4. Personal Firewalls: A Layer of Protection from Worms
Because worms spread across networks without
user interaction, antivirus programs that seek to prevent users from
launching viruses do not apply. Defense against worms demands a layered
defense, where the first layer is a good network firewall.
5. Automatic Updates: Remove the Side Doors
In
conjunction with antivirus, antispyware, and personal firewall
software, automatic updates are a critical part of a solid security
strategy because they shut down avenues of attack as soon as they are
discovered. Malware often relies on flaws found in software to work.
These flaws are akin to open side doors to your home that, hopefully,
nobody knows about. There they stand as an open invitation for malware
to walk in. Automatic updates don’t just shut the door; they usually
remove the door entirely and put a permanent wall in its place. You can
enable and configure automatic updates in the Security section in Action
Center. If daily updates at 3:00 a.m. do not suit you, adjust the time
and frequency as you like.
6. Data Execution Prevention
The infamous Internet Worm, launched in 1988 by
then Cornell University student Robert Morris, was the first worm to
publicly demonstrate the risk of buffer overflow attacks. It infected
thousands of systems on the Internet, frustrating military and
university researchers at the time. Modern malware writers continue to
exploit the same type of vulnerability on a much larger scale. The
Internet has grown exponentially, connecting banks, corporations,
government agencies, and private homes. The recent generation of worms,
such as MS Blaster and Sasser, have attracted mass media attention
because they delayed British Airways flights and affected networks from
public hospitals in Hong Kong to the Sydney train system—all made
possible by a single category of security vulnerability.
Buffers are fixed-length memory locations used
to hold data. They can be adjacent to other memory locations also used
to hold data. If a program attempts to write more data into the buffer
than will fit, the remaining data can overflow into the adjacent memory
location and overwrite its previous contents with malicious code. It is
an esoteric task that requires a high degree of skill, but if the
malicious code can then be executed, what was once a fine, upstanding member of the computer community is now, potentially, a minion of evil.
The effects of buffer overflow exploits can be
dramatic and complex, though the root cause, and effective remedies,
have been known for some time. It’s possible to write and compile
computer programs in ways that check and prevent these errors, but
traditional software engineering tools and practices have failed to
address the problem for decades.
New programming tools and conscientious coding
can thwart buffer overflow attacks, but because rebuilding all existing
computer code is impractical, techniques have been developed to mitigate
the risk. Executable space protection techniques, as implemented
through Microsoft’s Data Execution Prevention (DEP), disallow code
execution in areas of memory where it is not expected, and significantly
reduce the threat of buffer overflow attacks. It’s technology with a
proven track record of success. Several critical exploits have already
been proven to fail on DEP-enabled systems—but not all DEP is created
equally.
Modern processors from both AMD and Intel
include hardware-based DEP technology. Windows 7 can take full advantage
of this important security feature, but it will not do so by itself. As
installed, DEP is enabled only for core Windows components. To take
full advantage of DEP for non-Windows programs, you must find the Data
Execution Prevention menu, nestled deep in the user interface, and turn
on DEP for all programs. Microsoft did not enable this setting because
some programs do not work with DEP enabled. This should not deter you
from taking full advantage of DEP because, as shown in Figure 5, there is an exception list, and the trouble is worth the extra security.
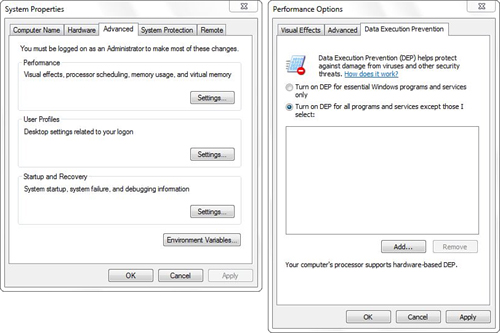
To enable DEP, follow these steps:
1. | Select Start, Control Panel, System and Security.
|
2. | Choose System, Advanced System Settings.
|
3. | On
the Advanced tab of the Performance Options dialog box, click Settings
(under Performance), and then select the Data Execution Prevention tab.
|
4. | Select the Turn on DEP for All Programs and Services radio button.
|
5. | Click OK. In the System Properties dialog box that prompts you to restart your computer, click OK.
|
6. | Close any remaining dialog boxes and windows, and then restart your computer.
|
Hardware
DEP takes advantage of the processor’s inherent security features. Even
if your computer lacks an AMD processor with NX (No Execute) or an
Intel processor with XD (Execute Disabled) features, Windows 7 can still
provide some level of buffer overflow protection using software DEP.
Although not as good as hardware DEP, software DEP has proven effective
against real-world exploits. It can protect the exception-handling
processes in Windows and provides better protection when programs are
built specifically to support software DEP.
Note
In
addition to DEP, Windows 7 uses address space layout randomization
(ASLR) to combat malicious code execution. Without ASLR, key OS
components load in predictable locations that are more easily targeted.
Randomizing the location of executable images adds a new level of
difficulty for would-be exploiters but not for you. This protection
activates and selects new random locations automatically at startup. |