With a minimal investment in
hardware, you can connect two or more computers and form a simple
peer-to-peer network. Because these networks aren't built around a
server, they don't allow you to manage users and shared resources
centrally; instead, each computer contains its own database of authorized user
accounts and shared folders, drives, and printers. Setting up a
workgroup-based network offers the following advantages:
Shared
storage By designating certain folders
as shared resources, you avoid the need to swap files on removable media
or to maintain duplicate copies of files; instead, everyone on the
network can open a shared document.
Shared printers
Sharing a printer allows any authorized network user to print to that
device.
Shared
media You can open shared media files
(music, pictures, and video) stored on another computer or device or
stream media from one computer to other computers and devices on the
network.
Shared
internet connection With a router to which all your networked
computers are connected, every computer can use the router's connection
to the internet. An alternative is to use Internet Connection Sharing
(ICS), with which you can set up internet access on a single computer
and then allow every computer on the network to share that connection.
ICS is an acceptable sharing method if you have a dial-up connection to
the internet; ICS lets you control it from any computer on the network.
However, using a hardware router offers significant security and
performance advantages over ICS and is clearly the way to go if you have
high-speed, always-on internet service, such as that provided by cable
or DSL.
1. What's New
in Windows 7
Networking in
Windows 7 improves on earlier versions primarily with ease-of-use
enhancements. Among the most useful improvements:
HomeGroup makes
child's play of the previously daunting tasks of connecting the
computers in your home and sharing the information they contain. When
you join a home network, Windows automatically invites you to join a
homegroup. Documents, pictures, music, and other files you choose to
share are then accessible among all your home network's computers.
Wi-Fi Protected Setup (WPS), a standard promulgated by the Wi-Fi
Alliance (wi-fi.org) and embraced by many hardware manufacturers,
enables simple and secure configuration of the gamut of wireless network devices, including
routers, wireless access points, computers, printers, cameras, game
consoles, media extenders, and personal digital assistants (PDAs). WPS
is fully integrated in Windows 7.
Mobile broadband support provides a driver-based
system for working with connections to mobile broadband services such as
3G. Instead of
having to install and learn proprietary connection software, you can now
connect a mobile broadband adapter and begin using it in essentially
the same way as any other network adapter.
In addition, Windows 7, when
connected to a server running Windows Server 2008
R2, enables new networking
features such as DirectAccess,
which enables connections to an enterprise server without creating a
virtual private network (VPN) connection; VPN Reconnect, which automatically
re-establishes a VPN connection when internet connectivity is restored;
and BranchCache,
which improves response time and reduces wide area network (WAN) traffic
by caching server content in a local office.
These usability
improvements come atop a major networking makeover in Windows Vista,
which is based on a protocol stack that was completely rewritten for
Windows Vista. Dubbed the Next Generation TCP/IP stack, this
redesign of the network underpinnings provides improvements in security,
performance, and convenience that are largely invisible to ordinary
users.
For example,
additional security comes in the ability of the Windows Filtering Platform to
implement packet
filtering at all levels of the Transmission Control Protocol/Internet
Protocol (TCP/IP) stack. Performance is enhanced by Receive Window
Auto-Tuning, which dynamically determines the optimal receive window
size based on changing network conditions; in previous Windows versions,
you were required to tweak the registry to set a fixed-size receive
window for your type of internet connection. The Next
Generation TCP/IP stack implements Internet Protocol version 6 (IPv6) in
a dual-stack architecture; instead of having to install a separate
protocol (with its own transport and link layers) as in previous
versions, IPv4 and IPv6 are incorporated in a single Windows driver,
with a shared transport layer and link layer. Enabling IPv4 and IPv6 by
default is more convenient for the user who needs both—because there's
nothing extra to install—but also easier for developers. Native support
for wireless devices is built in to the Next Generation TCP/IP stack, which also reduces
demands on developers and users who must deal with add-in support in
earlier versions of Windows.
And if all of the
preceding jargon means nothing to you—well, that's the point.
Improvements like these (and dozens of others) have made networking
almost transparent to users so that you don't need to spend time
understanding how the layers in a protocol stack communicate and, worse,
how to configure them to do so.
2. Using
Network And Sharing Center
Many of the tasks
related to configuring the hardware and software for a network, viewing
network resources, setting up shared resources on your own computer, and
diagnosing network problems can be managed from Network And Sharing
Center, which is shown in Figure 1.
