed over the Internet or the phone.
The primary advantage to MAK activation is that
it is relatively permanent. After a computer is activated using a MAK,
clients are not required to reactivate at regular intervals. In fact,
the only time reactivation should be necessary is after significant
hardware or driver updates or after reinstallation of Windows.
With permanent activations, users can create
images of the workstations after activating Windows, which bypasses any
activation or validation procedures. To prevent this, Windows keeps
track of the hardware on which it is installed. If a significant number
of components change, then reactivation is required. Although the intent
is to identify when the hardware has been changed, updating drivers can
also cause a change to be detected. Each hardware component is assigned
a weight. If the total weight of changed components reaches 25, then
the computer must be reactivated. Table 1 shows the indexed hardware components along with their corresponding weights.
Table 1. Understanding Weight Values for Triggering Reactivation
| Hardware Component | Weight |
|---|
| Physical System Hard Disk Drive Serial Number | 11 |
| BIOS Identifier | 9 |
| Processor | 3 |
| IDE Adapter | 3 |
| SCSI Adapter | 2 |
| MAC Address | 2 |
| Audio Adapter | 2 |
| RAM Amount (i.e. 0-512 MB, 512 MB-1 GB, etc.) | 1 |
| Display Adapter | 1 |
| CD/DVD Drive | 1 |
Reviewing the limitations of MAK
Using MAK activation has its disadvantages as
well. The primary disadvantage of MAK activation is that it uses an
activation pool for each MAK issued.
When you purchase volume licenses and receive a
MAK, Microsoft creates a pool of activations associated with your MAK.
Although this number is loosely based on the number of volume licenses
you purchase, it also is related to the licensing agreement you purchase
them under. After the pool has been created on Microsoft's activation
servers, you may activate computers with the corresponding MAK. Each
activation decreases the pool count by one. The most notable implication
here is that even reactivations will decrease the count by one.
Therefore, if you frequently reload your computers, which will in turn
require them to be reactivated, your activation pool may quickly become
depleted.
However, there is not a one-to-one relationship
between your activation pool and the number of licenses you purchased.
In addition, the activation pool may be increased at any time by simply
contacting Microsoft Activation. MAK activation is not intended to
ensure that each activation represents a legal copy of Windows. Instead,
it ensures that businesses and organizations are aware of the number of
activations they are performing. In turn, it would be much more
apparent if a key were to be leaked to the outside world or if it were
being used inappropriately by unscrupulous staff members. If you
legitimately reactivate computers very frequently, this can become quite
a hassle, however. In this case, it is usually best to implement KMS
activation.
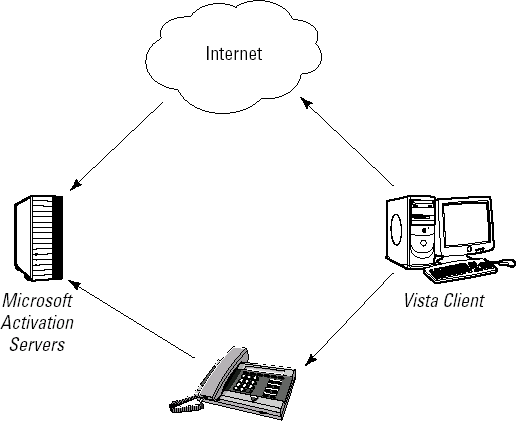
The actual activation process for MAK activation can be performed by two methods, depending upon your network design. Figure 3
shows an example of independent MAK activation. Independent activation
will be performed automatically if a MAK is used for installation and an
Internet connection can be established. Otherwise, independent
activation may be performed over the telephone. As the size of the
network grows, phone activation becomes increasingly unpopular and
ineffective.
In some environments, Internet access may not be
directly available and phone activation may not be practical. If the
environment contains at least 25 workstations, KMS activation is
typically preferred. If, however, there are not at least 25 workstations
or MAK must be used for other reasons, proxy activation may be
performed for MAK clients, as shown in Figure 4.
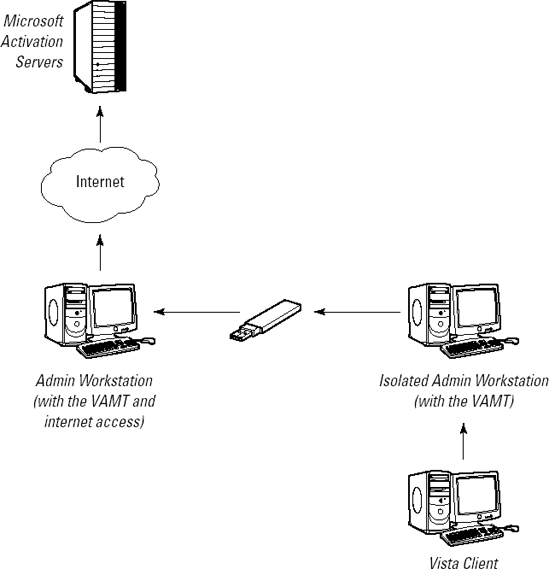
To perform MAK proxy activation, the Volume
Activation Management Tool (VAMT) is used. In proxy activation, the
computer requiring activation generates a request that can then be
passed on to Microsoft as a completely separate process. This feature
eliminates the need for direct Internet access by the clients and
eliminates the need to place a phone call for each workstation to be
activated.
3. Comparing KMS and MAK activation
Licensing can be confusing, and there are
several pros and cons to both the KMS and MAK approaches to activation.
To help you make a decision, we've included Table 2, which highlights the differences between MAK activation and KMS activation.
Table 2. Comparing KMS and MAK Activation Methods
| KMS Activation | MAK Activation |
|---|
| Clients use the default installation key | Clients must use a MAK installation key |
| Only the KMS server is activated with Microsoft | Each client is activated directly with Microsoft unless the VAMT is used |
| 25 physical client minimum to implement for Vista, and 5 for Windows Server 2008 | No minimum number required |
| No activation pool to manage allowing unlimited reactivations | Activation pool managed by Microsoft |
| Each activation is valid for 180 days | Activations are not time limited |
| DNS or manual client configuration is used to locate the KMS server | Internet access, a phone call or the VAMT is used for activation |