Microsoft, as the provider of Windows,
offers several tools and guidelines to secure the information your
systems host as well as securing the systems themselves. One excellent
example is the Windows Vista Security Guide. It offers a structured way
for you to further protect your systems beyond the base protections
enabled when you install Windows. However, securing a computer system is
more than just applying a set of configurations to the system; it also
involves a comprehensive administrative outlook on how systems are used
and how people are responsible for them.
Microsoft has gone the extra mile to protect
their systems just because they are so often under attack. In fact, one
of the most important efforts Microsoft has made in terms of security
with Windows Vista is to submit the operating system for evaluation
against industry standards for security. One of these is the Common
Criteria. Vista has been evaluated against the Common Criteria and has
passed this security evaluation. Organizations that have very tight
security requirements, for example, the Federal Government, can rely on
Vista's built-in security features to create highly secure environments.
Of course, this level of security is not for everyone, but it is
comforting to know that should you require it, you can secure your
systems thoroughly.
Vista also supports Federal Information
Processing Standard (FIPS) approved cryptographic algorithms to secure
client/server communications. For even tighter security, Vista
implements the Suite B cryptographic algorithms defined by the U.S.
government. Because of this, it supports data encryption, digital
signatures, key exchanges as well as hashing, which can let third-party
vendors create more comprehensive security solutions.
Security deals with almost every single aspect of
your network. The ultimate goal of your security strategy should always
be to protect the information that is stored on your systems. Sometimes
this information is the information that makes your organization run;
other times, it is your own personal information you want to protect at
all times.
Your security strategy should aim to cover the following aspects of computer activity:
Each person that enters your network must be identified.
Each
person who has access to your organization's premises must be cleared
and you must provide them with only appropriate levels of access once
they are authorized.
Your security
strategy must implement non-repudiation principles, or otherwise make
sure that when someone modifies something it is the person who is
authorized to do so.
Information in your
network must be protected at the appropriate level. For example,
confidential information must be kept confidential at all times.
Information must also be available when it is needed.
Information must have a high degree of integrity.
Network activity must be monitored to some degree so that you know that traffic patterns are approved traffic patterns.
Access to your systems must be audited so that you know who is doing what when.
Your security strategy must be surrounded by the appropriate administrative activities to ensure it is maintained at all times.
Although this list is not comprehensive, it does
identify the type of preoccupation you must have in mind when putting
together your security strategy. In addition, you need to consider the
scope of interaction users will have with your network:
Local: When people log on to a system, they interact with it at the local level.
Intranet:
When people log on to your network, they can interact with all of the
systems that are connected with each other. Most often, users will
interact with servers offering services and may interact with each
other. When the network is internal, it is called the Intranet.
Internet: Users will interact with public systems that may or may not belong to you.
Extranet:
When users connect to your network from outside your premises or when
partners interact with components of your network, they interact with
your Extranet — a network that is under your control, but that is not
part of the internal network.
Whatever its scope, security is an activity (like
all IT activities) that relies on three key elements: people, PCs, and
processes.
People are both the executors and the users of the security process.
PCs represent the technology people use to manage information.
Processes
make up the administrative aspects of the security strategy. They
include workflow patterns, procedures, and standards used for the
application of security.
Each of these three key elements must integrate with the other to create a strong security strategy.
1. Designing a security policy
Begin your security design for Vista with the
design of your security policy. Your policy will encompass several
aspects, but at the very least it should cover every aspect of
computing, each of the different scopes of interaction, and it should be
built upon sound principles and administrative practices. Don't wait
until you are the victim of an attack. Act now so if you are attacked,
you can mitigate the impact.
Look to your business model. Analyze the
processes that make your organization run and identify those that are
critical to its operation. This is much like business continuity. Many
organizations who do not have a business continuity strategy in place
will fail in the event of a major disaster to their datacenter. Although
it won't be PC security that will cause a disaster of this magnitude,
it is through the PC that most malicious attackers have access to your
systems. Consider it as the first point of interaction or the Point of
Access to Secure Services (PASS). This is why it must be secured.
Most organizations will already have some form
of security policy in place, if so; use it as the starting point of the
elaboration of your Vista security strategy. Then update it with new
settings and features. Identify which standards you want to implement;
include both technical and non-technical processes. For example, you
might include technical security parameters when you prepare computers
for delivery to end users. In another instance, you might make sure your
end users never share their passwords with anyone from within or
without your organization. Then, after you have the entire strategy
defined, communicate it to your users and provide continuous security
communications.
