Name
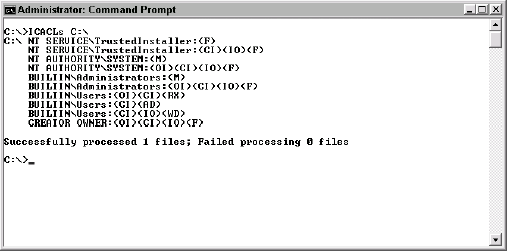
Provides the name of an ACL to work with when using the ICACLs utility. For example, if you type ICACLs C:\ and press Enter, you'll see the Discretionary Access Control List (DACL) for the root folder of the C drive. Figure 1 shows typical output from this command. The /Grant
command line switch explains the meanings of the letters after each
user or group entry. Notice that some entries appear twice. For example,
the Administrators group has modify access (M) in the first entry and
object inherit (OI), container inherit (CI), inherit only (IO), full (F)
access rights in the second. The first entry shows the Administrators
group rights to the current folder, while the second shows the
Administrators group rights to subfolders and files.
/Save
Stores all of the ACLs for the matching names into an ACL file for later use with the /Restore option. For example, if you type ICACLs C:\ /Save MyAcls.TXT and press Enter, you'll save all of the DACLs for the root directory of the C drive to a file named MyAcls.TXT.
ACLFile
Provides the name of a file used to store all of the ACLs.
/T
Changes the ACLs of the specified files or directories in the current directory and all subdirectories.
/C
Ignores access denied errors by moving to the next file or next action.
/Q
Performs the task in
quiet mode. The utility doesn't display any success messages. You'll
normally use this feature in a batch file to ensure the batch file user
isn't bothered by messages. However, you won't want to use this feature
while testing your batch file or performing tasks manually because this
command line switch hides important status messages.
/L
Processes the ACLs of a symbolic link, rather than the symbolic link's target.
Directory
Defines a directory used to perform a task.
/Substitute
SidOld SidNew [...]Specifies that the command should substitute an old Security Identifier (SID) with the value of a new SID.
/Restore
Restores the content of an ACL file to either an old or new SID.
/SetOwner
Changes the owner of the specified items.
User
Defines the name of a user who is the subject of a particular task.
/FindSID
Locates all of the names that contain an ACL that mentions the specified SID.
SID
Specifies an SID
to used to perform a task. The SID may appear in either friendly name
form or numerical form. Append an asterisk (*) to the beginning of the
SID when you use the numerical form.
/Verify
Locates all of the
files that have security problems. The two specific checks verify that
the file doesn't have an ACL that isn't in canonical form and that the
ACL lengths are consistent with ACE counts. The ICACLs utility preserves
the canonical order of the ACEs within an ACL. It follows this form:
Explicit denials
Explicit grants
Inherited denials
Inherited grants
/Reset
Replaces any custom
file ACLs with the default inherited ACL. This action resets the file's
security to a known state of accessibility.
/Grant[:r]
SID:PermissionGrants the specified user the rights defined by the combination of an SID and associated permission. When you include the :r
argument, the granted rights replace those the user currently holds.
Otherwise, the new rights are in addition to those that the user already
possesses. The Permission variable is
actually a mask that you can specify in one of two forms: simple and
specific. You can't mix the types in a single use of the utility. Here's
the list of simple rights that you can assign.
Here's a list of the specific rights that you can assign.
D (delete)
RC (read control)
WDAC (write DAC)
WO (write owner)
S (synchronize)
AS (access system security)
MA (maximum allowed)
GR (generic read)
GW (generic write)
GE (generic execute)
GA (generic all)
RD (read data/list directory)
WD (write data/add file)
AD (append data/add subdirectory)
REA (read extended attributes)
WEA (write extended attributes)
X (execute/traverse)
DC (delete child)
RA (read attributes)
WA (write attributes)
When working with
directories, you may also assign inheritance rights to the security
settings. Inheritance rights apply to either simple or specific rights.
Here's the list of inheritance rights.
/Deny
SID:PermissionDefines the
specified user the rights defined by the combination of an SID and
associated permission. When the system adds the specified deny ACE, it
also removes any associated grant ACE that may appear in the user's list
of rights. See the /Grant command line switch for an explanation of permissions.
/Remove[:[g|d]]
SIDRemoves all occurrences of the specific SID within an ACL. When you add the :g argument, the system removes all grant ACEs associated with the SID. When you add the :d argument, the system removes all deny ACEs associated with the SID. The default action removes both grant and deny ACEs.
/SetIntegrityLevel
Level[...]
Adds an integrity ACE
to all of the matching files. You specify the integrity level as L
(low), M (medium), or H (high). This option also accepts the inheritance
options of CI (container inherit) and OI (object inherit) when working
with directories.