Configuring and Optimizing Group Policy
After a Group Policy Object
is created, a few steps should be taken to configure how the policy will
be applied and to optimize the time to apply the policy. Group policies
can be limited to computer- or user-specific settings. To determine
whether either type of setting can be disabled, the administrator should
determine which settings are necessary to provide the desired policy
settings. In many cases, a policy uses settings for both types.
When multiple group policies
exist, they are applied in a predefined order. For a particular user or
computer, the order can be derived using the Resultant Set of Policies
snap-in. The results of standard policies are that if setting X is
enabled on a top-level policy and disabled
on the last policy to apply to an object, the resulting setting will
disable setting X. Many policy settings have three states: enabled,
disabled, and the default of not configured.
You can limit group
policies to apply to specific users or computers by modifying the
security entries. In addition to disabling portions of each GPO, policy
inheritance can be blocked at the domain or OU container level using a
setting called Block Policy Inheritance. When blocking or precedence
rules need to be ignored for the settings of a particular group policy,
the group policy can be configured as Enforced.
Group Policy Objects and Logon Performance
It is important that policies
be effectively placed to avoid slow logon performance. For each level
in the OU structure where a group policy is linked, the download and
application of the policies at that level can cause 15–30 seconds of
additional logon or startup delay. This is because the Group Policy
Objects at a particular OU level are evaluated at one time, which takes a
few seconds. The process is repeated for each OU level where there are
GPOs, and that processing time can really stack up, leading to longer
logon delays for the users and complaints to the help desk.
Interestingly, the same applies for the computer startup as the policies
are applied, but users don’t notice that as much.
Note
The logon delay is something
that can develop over time as the Active Directory infrastructure
matures. When initially deployed, the Active Directory will have
relatively few GPOs and, consequently, logon delays will be short. As
time progresses, more GPOs are added and more OU levels with GPOs are
added, with an increase in the logon times that users experience. This
creeping logon time can be directly traced to the proliferation of GPOs.
The general guidelines to reduce the logon performance impact are as follows:
Reduce the number of OU levels—
By reducing the number of OU levels, there will be fewer levels to link
GPOs to and, thus, better performance. The best practice is to have a
maximum of three levels, if possible. If more are needed, prohibit the
linking of GPOs to some of the levels.
Reduce the number of GPOs—
By consolidating settings into fewer GPOs, less processing time is
needed to read the GPOs. A single GPO at the same OU level will perform
faster than 10 GPOs at the same level.
Use security filtering—
If a GPO is security filtered to not apply to a user or computer, the
settings do not need to be read or processed. This speeds up logon and
startup performance.
Disable user or computer settings in GPOs— Each
GPO consists of a user and a computer section. If there are no settings
in either of those sections, that section can be disabled and will be
ignored. For example, if a GPO only has computer settings and the user
settings are disabled, that GPO will be skipped at logon (which only
deals with user settings).
These guidelines can dramatically improve logon and startup performance.
The last guideline
suggested disabling the user setting or computer settings, as processing
a GPO takes a certain amount of time for a computer at startup and for a
user at logon. To enable or disable the entire GPO or the user/computer
portion of the GPO, run the following steps:
1. | Open the Group Policy Management console.
|
2. | Expand the Forest folder, expand the Domains folder, select the specific domain, and select the Group Policy Objects.
|
3. | Select the GPO to enable or disable it.
|
4. | Right-click the GPO and select GPO Status.
|
5. | Select
the appropriate option: Enable, User Configuration Settings Disabled,
Computer Configuration Settings Disabled, or All Settings Disabled.
|
This will take effect
immediately. The All Setting Disabled option is useful for
troubleshooting when you want to completely disable a GPO without
changing the ACLs or the settings.
Block Policy Inheritance
The Block Policy Inheritance
option enables an administrator to prevent higher-level policies from
applying to users and computers within a certain domain or OU. This
capability can be useful to optimize Group Policy applications and
protect sensitive user and/or computer accounts from organization-wide
policy settings.
To block policy inheritance, follow these steps:
1. | Launch Server Manager on a domain controller.
|
2. | Expand the Features folder.
|
3. | Expand the Group Policy Management Console.
|
4. | Expand the Forest folder.
|
5. | Expand the Domains folder.
|
6. | Select the specific domain, such as companyabc.com.
|
7. | Locate and right-click the OU for which you want to block inheritance, and select Block Inheritance, as shown in Figure 2.
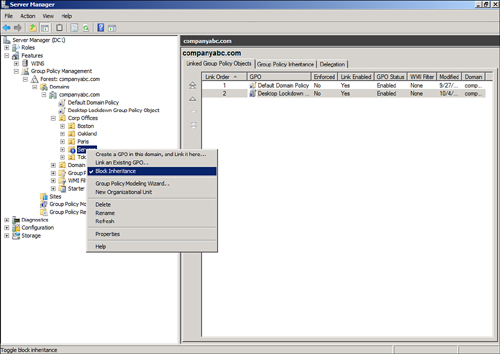
|
In this example, policy
inheritance was blocked on the Servers OU. Group policies created above
the OU will not affect objects within the OU (unless the group policy is
enforced; see the next section). Note the blue exclamation mark icon on
the OU to alert the administrator that policy inheritance is blocked.
The Enforce Option
Configuring the Enforce
option prevents lower-level policies from blocking policy inheritance
and from changing the parameters or configured settings in a policy.
This option should be used only if a policy needs to be enforced on AD
objects in every container and subcontainer with a link or inheritance
to this policy object.
To configure the Enforce option for a policy, follow these steps:
1. | Launch Server Manager on a domain controller.
|
2. | Expand the Features folder.
|
3. | Expand the Group Policy Management Console.
|
4. | Expand the Forest folder.
|
5. | Expand the Domains folder.
|
6. | Select the specific domain, such as companyabc.com.
|
7. | Right-click the group policy to enforce, and select Enforce.
|
Now
the group policy will be enforced even if the Block Policy Inheritance
option is set on down-level OUs. Note that the group policy will now
have a small lock icon associated with it to show that it is enforced.