4. Multiple Activation Key
Large enterprises can
purchase a Multiple Activation Key (MAK), which is a single key that can
be used to activate many clients. For example, a company could purchase
100 licenses using a MAK. This single key is used for the image, and
activation over the Internet is automatic.
A common method used to deploy the operating system to multiple computers is the use of imaging technologies.
MAKs are purchased from
Microsoft partners for a specific number of clients. They should be used
only for these clients and no others.
If your clients cannot
access the Internet, you can use a KMS server. You can also use the Volume Activation Management
Tool with a MAK proxy to activate clients that can't access the
Internet. The most common scenario where clients can't access the
Internet is when they host or access sensitive data, and company policy
specifically restricts them from accessing the Internet.
4.1. Volume Activation Management Tool
The Volume Activation
Management Tool (VAMT) version 1.2 is part of the Microsoft Windows
Automated Installation Kit for Windows 7. It can be used to manage activation of Windows Vista, Windows
7, Windows Server 2008, and Windows Server 2008 R2.
You would use the VAMT if
clients can't access the Internet or to manage MAK keys. The overall
process to use VAMT is as follows:
Install
VAMT on a host computer, which can be any Windows Vista, Windows 7,
Windows Server 2008, or Windows Server 2008 R2 computer.
Configure
the Windows Management Instrumentation (WMI) firewall exception on all
clients (if not already configured and if the firewall is running).
Create a Computer Information List (CIL) as a group within VAMT.
Have VAMT collect license status information for clients in the CIL using WMI.
Add
a MAK to the VAMT. The number of computers activated with the MAK is
tracked by Microsoft, and you can query Microsoft to determine how many
operating system activations are left using the MAK.
Install the MAK on the client computers and then activate them.
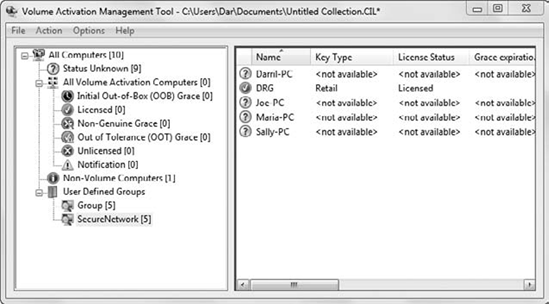
Figure 4
shows the VAMT with several computers added to a group named
SecureNetwork. In the figure, one computer has already been activated
with a retail (non-MAK) key. The other computers have not been activated
yet.
4.2. Inventory and Licensing Compliance Audits
The biggest benefit of using
VAMT with MAK is the ability to inventory your licenses and help with
licensing audits. A license audit is accomplished by identifying what
software is installed and then comparing it to what software has been
purchased.
Once you add MAKs to VAMT, you
can access the Refresh Remaining Count command to query the Microsoft
licensing site and identify exactly how many remaining activations exist
for the MAK. This tells you both how many licenses are purchased for
any MAK you add to VAMT and how many remain.
In large organizations,
license audits will often be accomplished using advanced tools such as
System Center Configuration Manager (SCCM).
4.3. Using a MAK Proxy
Although you can use VAMT to
activate clients with a MAK, you may have noticed a problem for the
computers working in an isolated network. By definition, the isolated
network wouldn't have access to the Internet. On one hand, you would use
VAMT for activation of computers in isolated networks, but on the other
hand, the VAMT computer accesses both the network and the Internet,
which would violate the security rules of ensuring the isolated network
remains isolated.
Instead, you can use VAMT as a MAK
proxy. One instance of VAMT is in the secure network and captures data
from the secure computers. Another instance of VAMT is installed on a
computer with access to the Internet. It acts as a proxy to connect to
the Microsoft licensing site, presents the data from the secure
computers, and receives activation data. This activation data is then
copied to the instance of VAMT in the secure environment.
|
A MAK proxy is used to activate
clients in a secure network when KMS is not being used. This would be
common in secure networks with fewer than 5 servers or fewer than 25
clients.
|
|
The following steps outline the process of using VAMT as a MAK proxy:
Install VAMT on a computer in the secure network and in a network that has access to the Internet.
Perform the following steps on the computer hosting VAMT in the secure network:
Collect
the status of the computers in the secure network using VAMT. This data
is referred to as a Computer Information List (CIL) and can be exported
as a file.
