Windows Server 2008 R2 systems provide local security
policies to manage user and group administrative access on a per-server
basis. Within Active Directory, you can use group policies to set
configurations and security on a specified collection of computers,
users, or groups of users from a single policy. These policies can be
used to deliver standard desktop configurations and security settings
for server access and application functionality. Also, policies can set
user configurations to deliver software on demand, redirect desktop
folders, plus affect many more settings. Many settings within each
policy explain what the setting controls and whether computer-based
settings apply to only Windows XP, Windows Vista, or Windows 7
workstations.
Viewing Policies with the Group Policy Management Console
You can view Active
Directory-based group policies or server and workstation local security
policies with very little effort by using a single console, the Group
Policy Management Console (GPMC). This tool is added to the Server
Manager console when the Active Directory Domain Services role is added
to a server. The GPMC enables administrators to view group policies,
edit group policies, and model the effects of combinations of group
policies (that is, model the resulting configuration).
To open an existing policy, follow these steps:
1. | Launch Server Manager on a domain controller.
|
2. | Expand the Features folder.
|
3. | Expand the Group Policy Management Console.
|
4. | Expand the Forest folder.
|
5. | Expand the Domains folder.
|
6. | Expand the specific domain, such as companyabc.com.
|
7. | Select a Group Policy Object, such as the Default Domain Policy. Click OK to close the linked policy warning window.
|
8. | Select the Settings tab to review the settings. Or right-click the Group Policy Object, and select Edit to change the settings.
|
After you access the policy,
you can view each setting or settings container to determine the
default value and, in some cases, learn what the setting controls. Keep
in mind that, with the correct level of permissions, any changes you
make to this policy are live changes; there is no undo other than
reversing the individual setting changes or performing an authoritative
restore of Active Directory.
Creating New Group Policies
When changes need to be made
or tested using group policies, the administrator should leave the
production environment untouched and create test policies in isolated
test lab environments. When test labs are not available or cannot
replicate the production environment, the administrator can test
policies in isolated organizational units within a domain. Also, if
domain- or site-based policies need to be created for testing, security
filtering could be modified to apply the policy only to a specific set
of test users or groups.
The preceding section
described how to locate a group policy. Using the Group Policy
Management Console, you can also create, configure, and open site,
domain, and organizational unit (OU) group policies for editing.
In some cases, it will be
necessary to prevent a GPO from being applied to a user or computer.
That is, there might be a GPO that applies to all members of a
department, but it is necessary to make a single exception to the rule.
Rather than create a specific OU to apply the GPO, security filtering
can be used to allow or deny the application of the Group Policy Object.
The following steps outline how
to create a new domain-based policy and configure its security filtering
to apply to a single user:
1. | Launch Server Manager on a domain controller.
|
2. | Expand the Features folder.
|
3. | Expand the Group Policy Management Console.
|
4. | Expand the Forest folder.
|
5. | Expand the Domains folder.
|
6. | Select the specific domain, such as companyabc.com.
|
7. | Right-click on the domain and select Create a GPO in This Domain, and Link It Here.
|
8. | Type in a descriptive policy name, leave the source starter GPO set to None, and click OK to create the policy.
Note
Source starter GPOs are
GPO templates that can be used to prepopulate settings in GPOs. If there
are common settings that will go into GPOs, they can be created in
starter GPOs and then seeded into new GPOs as they are created.
The starter GPOs are stored
in a common folder named StarterGPOs. Any GPOs created in this folder
are available for seeding GPOs. There are no starter GPOs in a domain by
default.
|
9. | The
new policy will be displayed in the right pane. Right-click the new
policy and select Edit to launch the Group Policy Management Editor
snap-in.
|
10. | Right-click the GPO name in the Group Policy Management Editor, and select Properties.
|
11. | Select the Security tab and highlight the Authenticated Users entry.
|
12. | In
the Permissions section, scroll down and uncheck the Allow check box
for Apply Group Policy. This means that the GPO will not take effect on
any user or computer.
|
13. | Select each entry in the Group Policy access control list and verify that no existing groups are allowed to apply Group Policy.
|
14. | Click
Add and type in the name of a user or group. To find a list of users
and groups within the current domain, click the Advanced button, and in
the search window, click Find Now to return the complete list. Scroll
down and select the users or groups you want, and click OK.
|
15. | Click OK to add the entries to the policy.
|
16. | Back in the security window, select the respective entry and check the Allow check box for Apply Group Policy, as shown in Figure 1. This means that the GPO will take effect on the members of this group, which could include both users and computers. Click OK when you’re finished.
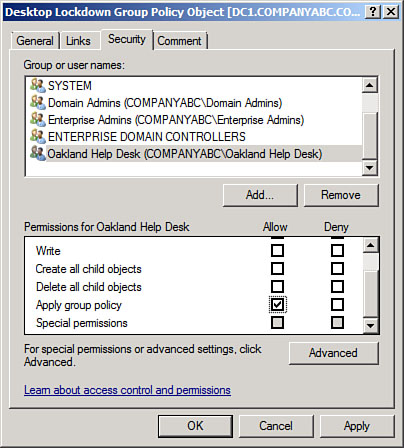
|
17. | Close the Group Policy Management Editor snap-in.
|
Now the group policies set in
the GPO will affect only the users or computers that were specified—in
this case, members of the Oakland Help Desk. This allows for
fine-grained application of group policies to targeted groups.