The Microsoft Baseline Security Analyzer (MBSA) is
one of the tools you can use to audit security on systems in your
network. It checks for updates and for various security vulnerabilities.
|
One of the core
principles of hardening any computer is keeping it up to date. If a
computer isn't up to date with security updates, it can be vulnerable to
any attack that exploits the vulnerabilities that the updates are
trying to resolve.
|
|
Figure 1
shows the first screen you'll see when launching the MBSA. Although the
title bar shows it as version 2.1, the introductory text states that it
includes support for Windows 7, indicating that it is version 2.1.1.
MBSA 2.1.1 was released to support Windows 7 clients. It can run on and scan any of the following clients:
Windows 2000
Windows XP
Windows Vista
Windows Server 2003
Windows Server 2003 R2
Windows Server 2008
Windows Server 2008 R2
After you've run at least a
single report, the View Existing Security Scan Reports link will be
enabled, allowing you to view past reports. If you click this link,
it'll provide a list of all the reports that have been run. This list
includes the computer name, the IP address, the overall assessment of
the scan, and the date when it was run.
1. Picking Computers to Scan
You can run MBSA against a
single computer or multiple computers in a network. When you choose to
scan a single computer, you'll see a screen similar to Figure 2. You can identify the computer to scan based on the computer name or its IP address.
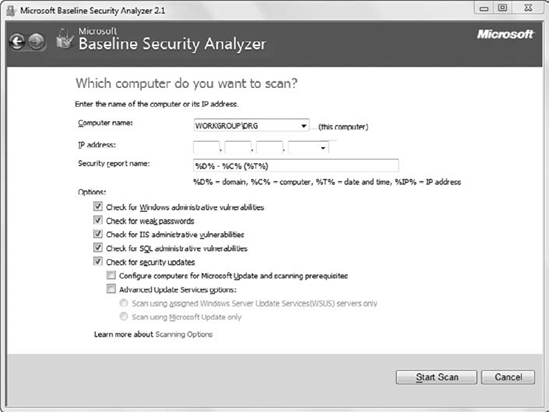
You'll need administrative
access to scan any computers using MBSA, so if you're scanning remote
computers, you should be logged on with an account that is in the remote
computer's Administrators group.
|
When running MBSA in a domain,
you should use a domain account that is added to the Administrators
group of the desktop computers. Most organizations create a group that
is automatically added to the local Administrators group on desktop
computers that desktop support personnel manage.
|
|
If you instead click the Scan Multiple Computers link of MBSA, you'll see a display similar to Figure 3. You can choose to scan all the computers in a domain or all the computers in a range of IP addresses.
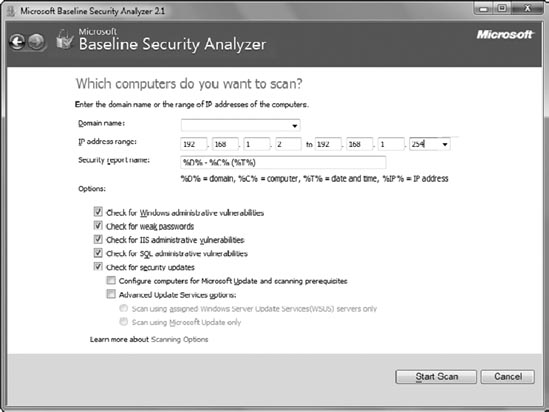
In the figure, I added the IP
address range of 192.168.1.2 to 192.168.1.254 to scan all the computers
in this subnet. I omitted 192.168.1.1 because it is the address of the
router in this network and not a Microsoft computer. MBSA will then
connect to the specified computers and inspect them for installed
updates and other security issues.
When MBSA is run, it will first connect to a Microsoft website to download the MBSA detection catalog (wsusscn2.cab).
This catalog includes information about all available updates and
security vulnerabilities. It is used to compare the existing updates and
configurations on individual clients with a list of security updates
that have been released along with known vulnerabilities. If the catalog
has already been downloaded, MBSA will check to be sure it is up to
date.
NOTE
You can download the wsusscn2.cab catalog directly from Microsoft's site using this link: http://go.microsoft.com/fwlink/?linkid=76054. This file can then be centrally located and used with the /catalog switch when using MBSACLI (the command-line equivalent of MBSA).
The previous version of the cabinet file was named wsusscan.cab and is still available. However, wsusscan.cab has not been updated since March 2007 and doesn't include updates and security vulnerabilities since then. You need to use the wsusscn2.cab file to ensure that you are checking against the most recent data.