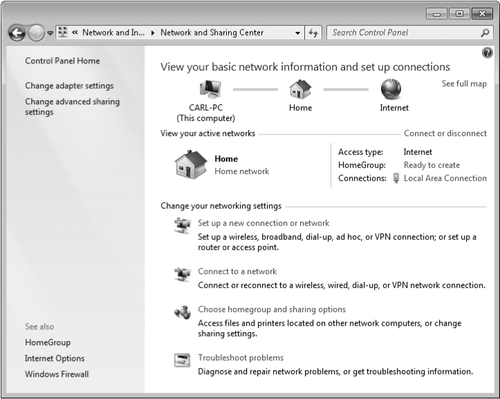
You can open Network And
Sharing Center in any of the following ways:
In the notification
area, click the Network icon and then click Open Network And Sharing
Center.
In the
Start menu search box, begin typing network until Network And Sharing Center appears;
click it.
If your Start menu includes a
Network command on the right side, right-click it and then click
Properties.
In
Control Panel, click Network And Internet, and then click Network And
Sharing Center.
In
Windows Explorer, with the Network folder displayed, click the Network
And Sharing Center button on the toolbar.
Note:
Many of the tasks related to configuring networks
require elevation to administrator
privileges, as indicated by the shield icon next to commands and on
command buttons.
3.
Understanding Network Locations
With computers that
connect to different types of networks—such as a corporate domain, an
internet café, and a private home network—often within the same day and
sometimes even simultaneously, using the same network security settings for all
networks would lead to security breaches, severe inconvenience, or both.
Windows uses network locations to categorize each network and then
applies appropriate security settings. When you initially connect to a
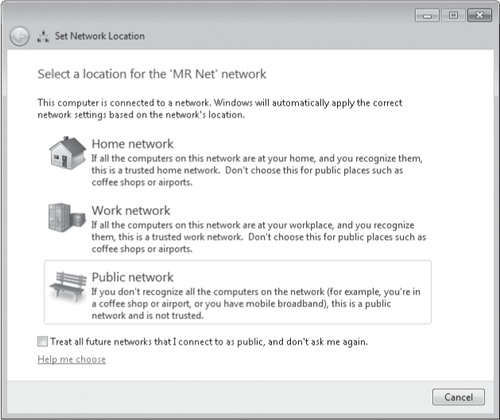
network, Windows asks you to select a network location, as shown in Figure 2. Select one of the three options:
Home Network Select this option when you're connecting to a
trusted network, such as your own network at home. You should select
Home Network only for a network that is protected by a residential
gateway (a term we'll explain shortly) or comparable internet defense,
and one where you're confident that malicious users aren't connected.
With this choice, Windows enables the HomeGroup feature for sharing with
other users on the network.
Work Network Select this option when you're connecting to a
trusted network, such as your company network at work. With this choice,
Windows turns on network discovery, which lets you see other computers
on the network and lets other users see your computer.
Public Network Use this option
for networks in public places, such as wireless hotspots in coffee
shops, hotels, airports, and libraries. This type of network typically
has a direct connection to the internet. Network discovery is turned off
for public locations.
Note:
In Windows
Vista, the Home and Work options are functionally identical; the only
difference is the default icon that Windows assigns to represent the
network. In Windows 7, however, there is a key difference: only Home networks can use the Home-Group feature.
If you have a mobile
computer that connects to multiple networks, keep in mind that Windows
keeps three groups of network security settings: one for private (home or work)
networks, one for public-location networks, and one for use when your
computer is joined to a domain-based network. A visit to Windows
Firewall shows that it maintains three profiles: Home Or Work (Private)
Networks, Public Networks, and Domain Networks; each is associated with a
network location type.
This is important
because, for example, when you are connected to a public network and
Windows Firewall is turned on, some programs and services ask you to let
them communicate through the firewall. Consider carefully whether you
want to unblock such programs; if you do, that program is unblocked for
all networks identified as "public location" networks.
The location of the current
network is shown in Network And Sharing Center, below the name of the
network.
To change the
network location, in Network And Sharing Center, click the link that
identifies the network location. In the dialog box that appears (same as
in Figure 2), click the appropriate location.
|
Computers on a network can
be part of a workgroup or a domain.
In a workgroup,
the security
database (including, most significantly, the list of user accounts and
the privileges granted to each one) for each computer resides on that
computer. When you log on to a computer in a workgroup, Windows checks
its local security database to see if you've provided a user name and
password that matches one in the database. Similarly, when network users
attempt to connect to your computer, Windows again consults the local
security database. All computers in a workgroup must be on the same
subnet. A workgroup is sometimes called a peer-to-peer
network.
By contrast, a domain consists of computers that share a security
database stored on one or more domain controllers running Windows
Server. When you log on using a domain account, Windows authenticates
your credentials against the security database on a domain controller.
|