Copy the CIL to removable media such as a CD.
Transfer the removable media to the computer hosting VAMT with access to the Internet and complete the following steps:
Import the CIL using VAMT.
Use VAMT to connect to Microsoft and request Computer Identification numbers (CIDs) using this CIL.
Export the CIL with the CIDs from Microsoft. Copy the new CIL to removable media.
Transfer
the removable media holding the new CIL to the computer hosting the
VAMT in the secure network and complete the following steps:
Apply the new CIDs using MAK Proxy Activate.
While this process will work
for networks of any size, there is an easier and more automated method
for larger networks. In any isolated network with more than 5 servers,
more than 25 clients, or a combination of more than 25 clients and
servers, you can use the Key Management Service. MAK keys cannot be used
with the Key Management Service, but instead KMS keys are used.
5. Key Management Service and Licensing Infrastructure
The Key Management
Service is used for enterprises with a large number of clients in secure
networks. Clients will access the KMS server for temporary activation
instead of connecting to Microsoft's activation servers for permanent
activation.
Two important concepts are worth repeating with KMS:
Activation is temporary.
Clients are not
permanently activated. Instead, they must periodically connect to the
KMS server to be reactivated. Temporary activation will last for 180
days.
KMS is used for a large number of clients.
Specifically, KMS can be
used only if there are five or more servers or 25 or more clients and
servers that need to be activated by KMS. If the numbers fall below this
threshold, KMS will stop reactivating clients.
You can download KMS for free. Go to www.microsoft.com/downloads,
and search for "Key Management Service." You can install it on Windows
Server 2003, Windows Server 2008, or Windows Server 2008 R2.
If you're running a KMS
server on a Windows Server 2008 server, you can update it to provide
activation for Windows 7 and Windows Server 2008 R2. Knowledge Base
article 968915 (http://support.microsoft.com/kb/968915) provides the information on this extension and links for the download.
NOTE
At this writing, there
isn't a single download for KMS to support Windows 7 and Server 2008 R2.
You must install the earlier version and then extend it using KB
968915. However, I expect it's just a matter of time before Microsoft
releases a single-version download.
5.1. KMS Activation Terms
When discussing the Key
Management Service (KMS), it helps first to understand the different
terms associated with KMS. Once you grasp the terms, the process is much
easier to understand. I've outlined many of the basic terms here:
KMS host
The server hosting the KMS service is commonly referred to as the KMS host.
KMS client
Clients configured to contact the KMS host are referred to as KMS clients.
DNS publication
A KMS host can publish
Domain Name System (DNS) SRV records (server records) to the DNS server
using dynamic DNS within a Microsoft domain. If DNS isn't configured to
allow dynamic updates, the SRV records must be manually configured on
the DNS server so that KMS clients can locate the KMS host.
Activation threshold
The minimum number of
clients a network must have for KMS activation to work is referred to as
the activation threshold. A network must have at least 5 servers for
server activation to work or a combination of at least 25 servers and
clients for client activation to work. The KMS host tracks this
threshold, and if the threshold isn't reached or the number of clients
falls below this threshold, it will no longer activate the clients. KMS
clients that aren't activated because the activation threshold is not
met will request activation every two hours.
Activation validity interval
After activation by a KMS
host, KMS clients will remain activated for 180 days. If the KMS client
has not connected to a KMS server within 180 days, the activation will
be invalidated. Clients attempt to connect every seven days, and when
they connect, this 180-day counter is reset.
Activation count
The current number of
clients that are being activated by KMS is tracked using unique client
machine identification designation (CMID) records. Clients attempt to
contact the KMS server every seven days, and the KMS server renews this
CMID when the client activates or reactivates. If the client doesn't
renew within 30 days, the CMID is discarded and is no longer counted
toward the activation threshold.
This is an important
concept. Your network may have reached the threshold of 25, and then two
systems are decommissioned or taken on the road by sales people. Within
30 days, the CMID for these two systems will be removed from the KMS
host, and the count will be at 23. Clients will no longer be activated,
and within seven days all 23 remaining systems will be trying to
activate every two hours. Even though the clients will stay activated
for 180 days, these failures will result in errors in the event logs.
Once two new clients are added to the network, everything will
normalize.
