Wireless Security
Microsoft
Windows Vista offers the full complement of wireless security. Wireless
security presents the most troublesome aspect of wireless network
configuration because the WCN wizards, along with a host of other
wizards in the Network and Sharing Center, allow easy creation of a
wireless connection.
Several security features offer a
thin layer of security to wireless communication. The following
sections look at these before proceeding into the two major aspects of
securing wireless communication: authentication and encryption.
To Broadcast or Not Broadcast the SSID: That Is the Question
Many previous works
on wireless security describe one way to make it harder to hack a
wireless network: disable the broadcast of the SSID. This is a nonissue
anymore because a plethora of tools can easily discover access points
that are not broadcasting the SSID as well as prompt the APs to give up
the SSID. Although this may seem like a good idea because it hides the
AP from the casual bad guy, in reality it is probably more of a nuisance
not broadcasting the SSID to the network administrator than it is to
the bad guys attempting to crack into your wireless network. In
addition, considering that even Windows Vista now supports the ability
to “see” APs that are not broadcasting their SSID also makes this
security mechanism fairly useless when you are trying to hide its
presence.
MAC Address Filtering
Wireless access points usually contain a feature referred to as MAC ID filtering.
This allows you to select which MAC addresses are allowed to associate
with the AP for a wireless connection. This is a tedious process because
you must acquire the MAC IDs of all wireless adapters within the
environment. In addition, you must manually update this list as MAC IDs
are added or subtracted in the environment due to new devices being
added or older devices being discarded.
One obvious downside to
relying on MAC ID filtering is that MAC IDs can be easily faked because
the MAC address is unencrypted by wireless encryption schemes. Tools
such as SMAC can adjust the MAC ID used by a network device without
modifying the burned-in address. SMAC is one of many widely available
security or cracking utilities for this purpose. An additional downside
to this thin layer of added security is that MAC IDs within the BIOS of
many computers can also be adjusted, thus making it harder to manage
which MAC IDs are allowed on the network.
With that being said,
using this approach is still a decent first start because it does make
the casual cracker look elsewhere. On the other hand, you should not
consider this feature to be anything more than a casual nuisance to a
true bad guy intent on entering your wireless network.
Static IP Addressing
Static
IP addressing ups the ante a bit when attempting an illicit entry into a
wireless network. Because most APs offer a DHCP service within their
configuration, disabling this feature and manually assigning IP
addresses would make it one step harder to gain entry into the wireless
network beyond an association to the AP. If the subnet size used for the
wireless portion of the network is sized according to only the desired
need of that subnet, a would-be hacker would have a more difficult time
picking up the use of an additional IP address and going unnoticed.
Using this approach definitely stops the casual hacker and requires a
bit more sophistication. But once again, there are tools available that
aid a bad guy in working around this issue.
Another downside of
this approach to wireless security is, once again, the tedious nature of
managing the wireless network. Manual IP addressing in IPv4 is bad
enough; it is inconceivable when discussing IPv6 networks. Also, using
this method may not stop a wireless cracker because there are
Man-in-the-Middle attacks and many others around this approach to
wireless security.
Authentication and Encryption Methods to Wireless Security
The preceding methods may
offer an initial starting point to securing your wireless network, but
they also have trade-offs when you’re attempting to manage the networks
employing those methods. Windows Vista supports several wireless
standards when it comes to authentication and encryption. Table 2 offers a snapshot of the protocols that are available to use within Windows Vista itself.