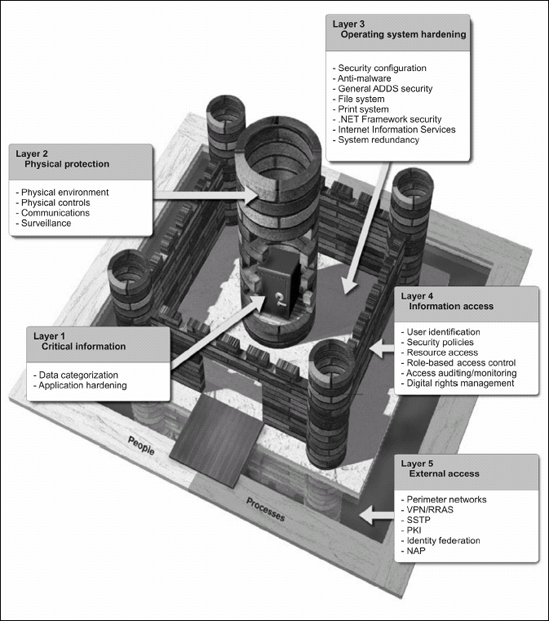
2. Using the Castle Defense System
One good way to make security simpler for
everyone in your organization is to use a security model. For example,
we have been using the Castle Defense System (CDS) security model for
several years now. This model is easy to understand because everyone is
more or less familiar with the concepts inherent in the protection of
medieval castles. Using a descriptive illustration lets you show your
end users, including management, that computer security is a
multilayered activity that does not rest only on your shoulders.
In the days when the world was younger, it was
also more dangerous. To protect themselves and their belongings, people
built castles with multiple layers of protection. There are at least
five different layers of protection in all castles. The first layer is
the moat. It protects the castle by creating a physical barrier to
entry. When the drawbridge is up, no one can enter and when it is down,
only authorized people have access. The second level is the walls
themselves. They are high and cannot be climbed except under duress. On
top of the walls are crenellations that let archers defend from
attackers. The third level is the courtyard; it is designed to let
defenders fend off attackers because it does not offer cover from their
arrows. The fourth level, the castle itself, offers a second massive
layer of defense should the walls be breached. Finally, you have the
vault that is designed to protect the crown jewels from attackers.
This rudimentary description gives a good
impression of how you should defend your own "crown jewels" and ensure
that they are protected at all times. It is a good analogy with which
you can drive home the concept of multilayered security strategies.
When you transform it into a computer protection
mechanism, the Castle Defense System also includes five layers of
defense. In addition, like the castle, you begin the in-depth defense
strategy from within and expand it to cover all aspects of computer
security, as shown in Figure 1.
These five layers include:
Layer 1: Critical Information. Identify what you want to protect.
Layer 2: Physical Protection. Implement some physical level of protection for your offices.
Layer 3: Operating System Hardening. Address the computer systems themselves.
Layer 4: Information Access. Apply controls to the people whom you trust to interact with computers within your network.
Layer 5: External Access. Control how people outside your own domain can interact with your network and the systems it contains.
And because you must work with people, PCs, and
processes, two additional aspects — people and processes — must be
included in the CDS to round out your illustration of a complete defense
and security strategy.
Using this layered approach also makes it easier
to identify what needs to be covered. Of course, before you can design
or review your security strategy, you must have a thorough understanding
of your own organization. You also need to have a good understanding of
the technical components of your IT infrastructure to ensure that you
cover them all.
As far as PC security is concerned, you need to
address each of the five layers with respect to what does apply and what
doesn't apply to these endpoint systems.
NOTE
The Castle Defense System also applies to servers. For information on how to apply the CDS to server infrastructures, look up Windows Server 2008: The Complete Reference by Ruest and Ruest from McGraw-Hill Osborne.
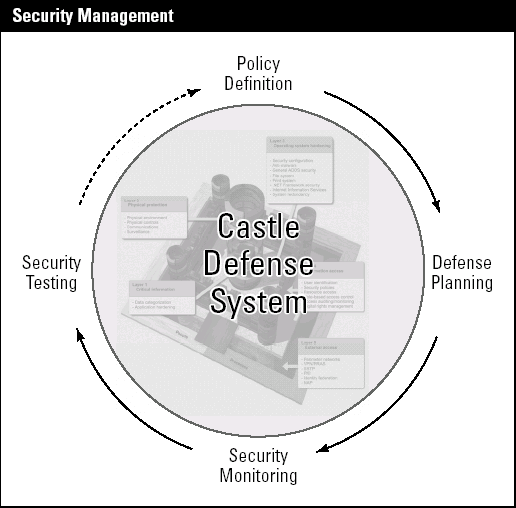
3. Building a security plan
Each security strategy includes a security plan.