5.2. KMS Activation Process
The KMS activation process
is ongoing, requiring the KMS clients to connect to the KMS host
periodically. Before the process can start, an SRV record must exist in
DNS so the clients can reach the KMS server.
Normally, dynamic update
will be configured in DNS, which allows the KMS service on a KMS host to
publish SRV records automatically to DNS. Once this is configured, no
further steps are required. KMS clients then query DNS to locate the KMS
host.
|
DNS is a critical
component of the KMS activation process. If KMS clients can't locate the
KMS host because the SRV records aren't published in DNS, activation
won't occur. If KMS was working and has stopped, DNS should be checked
to ensure the KMS host record exists. These records will be in the _VLMCS._TCP folder on the DNS server.
|
|
Once the KMS client has located the KMS host, the following process is used to temporarily activate the client:
Every seven days, KMS clients query DNS for the IP of a KMS host.
KMS clients then try to renew their activation with KMS.
If the activation fails, clients continue to try every two hours.
If
clients can't connect to the KMS host for 30 days, the record for the
client in the activation count is deleted on the KMS server. If the
activation count falls below the activation threshold, the KMS host will
stop activating clients.
If clients can't connect for 180 days, client activation expires.
If the client succeeds in reaching the KMS host, the activation will be renewed.
Once the client is activated, the seven-day counter will be reset on the KMS client.
The 180-day counter for the KMS client activation is renewed.
The
KMS host creates a new record for this client for the activation count
(which is kept for 30 days). The original record is deleted.
Seven days after the client is temporarily activated, the process starts again.
5.3. Working with KMS
In order for the KMS to
respond to activation requests, the firewall needs to be properly
configured on the KMS server. If the Windows firewall is being used, the
KMS Traffic exception can be enabled. If a third-party firewall is
being used, you'll need to open port 1688.
In addition, you can use the Software Licensing Management Tool (slmgr.vbs) to configure and manage specific settings on the KMS server. Table 2 shows some of the common switches used with KMS.
Table 2. Slmgr switches used with KMS
| Switch | Description |
|---|
| /sprt #### | Use this switch to change the default port number if necessary. The default port number is 1688. |
| /cdns | This will disable automatic DNS publishing by a KMS host. The SRV records must be manually created on DNS. |
| /cpri | This will reduce the priority of host processes. Use this if the KMS host needs more processing power for other server roles. |
| /spri | This returns the priority of host processes to normal on the KMS server. |
| /sai # | You
can use this to change how often a KMS client tries to connect to a KMS
if activation fails. The number is provided in minutes, and the default
is 120 (two hours). |
| /sri # | This
will change how often a KMS client contacts the KMS host to renew the
activation. The number is provided in minutes, and the default is 10080
(seven days). |
| /dli | When executed on the KMS server, this provides the current activation count on the KMS server. |
| /skms | You can use this to set the name and the port of the KMS server for non-domain computers. |
6. Virtualization Licensing
If your company is
considering a Virtual Desktop Infrastructure (VDI) solution, you'll need
to understand the licensing requirements. It's important to realize
that licenses are needed for the virtual machines just as they are
needed for a regular installation.
Virtual computers can be
activated using MAK keys or KMS servers. In addition, Microsoft recently
announced the Virtual Enterprise Centralized Desktop (VECD), which can
be used specifically for VDI licensing. VECD allows an organization to
license virtual copies of Windows client operating systems at a lower
cost than a full version of the operating system. VECD uses a
device-based subscription license and is available with two
configurations:
VECD for Software Assurance (SA), currently priced at $23/year
VECD, currently priced at $110/device/year
Once VECD is purchased, you
can deploy as many as four virtual desktops on any single system. This
doesn't include the cost of the host operating system. The host
operating system could be Windows 7, Windows Server 2008, Windows Server
2008 R2, or other operating systems.
VECD offers many benefits, including these:
Rights to move virtual machines between systems for increased reliability
Unlimited backup of virtual machines
Ability to access up to four running VM instances per device
Rights to access corporate desktops from home for a user who has already been licensed at work
Licensing of Microsoft
products can easily get complicated, and pricing often changes. When
you're looking at purchasing licenses, you should locate a Microsoft
Licensing Specialist through a Microsoft partner.
Remember these two key points, however: