Security
Because SQL Azure is
implemented in a different way compared to on premise SQL Server, there
are a number of differences regarding security. A complete overview of
SQL Azure security is found in the MSDN documentation, available at http://msdn.microsoft.com/en-us/library/ee336235.aspx.
First and foremost,
only SQL Authentication can be used. This make sense, as there really is
no Azure Active Directory a user account could be part of. Each time a
connection is made, the SQL credentials must be supplied.
In SQL Azure, there is no "sa"
account. Instead, the user account used to provision the instance
becomes the equivalent of "sa". In SQL Server 2008, the roles securityadmin and dbcreator are both server-level roles, and are not present in SQL Azure loginmanager replaces securityadmin, whereas dbmanager replaces dbcreator.
For security reasons, several user names are "reserved". We cannot create user names that begin with:
Admin
Administrator
guest
root
sa
Connecting to SQL Azure is
slightly different too. Encryption must always be supported, and only
TCP/IP connections can be made. Before we connect to SQL Azure, the SQL
Azure firewall needs an exception for our IP range, and the local
computer may need a firewall exception for port 1433. If we are allowing
Windows Azure applications to connect to SQL Azure, we need to
whitelist Windows Azure by adding the IP address 0.0.0.0 to the Azure
firewall.
Development considerations
In ADO.NET, application should
have retry logic to catch errors due to service closing. Because of
failover and load balancing, we can't guarantee that a connection will
always be available or even accessible.
Depending on how an application supports the tabular data stream (TDS), the login name in the connection string may need to be<login>@<server>.
All design and user
administration must be performed using T-SQL scripts. This means if
we're used to performing these functions via the GUI in SSMS, it's time
to brush up on the command syntax.
Finally, there are two sizes of SQL Azure database. If our database reaches its maximum size, we'll receive the 40544
error code and we'll be unable to insert/update data (but read
operations will continue as normal). We'll also be unable to create new
database objects.
Managing maximum size
If we reach the maximum size
limit set for a Web Edition database (5 GB), then it is not easy to
migrate from a Web Edition database to a Business Edition database. If
our database exceeds 5 GB in size and we want to allow further growth,
we would need to create a Business Edition database and use the database
copy to migrate our data. We can also remove data to free some space,
but there can be a 15-minute delay before more data can be inserted.
If we reach the maximum size
limit set for a Business Edition database (50 GB), our only option is to
remove some data to free some space. Again, there can be a 15-minute
delay before more data can be inserted.
To prevent issues in our live
databases, it's important we have a good policy regarding data retention
and storage. Instead of storing images and other binary objects in SQL
Azure, use blob service and store a pointer in the database. Older data
can be archived into other SQL Azure databases, or into an on premise
database.
Management tools
Developers who are used to the GUI interface of SSMS, will find
managing SQL Azure frustrating. A good grasp of DDL query commands is
necessary to fully manage a SQL Azure database. Sometimes, creating and
managing a SQL Azure database may involve two or more tools.
SQL Azure portal
The SQL Azure portal is the
only place where databases can be created and firewall rules can be set.
We can also retrieve connection strings from the SQL Azure portal.
SSMS 2008 R2
Because SQL Azure was
released after SQL Server 2008, SQL Server Management Studio Express
2008 R2 or any higher version must be used to connect to SQL Azure. Only
the client tools need to be installed, but this will upgrade any client
tools and drivers currently installed on the system.
Unlike SQL Server, tables in
SQL Azure cannot be created using the properties grid style of table
designer. Instead, every configuration must be performed via SQL
queries. And we do mean everything table creation, user creation, user permissions, setting foreign keys, and so on.
Project Houston
Project Houston is a Silverlight-based database editing tool provided by Microsoft. It can be found at http://www.sqlazurelabs.com/houston.aspx.
At the time of writing, Project Houston was in CTP 1. Databases must be
created in the SQL Azure portal; however, in Houston we can create
tables using the more familiar properties grid. At the time of writing,
alterations to tables (such as adding foreign keys) must still be done
with DDL queries. We can also run queries, create stored procedures and
views, and directly enter/edit data. Creating a new table is shown in
the following screenshot:
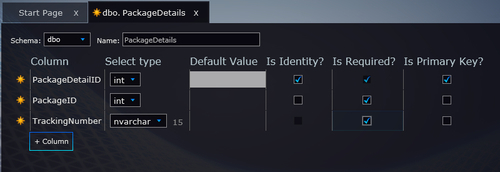
One advantage of using
Houston over SSMS is that we don't need to configure firewall rules for
every client location. Because Houston is a Microsoft service, the
0.0.0.0 rule allows access to our databases.
Access 2010
In an announcement that made a
great number of enterprise developers weep, Microsoft added support for
SQL Azure to Access 2010 via ODBC. Tables can be linked or users can
use pass-through queries. Access 2010 support provides a database entry
point business users are familiar with, but which can sometimes grow
into an unmanageable mess.
The SQL Server Native
Client 10.0 or higher is required for access to connect to SQL Azure.
This driver is installed with any flavor of SQL Server 2008 R2, SSMS
2008 R2, or as a standalone driver in the SQL Server 2008 R2 Feature
Pack at http://www.microsoft.com/downloads/en/details.aspx?FamilyID=ceb4346f-657f-4d28-83f5-aae0c5c83d52&displaylang=en.
If we want to migrate an existing
Access 2010 database to SQL Azure, the recommendation is to use the SQL
Server Migration Assistant (SSMA) rather than the Upsizing Wizard.
Managing databases, logins, and roles in SQL Azure
Managing databases and
logins in SQL Azure is very similar to managing them in an on-site
instance of SQL Server. Using T-SQL commands, you can create/alter/drop
logins, create/drop databases, and create/alter/drop users, though some
parameters are not supported. One thing to remember is that all
server-level and database-level security must be applied to the "master"
database that is created when your SQL Azure service has been
provisioned. Also, the administrator username you selected when
provisioning the service is similar to the "sa" user in an on-site
instance of SQL Server.
There are also two new roles in SQL Azure: loginmanager and dbmanager. The loginmanager role is similar to the securityadmin role of SQL Server, whereas the dbmanager
role is similar to the dbcreator role of SQL Server. You can add users
to either of these roles if you want them to have the permissions to
create/alter/drop logins and users (loginmanager), or create/alter/drop
databases (dbmanager).