Virtualization gives you the ability to host multiple
independent instances of operating systems on a single server. The
virtualized instances "borrow" physical resources from the host system.
You are able to configure the virtual machines to provide the required
amount of physical resources to the virtual machine. Here are some of
the resources you can manage and present to your virtual machines:
Virtualization of servers is
becoming popular in many organizations. There are compelling reasons to
consider virtualization for your infrastructure, although some
situations will not lend themselves to a positive virtualization
experience.
Technology continues to
evolve, and we have seen great strides in the virtualization world over
the past few years. There are multiple vendors in the virtualization
game. Microsoft and VMware both have hypervisors that are at the top of
the pile for virtualization technologies. They are not the only
companies offering virtualization solutions, but they are the most
popular. Figure 1 gives a virtualization overview.
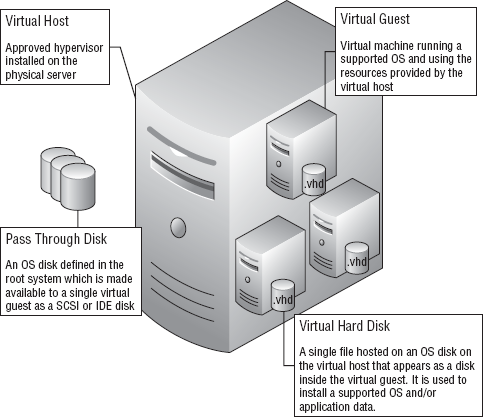
1. Terminology
Table 1. Virtualization Terms
| Term | Definition |
|---|
| Virtual host | The
server that is running the virtualization product. This is the computer
that is sharing its physical resources to the virtual guests. Also
referred to as the parent. |
| Virtual guest | Virtual machine running a supported OS and using the resources provided by the virtual host. |
| Database availability group (DAG) | A group of Mailbox servers that host a set of databases and provide automatic database-level recovery from failures. |
| Virtual hard disk (VHD) | The
virtual hard disks are the files that will hold the operating system,
data, application, and so forth for the virtual guests. |
| BIN | This
is the temporary memory storage. It is the same size as the virtual
guest RAM size. The BIN file is located on the virtual host file system
and is used to dump memory during a system save or planned migration
from one node to another node in a cluster. |
| VSV | This
is the virtual save state file. It is also stored on a virtual host
file system. It is used to save the virtual guest state during save
operations or a planned failover to another node. |
| Fixed VHD | Presented
to the virtual host as a predetermined size for virtual guests to use.
When this disk is presented to the virtual host, it is at its maximum
size. |
| Dynamic VHD | Presented
to the virtual host; dynamic VHD has been set with a maximum size. This
disk is initially only a fraction of the maximum size and will grow as
data is written. There is a performance hit as the disk grows. |
| Differencing VHD | This
is linked to a fixed or dynamic VHD. Changes are written to the
differencing VHD and not to the fixed or dynamic VHD. Any changes can be
rolled back to a previous state. Differencing VHD would be used for
testing purposes only. |
2. Understanding Virtualized Exchange
Microsoft started
supporting Exchange as a supported, virtualized application with
Exchange 2003. Support for virtualizing Exchange and the desire to
virtualize Exchange has grown since then. With Exchange 2007, the
virtualization platform moved from Virtual Server to one of the approved
hypervisors. This moved Exchange into the mainstream for applications
that could take advantage of the benefits of virtualization.
Microsoft's stance on
virtualizing Exchange has not changed between Exchange 2007 and Exchange
2010. Windows Server 2008 SP2 and Windows Server 2008 R2 are the only
supported operating systems for the virtualization of Exchange 2010.
Supported roles include the Mailbox, CAS, Hub Transport, and Edge
Transport roles. The Unified Messaging role is not supported because it
has too much voice codec processing for it to be a viable candidate for
virtualization. Visit http://technet.microsoft.com/en-us/library/cc794548.aspx
to learn the details of Microsoft's support policy. The virtualized
instances of Exchange must still meet the basic Exchange requirements.
|
Make sure you have read and
are familiar with the "Microsoft Support Policies and Recommendations
for Exchange Servers in Hardware Virtualization Environments," which
you'll find at http://technet.microsoft.com/en-us/library/cc794548.aspx.
Here are some of the unsupported technologies:
The combination of virtual host clustering and Exchange Mailbox high availability Snapshots of the virtual machines Differencing disks Virtual-to-logical processor ratios greater than 2:1 Any applications running in the root partition
|
3. Understanding Your Exchange Environment
Before virtualizing
your Exchange environment, you must define your current environment.
The better you understand your environment, the more prepared you will
be to define the virtualized environment. Here is some of the
information you need to gather:
Number of users
User profiles
Number of messages sent/received per day, per user
Server CPU utilization
Server memory utilization
Server network utilization
Database sizes
Storage patterns
Storage type
Current high availability model
Concurrently connected users
Number and types of clients accessing the system
Exchange connectors
Administration model
As you gather this
information, you will be painting a picture of your Exchange
environment. This information will be placed into various calculations
throughout the process to ensure that you have done a complete
evaluation before moving forward with virtualization. This information
will have a significant impact on the Exchange system moving forward.
For example, 500 users who have heavy profiles (see Table 2) will utilize storage much differently than 500 users who have average profiles.
Table 2. Exchange User Profiles
| User Profiles | Messages Sent/Received per Day |
|---|
| Light | 5 sent/20 received |
| Average | 10 sent/40 received |
| Heavy | 20 sent/80 received |
| Very heavy | 30 sent/120 received |
Each bit of the information
you gather will add another piece to the puzzle. As you put the puzzle
together, you will have a good idea whether virtualization will meet
your needs. You also will be able to validate whether you will get the
performance from the virtualized environment that your users require.