2. Vulnerability Checks
MBSA will scan computers
for several security issues. It uses Windows Management Instrumentation
queries to inspect the system for the following vulnerabilities:
Check for Windows Administrative Vulnerabilities
MBSA inspects the system
for basic security issues such as whether more than one user is a member
of the Administrators group, the Guest account is enabled (it should be
disabled), NTFS is used on all the drives, and any folders are being
shared.
Check for Weak Passwords
MBSA checks for blank or
weak passwords on each local account on the system. A strong password
will have at least eight characters and use a combination of at least
three of the four character types (uppercase, lowercase, numbers, and
symbols).
Check for IIS Administrative Vulnerabilities
This check looks for
vulnerabilities in Internet Information Services (IIS) versions 5.0,
5.1, and 6.0. It also checks to see whether the IIS Lockdown Tool has
been run on these versions. If IIS is not installed on the scanned
system, this check is skipped.
Check for SQL Administrative Vulnerabilities
This check looks for
vulnerabilities in both SQL Server instances and the Microsoft Data
Engine (MSDE) that is installed on any scanned computers. If SQL Server
or MSDE is not installed on the system, this check is skipped.
Check for Security Updates
This check scans all
systems to determine whether all current security updates are installed.
It uses the same technology that is used by WSUS and SCCM to scan the
computers. However, if your network is not using WSUS or SCCM, this is a
valuable tool to determine easily whether clients are up to date. A
green check indicates that no missing security updates were identified.
Missing updates are marked with a red X, and missing service packs or
update rollups are marked with a yellow X.
|
The easiest way to verify that unmanaged
clients have installed updates is by using MBSA. Clients managed by
WSUS or SCCM will be checked using those tools, but if clients aren't
being managed by WSUS or SCCM, they can be checked with MBSA.
|
|
The security updates check gives you several additional options, including these:
Configure Computers for Microsoft Update And Scanning Prerequisites
If a client doesn't have
the Windows Update Agent installed, it can't be scanned. However,
selecting this setting allows you to install the Windows Update Agent
and other prerequisites automatically on the target computers so that
they can be scanned.
Advanced Update Services Options
Two additional update
services options are available for clients that are configured to
receive updates from WSUS servers. If your environment is not using
WSUS, these settings won't be used.
Scan Using Assigned Windows Server Update Services (WSUS) Servers Only
This option can be used
in an environment where WSUS is being used. It will scan only computers
that are configured to receive updates from WSUS servers.
Scan Using Microsoft Update Only
This option allows
you to compare clients against the list of updates available from
Microsoft instead of the list of updates that have been approved on the
WSUS server.
MBSA provides a report on the
findings for each scan. Reports include information on any issues that
are found and also provide instructions on how to fix any of the issues.
Figure 4
shows a sample report with the Windows Scan Results showing. If you
look at the vertical scroll bar on the right side of the window, you can
see that there is a lot more to this report.
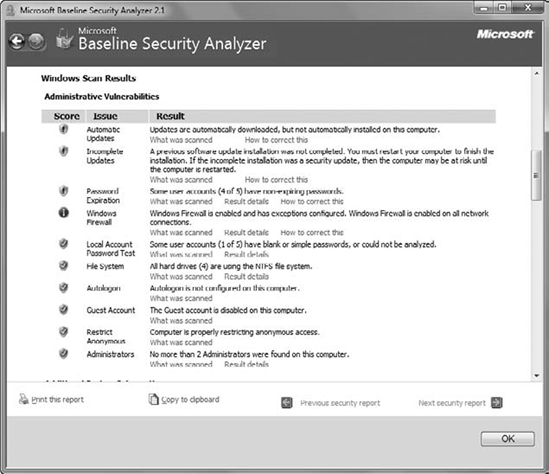
The report shows three different
icons referred to as risk scores. The orange shield icon with an
exclamation mark generally indicates that action is required to secure
your system. You may also find a red shield icon, which indicates a
severe risk.
Orange shield with exclamation mark
This indicates a risk
that should be addressed. In the figure, it shows that automatic updates
are not set to be installed automatically (requiring user action), an
update is not complete and is pending a reboot, and four out of five
accounts have non-expiring passwords.
Blue circle with exclamation mark
This generally
indicates a best practice and not necessarily a security issue. An
exception for a firewall allows certain traffic through. The firewall
should be enabled and that's the most important setting, but it is often
acceptable and even necessary to enable exceptions.
