Software developers have been battling software
counterfeiting (often called pirating or software piracy) since the very
first operating system or application was sold. When it's easy to copy
the software without paying for it, some people do just that.
Client licenses,
product keys, and activation work together to help ensure that a
software program that is being used is a valid copy. The goal is to make
it more difficult for software counterfeiters to copy and sell the
software to unsuspecting users while also making the process smooth for
users who have purchased valid versions.
With this in mind,
administrators have a responsibility to their company to help it develop
sound licensing strategies and ensure they remain compliant with
license agreements. You should understand the basics of client
activation that can be implemented in an organization.
1. Licensing Strategy and Compliance
Windows 7 uses a product key and an activation process to help thwart counterfeiting. Figure 1
shows the product key screen from the installation process. You can
still install Windows 7 without the product key by clicking Next on the
installation screen, but it won't successfully activate without the key.
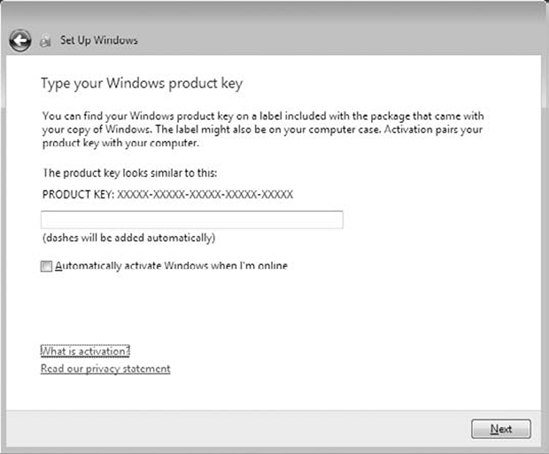
Some product keys are designed
for a single product, and some product keys are designed for multiple
products. A Multiple Activation Key (MAK) uses a single key purchased
for many clients. In larger organizations, MAKs or Key Management
Service (KMS) servers could be used for activation, or a combination of
the two can be used.
Activation will ultimately
be paired with the product key and your computer. The activation process
collects information on the computer to uniquely identify it, but it
does not collect any information on the user.
When installing Windows,
you'll receive the prompt Automatically Activate Windows When I'm
Online. If this box is checked, activation will be attempted three days
after the user logs on the first time. If it is not checked, the user
will be prompted to activate before the grace period expires.
1.1. Windows 7 Activation Grace Period
Windows 7 has a grace period
of 30 days before it needs to be activated. During this time, users will
see a pop-up reminding them they need to activate. This starts as a
once-a-day pop-up four days after the installation and increases to as
often as once an hour on day 30.
On day 31, a message will
appear indicating that you must activate Windows to continue using all
Windows features. A logical question is, "What features can't be used?"
In past versions of Windows, Microsoft introduced a
reduced-functionality mode where users can browse the Internet for one
hour before having to log off and back on again.
At this writing, it appears as
though everything in Windows 7 still works in this reduced-functionality
mode. The desktop background goes black with text indicating the copy
of Windows is not genuine. You can change the background, but it will
change back within about an hour. Periodically, an Activation window
appears, informing you the activation period has expired and prompting
you to activate, buy a new product key online, retype your product key,
or view other ways to activate.
On Windows Server 2008 R2 (the server companion to Windows 7), the server shuts down hourly after the activation period expires.
All of this can be frustrating
when you use a system that isn't activated, but there is a simple
solution—ensure the software is genuine and activate it.
You can activate Windows from
the System page. Click Start, right-click Computer, and select
Properties. If you scroll down to the bottom of the page, you'll see a
Windows Activation menu similar to Figure 2.
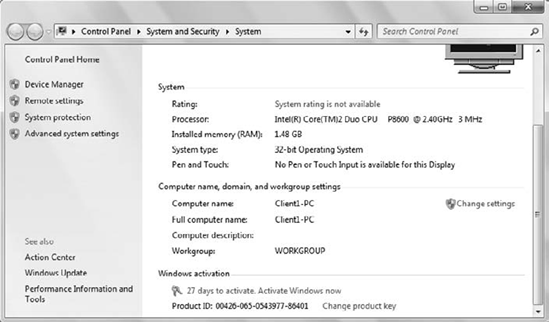
If your system is connected
to the Internet, you can simply click this link. Your system will
connect to Microsoft's servers, some information on your computer will
be transferred back and forth, and a moment later you'll be notified
that activation was successful. Microsoft stresses that the information
transferred during the activation process can be used to identify your
computer, but it does not include any information on the user.
Once the system is
activated, the countdown to activate will be replaced with a message
saying, "Windows is Activated." Windows activation is considered
permanent, although Windows does periodically check to ensure that the
system is the same.
1.2. Detecting Changes
Periodically, Windows 7 will
verify that the copy of Windows is valid and is operating on the same
system where it was originally installed. If significant changes are
detected, the activation will be reversed and the system will need to be
reactivated.