The plan must address more than the security policy itself. It must
address how you will manage and update the security policy. In fact, the
plan builds upon the first activity — security policy definition — to
provide you with a complete approach to security. The next parts of the
plan address every day approaches to ongoing security. They include:
Defense planning: Mostly a budgeting and project management activity that ensures you will continue to update your defenses.
Security monitoring: An activity focused on continuous monitoring of your network to ensure nothing untoward is occurring.
Security testing: A final activity that ensures that the protection mechanisms you have in place are appropriate for your requirements.
The security plan and its interaction with the Castle Defense System are shown in Figure 2.
As you can see, it is a continuous cycle that comes back to the policy
definition when complete. If your testing determines that modifications
are required, then you must update the policy, include the update in
your planning, continue to monitor the update, and test it and so on.
Security is never final and must always be an ongoing activity.
One key focus of the security plan is the
understanding of the types of threats you face. Although you may not
face all of the known threats, you will face some; therefore, it is
better to understand as many as possible so that if they occur, you can
to recognize them. Several types of threats exist, including:
Accidental security breach:
This type of threat often occurs because people are just not aware that
they must protect your systems. For example, users from all over the
world give out their passwords to people they trust. The next thing you
know someone is impersonating the user because they have access to their
account. You should make sure your users are aware that they should
never give out their password to anyone.
Internal attack:
Often this attack stems from giving users too much access. This usually
occurs because IT administrators believe that anyone having access to
the internal network is a trusted person. Because of this, internal
resources are not explicitly protected. Therefore, when contractors have
access to your network, they also have access to all of your crown
jewels.
Social engineering attack:
This attack derives from people impersonating someone users will trust.
For example, sending someone a message from the "Internal Help Desk"
and asking them for their credentials is a very common form of social
engineering. Make sure that your users don't fall prey to this type of
attack. Teach them to always call back if they are not sure they are
actually talking to the help desk.
Organizational attack:
This attack is launched from a competitor — one who wants to have
access to your confidential information to gain a competitive advantage
over you and your organization.
Automated attacks:
These attacks are the most common attack type you and your end users
will face. Automated programs scan computer ports at various addresses
until one of them responds. Then, when they get a response, they begin
to identify what type of opening the user has left on. Systems that do
not run personal firewalls are excellent examples of the victims of this
attack type.
Denial of Service (or Distributed Denial of Service) attack:
This threat relies on multiple systems to try to overwhelm a service
you offer. For example, if someone can overwhelm your Domain Naming
Service (DNS), then users may no longer be able to find your
organization on the Web.
Viral attacks:
Viruses or other malicious code is inserted into the organization and
begins to infect systems. This is often due to the fact that
organizations do not run locked down computer environments. When a user
runs with local administrative privileges, anything that can take
control of their machine will automatically have the same privileges.
Locking down systems prevents many of these attacks.
Malicious e-mails and phishing:
These attacks try to fool your users into doing something that will
compromise your systems. The best defense for this type of attack is a
strong offence: make sure your users are educated and won't fall prey to
stupid gimmicks.
Although they do not all apply to the PC, each type of attack must be addressed by your security plan.
4. Using the Windows Vista Security Guide
One of the best resources you can rely on to
secure your PCs is the Windows Vista Security Guide. This guide includes
both textual information as well as tools that help you implement
security on PCs running Vista. It assumes that you are running a network
in an Active Directory (AD) domain and that you have access to Group
Policy to centrally control change on your PCs. It provides a GPO
Accelerator — a tool that can generate either Local or Group Policies to
further protect systems. When using Group Policy, the tool relies on a
specific organizational unit (OU) structure, one where PCs are
categorized according to type and are secured according to role.
No security strategy for Windows Vista is
complete without including contents from this guide. Make sure that you
review it fully and incorporate its recommendations in the security
strategy you prepare for your PCs.
5. Learning Windows Vista security features
Windows Vista includes a host of new features,
many of which are focused on security. In fact, Microsoft's goal with
Vista was to rewrite the Windows code to remove as many security flaws
as possible. Although it is evident that Microsoft's new Trusted
Computing Initiative has borne some fruit, it is almost impossible for
an organization to go over millions of lines of code and remove every
single flaw that it contains, especially when all too many experts are
only happy to prove that they missed something. Despite this, Vista is
much more secure than any other Windows operating system has ever been
and, with the application of its security features in a judicious
manner, you'll be able to make sure breaches of security won't happen in
your network.