Green shield with check mark
This indicates that MBSA checked for the vulnerability and found the system compliant.
Red shield with an X
This indicates a known
security update, service pack, or update rollup is not installed. In
addition, if Automatic Updates is completely disabled, it will show up
with a red shield.
By clicking Result Details
in the report for any of the issues, you can see additional data that
can tell you what to do. As an example, Figure 5 shows the result details for the issue related to user accounts having non-expiring passwords.
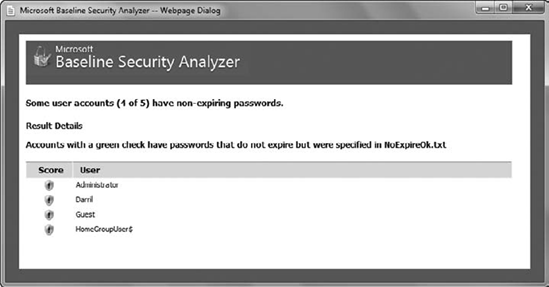
You can drill into the details of any of the report issues and determine exactly what the problem is and how to resolve it.
3. Installing MBSA
MBSA is a free download available at Microsoft's download site (www.microsoft.com/downloads)
by searching for "MBSA 2.1.1." You should download at least version
2.1.1 to support Windows 7. Versions exist for both x86 (32-bit) and x64
(64-bit) systems.
Browse to where you've downloaded the MBSA, double-click it, and click Run. If prompted by User Account Control, click Yes to continue. Review the information on the Welcome page and click Next. Review the license agreement, select I Accept the License Agreement, and click Next. Accept the default destination folder and click Next. Click Install on the Start Installation page. When the installation completes, click OK.
|
4. Running the MBSA
The first time it is run, it may take some time to connect to Microsoft's site to download the wsusscn2.cab file, which includes the catalog of security update information. Later, it only checks to see if the version is up to date.
Click Start => All Programs => Microsoft Baseline Security Analyzer to launch MBSA. If prompted by User Account Control, click Yes to continue. It will default to the selection of your computer. Review the options, and accept the default settings. Click Start Scan. After
a moment, the scan will complete and the report will appear. Review the
report, and investigate any issues that are reported.
|
5. Running the MBSACLI
When you install the MBSA, the
MBSA command-line interface (MBSACLI) will also be installed. The great
strength of the MBSACLI is the same as with any command-line tool: It
can be scripted, and anything that can be scripted can be scheduled.
You could
create a batch file to run MBSACLI on all the computers in your domain
or on all the computers within a specific subnet. You can then schedule
this batch file to run every Sunday night. When you come in to work on
Monday, you'll only need to check it. If you want to get fancier, you
can include a script to send the output to your email address or the
email address of a group of administrators.
5.1. MBSACLI Location
The Mbsacli.exe file is located in the \Program Files\Microsoft Security Baseline Analyzer 2\ folder when MBSA is installed. You need to specify this path when executing MBSACLI.
Just as MBSA must
be run with administrative permissions, MBSACLI also needs
administrative permissions. When running the command from the command
prompt, launch it with administrative permissions by right-clicking
Command Prompt and selecting Run as Administrator.
As a simple way to see MBSACLI in action, you can execute the following command:
"C:\Program files\Microsoft Baseline Security Analyzer 2\mbsacli" i
/target localhost
NOTE
Even though the previous code is shown on two lines it should be entered on a single line.
Since the path and command contain spaces, they must be enclosed in quotes. The /target switch is used to identify the computer to check. Localhost is resolved to the computer from where it's run using the host file (located at C:\Windows\System32\Drivers\etc\).
NOTE
The /target switch is useful when running MBSACLI against a remote computer. However, it can be omitted. If MBSACLI is run without the /target switch, MBSACLI will run on the local computer.
Some of the common switches used with MBSACLI are shown in Table 4.1.
As with any command-prompt tool, you can redirect the output to a text
file using the redirect symbol (>). For example, the following
command runs the same report as shown in the previous command but
redirects it to a text file named mbsacli.txt.
"C:\Program files\Microsoft Baseline Security Analyzer 2\mbsacli"
/target localhost > mbsacli.txt
NOTE
Even though the previous code is shown on two lines it should be entered on a single line.