The most common scenario
where this occurs is when imaging software such as Symantec's Ghost is
used. It is possible to make an image copy or clone of a system and then
use this cloned copy on other computers. The license for the original
system wasn't purchased for the other computers, and Windows 7 will
detect that the operating system that was activated on the original
system is now located on a different computer. Once the change is
detected, activation will be revoked and the client will need to be
reactivated.
This can also occur if too
many changes are made to the hardware of a system. For example, if the
motherboard of a system is replaced, Windows 7 may assume it's been
moved to a different computer. This can usually be resolved with a phone
call to a Microsoft help center to obtain a new key.
NOTE
Cloning systems can
also result in duplicate security identifiers (SIDs). To prevent
duplicate SIDs on a network, the Sysprep program is run before capturing
the image. Sysprep sanitizes
the system by removing unique information such as the computer name and
SIDs. It also resets the licensing information used for activation,
requiring computers receiving the image to be activated separately.
2. Software Manager Licensing Manager Tool
The Software Licensing Management Tool is a built-in Visual Basic script (slmgr.vbs)
program that can be used for licensing and activation tasks. It
includes several options that are entered as a switch. Some of the
options directly relate to the clients (and are covered in this
section), and some of the options directly relate to KMS.
The slmgr tool must be run from an elevated command prompt. Click Start => All Programs => Accessories, right-click Command Prompt, and select Run As Administrator.
2.1. Reset Grace Period
You can extend the initial 30-day grace period using the slmgr /rearm
command. In other words, if the 30-day grace period has expired, the
background has gone black, and the reminder screens are coming up
hourly, you can execute this command at the command prompt to give
yourself another 30 days. This command can be executed three times.
|
The Windows 7 activation limit can be extended to a total of 120 days. When the 30-day limit is reached, you can run slmgr -rearm
from an administrator command prompt, which resets the activation limit
for another 30 days. This command can be executed three times. Thus, if
it is run at the end of each 30-day period, you'll get a total of 120
days.
|
|
2.2. Activate Windows
You can use slmgr /ato
command to cause the system to activate right away. As a reminder,
activation won't normally be done until three days after the user first
logs on. If you are building computers that you'll move to an isolated
environment without Internet access, you can use this command to force
activation right away.
2.3. Display License Information
The slmgr /dli command
can be used to display information on the license used for this system.
When executed, it will show the name, description, a partial product
key, and the license status of the current license. As an example, Figure 3 shows what it looks like on one of my systems:
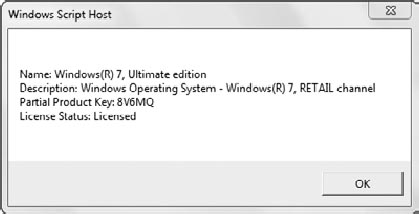
You can also execute it as slmgr /dli all
to display information on all licenses on the system. Other licenses
will indicate they are not in use and the status is Unlicensed.
2.4. Install Product Key
The slmgr /ipk <Product Key>
command can be used to install a new product key. This can be useful if
the system is configured to use a KMS but you want to switch it to use a
MAK.
2.5. Display Detailed License Information
You can use the slmgr /dlv
command to get more detailed information on the license. The result
includes several identification numbers and certificate URLs. It will
also show the status of the license and the remaining rearm count.
2.6. Expiration Data for Current License
The command slmgr /xpr
can be used to indicate the expiration date for the current license. If
the system has not been activated, this will indicate the date and time
when the 30-day grace period expires.
If the license has been
permanently activated, it will say, "The Machine is Permanently
Activated." If the system has been activated by KMS, it will indicate
the expiration of the KMS activation.
3. Volume Activation Methods
For smaller businesses,
Windows 7 is purchased on an individual basis, and the clients are
automatically activated three days after the installation. For larger
enterprises, volume-activation methods are used to activate multiple
clients with a single key. There are two methods of volume activation.
KMS is used when the clients
can't access the Internet and require the use of a KMS server. KMS
requires significantly more administration than other methods of
activation.
As an overview, Table 1
shows some of the comparisons between MAK activation and KMS server
activation. It's important to realize that MAK keys and KMS keys are
different. A MAK key can't be activated with a KMS server, and a KMS key
won't be activated over the Internet.
Table 1. Comparing MAK and KMS
| MAK | KMS |
|---|
| Activation is permanent. | Clients must connect to a KMS server periodically to renew activation. |
| Used when access to the Internet is possible (or manual phone method is desirable). | Used in isolated networks where Internet access is not possible (and manual activation via the phone is not desirable). |
| Can be used for any number of clients. | Requires a minimum of 5 servers, 25 clients, or a combination of 25 servers and clients. |
| Volume Activation Management Tool (VAMT) can be used with a MAK proxy. | Although a KMS server is used, it's not referred to as a proxy. |
| Supports clients duplicated from a single image. | Supports clients duplicated from a single image. |