New security features in Vista include:
Service Hardening:
Microsoft has reduced the amount of privilege system services include
by default. By creating new, restricted services, Vista will not allow
attackers who take control of a service to perform tasks for which the
service is not designed.
Data Execution Prevention
(DEP): A system which is built into most modern processors. DEP stops
code from using certain memory areas to run malicious software. Vista
integrates directly with DEP to ensure that the famous buffer overrun
flaw is mitigated on the PCs it runs on.
x64 editions:
64-bit editions of Vista also offer more protection than their x86
counterparts. Device drivers must be signed by their manufacturer before
they can be installed. This ensures that it has not been tampered with
from the time it was written to the time you install it. In addition,
x64 systems include PatchGuard, a system that prevents code from
modifying the Windows Kernel and ensures that your system runs as it was
intended.
User Account Control
(UAC): With UAC, everyone runs with a standard user token when using
Vista, even administrators. UAC makes it easier to run locked down
systems because everyone is locked down by default.
The Vista Credential Manager:
This tool powers the logon architecture, removing the older graphical
identification and authentication (GINA) architecture and making it
easier for security providers to integrate to the logon process.
Smart Cards:
The new Credential Manager also makes it easier to integrate Smart
Cards to the logon process and with the new cryptographic service
provider (CSP), the deployment of smart cards is greatly simplified.
Network Access Protection (NAP):
This service is built into Vista from the start. You can use the Vista
NAP client to integrate with either Cisco's Network Access Control or
use a Windows Server 2008 backend to create a full NAP infrastructure.
NAP protects your networks by quarantining systems that do not pass
health status validations. Once quarantined, systems are updated, and
when they have a clean bill of health are allowed access to full network
resources.
Windows Security Center:
This Center provides you with a single integrated control panel for all
things secure. If clearly outlines the status of updates, antivirus,
anti-malware, and other security features on the Vista system.
Windows Defender:
A tool which provides built-in protection for malware including spyware
and rootkits. Defender automatically obtains updates from Microsoft.com and provides one easy way to clean infected systems.
Windows Firewall with Advanced Security:
A tool which lets you completely control the inbound and outbound
connections on any Vista PC. The Windows Firewall can be completely
configured through Group Policy and can provide conditional behavior,
letting you configure one behavior for systems connected to the internal
network and another for systems that are traveling.
The Microsoft Malicious Software Removal Tool: A tool that runs each month on your systems to ensure no malicious software is lurking in its depths.
Internet Explorer version 7:
This version of IE also includes a host of security advancements. Its
Protected Mode automatically reduces its attack surface when surfing on
the Internet. Its ActiveX Opt-In option lets you control the behavior of
unauthorized ActiveX code. Other protections include URL handling and
cross-domain scripting barriers. The new Fix My Settings command lets
users rapidly return to a working IE environment. Also, its new security
status bar lets users immediately know it the site is secure (green) or
if the site is potentially unsafe (red). And the built-in Phishing
Filter lets you know if a site is authentic or not.
BitLocker Full Drive Encryption:
BitLocker lets you protect the entire system on portable computers so
that no content can be stolen in the event of a computer loss.
Rights Management Client: The integrated client also helps protect user data by controlling how others can use the information you create.
The Encrypting File System (EFS): EFS can now integrate with smart cards and provide more complete protection for information stored on any PC.
USB Device Controls:
These settings are managed through Group Policy and allow you to
completely control which devices can be plugged into your Vista systems.
This lets you control who can or cannot use removable disks to copy
data from your network.
Software Restriction Policies:
A tool that lets you control what software is allowed to run in your
network. You should apply this to any software installations or scripts
you want to allow to run in your network and block all other code from
execution.
Temporary and Offline Files:
These files can now be protected through EFS as well as protecting
files while in transit through the Secure Sockets Tunneling Protocol
(SSTP). This means that the contents of folders such as %tmp% and %temp%
is protected at all times, even when the user logs off from the system.
This list includes a series of features that
build on all of the security elements Microsoft put into Windows XP
especially after the delivery of Service Pack 2. These features make it
easier for you to deploy completely secure endpoints.
However, security does not only come
from the client. It must be married with services that are rendered by
servers. These services differ depending on whether your network is
running Windows Server 2003 or 2008. The ideal and most secure
combination is obviously Windows Server 2008 with Windows Vista.
Nevertheless, running a Windows Server system with Vista should give you
access to additional security components.