Table 1. MBSACLI switches
| Switch | Description |
|---|
| /target | Use this to identify the target computer where MBSACLI will run. You can specify the target as a hostname or an IP address.
Mbsacli /target 192.168.1.10 |
| /r | Use this to specify a range of IP addresses. Both the beginning IP address and the ending IP address are specified.
Mbsacli /r 192.168.1.10-192.168.1.20 |
| /listfile | You
can create a file with a list of computers or a list of IP addresses
and then direct MBSACLI to run the command against all the computers in
the list. The following command assumes a file named computers.txt exists in the current directory.
Mbsacli /listfile computers.txt |
| /d | Use
this to specify the domain name in which to run MBSACLI against all
computers in the domain. The domain name needs to be expressed as a
NETBIOS name (single name). For example, if the domain name is wiley.com, it should be expressed as wiley, not wiley.com.
Mbsacli /d wiley |
| /n | You can use the /n option to exclude specific tests. Valid options are OS, SQL, IIS, Updates, and Password. You can exclude more than one option by adding the + with no spaces. The following command will run the check on the local system and exclude the SQL and IIS checks.
Mbsacli /target localhost /n SQL+IIS |
| /nd | This
switch can be used to tell MBSACLI to not download any updates from the
Internet. It will just use the current version of the cabinet files. |
| /wa | This
specifies that only results that have been approved on the WSUS server
should be checked. Append this switch to commands that scan the domain
or a range of IP addresses. |
| /wi | This
specifies that all updates should be checked even if not approved by
the WSUS server. Append this switch to commands that scan the domain or a
range of IP addresses. |
| /u | You can specify a specific user name to use to perform the scan. |
| /p | When specifying a user name, you must also provide a password with the /p switch. |
| /catalog filename | You can specify the location of the wsusscn2.cab file using the catalog
switch. This is useful if you've downloaded the cabinet file and stored
it in a central location (such as a share on a server) and mapped the
share.
Mbsacli /catalog z:\wsusscn2.cab |
| /nvc | The no-version-check switch will prevent MBSA from checking to see if a newer version is available. It is often used with the /catalog switch.
Mbsacli /catalog z:wsusscn2.cab /nvc |
| /ia | This switch will update any prerequisite Windows Update Agent components during a scan and is also often used with the /catalog switch.
Mbsacli /catalog z:wsusscn2.cab /nvc /ia |
| /l | This
shows a list of reports available on this system. The output list
includes Computer Name, IP Address, Assessment, and Report Name columns.
The Report Name column can be used to identify report names that are
needed for other list switches such as the /lr and /ld switches.
Mbsacli /l |
| /ls | This shows a list of reports available from the most recent scan.
Mbsacli /ls |
| /lr | This displays an overview of a specific report. The report name must be used and can be determined with the /l switch.
Mbsacli /lr reportName |
| /ld | This displays a detailed output from a specific report. The report name must be used and can be determined with the /l switch.
Mbsacli /ld reportName |
|
Microsoft has created a
free download that includes several sample scripts you can use to
accelerate your learning and use of the MBSACLI. The current version is
called mbsa2samples.exe and can be located on Microsoft's download site (www.microsoft.com/downloads) by searching for "MBSA scripts." Just be aware that any script that references the wsusscan.cab file needs to be modified to use the wsusscn2.cab file (or the wsusscn2.cab file needs to be renamed as wsusscan.cab). The older wsusscan.cab file has not been updated since March 2007.
|
|
5.2. Running in an Isolated Environment
It is possible to
run MBSACLI in an isolated environment that doesn't have access to the
Internet. For example, you may be running Windows 7 in a VPC machine
used for testing, or you may have an entire network that is completely
isolated from the Internet for security reasons. When running MBSACLI in
an isolated environment, you'll need to take a couple of extra steps:
If the wuredist.cab file is not copied to the appropriate folder, MBSACLI will return the following error: The catalog file (Wuredist.Cab) is damaged or an invalid catalog. Once these steps are taken, you can then run MBSACLI with the /catalog switch to point to the location of the file. It's also common to include the /nvc, /nd, and /ia switches. Assuming the wsusscn2.cab file is located in the c:\mbsa
folder, you could use the following commands. The first command changes
the directory to where MBSACLI is located, and the second runs it with
the appropriate switches for an isolated environment.
CD "C:\Program files\Microsoft Baseline Security Analyzer 2\mbsacli"
Mbsacli /catalog C:\mbsa\wsusscn2.cab /ia /nvc /nd