Table 2. Wireless Authentication and Encryption Protocols
| Security Feature | Authentication Offered | Encryption Type |
|---|
| Wired Equivalency Privacy (WEP) | Open (none) | WEP |
| Wired Equivalency Privacy (WEP) | Shared Key | WEP |
| Wi-Fi Protected Access (WPA)-Preshared Key (PSK) | None | WPA-PSK with either Temporal Key Integrity Protocol (TKIP) or Advanced Encryption Standard (AES) |
| WPA-Enterprise | IEEE 802.1x | WPA with TKIP or AES |
| WPA2-Personal (PSK) | None | WPA (PSK) with TKIP or AES |
| WPA2-Enterprise | IEEE 802.1x | WPA2 with TKIP or AES |
| Open | None | None |
| 802.1x | 802.1x | None |
The following sections disregard the last two security feature types from Table 2,
focusing the discussion on the more useful settings. Using these two
security features by themselves presents a flawed approach to wireless
security:
Using Open as the only
security feature is using no security feature at all. This is fine for
publicly accessible APs but not for corporate use.
The
802.1x authentication protocol is highly secure, but it does not
provide any encryption. Therefore, using 802.1x alone provides no
security for the actual data that is communicated after authentication.
WEP
WEP
was the original encryption scheme when 802.11 wireless standards were
first created. It was soon discovered to have severe flaws in the way it
employed the use of the RC4 algorithm for its encryption services. It
is considered to be better than nothing and may be the only choice if
you are using legacy devices or software. WEP, as defined by the IEEE,
comes in 64-bit and 128-bit sizes as well as a newer 256-bit flavor.
Using Shared for the authentication means that the Pre-shared key used
for the encryption process by WEP is also used to authenticate the
connection. This is actually considered to be less secure than the Open
setting for authentication. Figure 9 shows how to reconfigure a wireless connection for WEP with Shared key authentication.
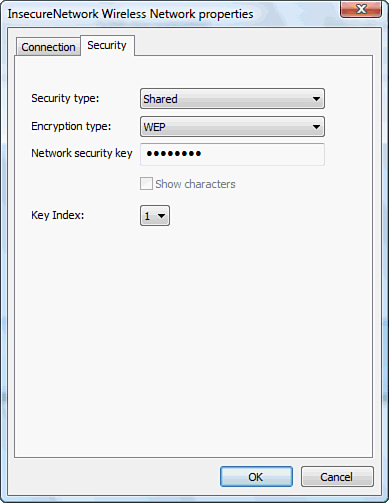
Using the dialog box in Figure 9 as a guide, you can change the security type to any of the listed security types in Table 4.7.
WPA-Personal
Wi-Fi Protected
Access (WPA) was a standardized update to the encryption scheme used by
WEP. Essentially, WPA was the first step toward IEEE’s 802.11i
specification. WPA-Personal is also known as WPA-Preshared Key (PSK). In
addition to using a PSK, WPA is required to use Temporal Key Integrity Protocol (TKIP).
TKIP still uses RC4 but adds a message integrity check, providers for
per-packet keying, among other items. It was designed to be
backward-compatible with most WEP-enabled products at the time so that
only a software update was necessary. WPA-PSK may also provide for the
use of the Advanced Encryption Standard (AES) that uses the newer
Rijndael algorithm. AES is a much stronger block cipher that allows the
use of up to 256-bit keys. This is built for small office/home office
(SOHO) use.
WPA-Enterprise
WPA-Enterprise adds the use of a centralized authentication server (called an authenticator) such as a Remote Authentication Dial-in User Service (RADIUS) server and employs the use of the IEEE 802.1x authentication protocol. The client (known as the supplicant)
is required to authenticate prior to unrestricted access through the
wireless AP to the wireless network. WPA-Enterprise uses the same
encryption services as described for WPA-PSK. This protocol is built, as
its name suggests, for an enterprise network. This security model
requires a Public Key Infrastructure (PKI) to hand out certificates
because the certificate takes the place of the PSK used in WPA-PSK. The
certificate also provides for additional authentication encryption
services for the wireless clients.
WPA2-Personal
WPA2-Personal provides the
same security services as WPA except that the WPA2-Personal protocol is
required to support AES as the default protocol of choice. This
essentially ensures that legacy wireless adapters need to be replaced or
upgraded. A PSK is also used instead of a certificate.
WPA2-Enterprise
WPA2-Enterprise is the true
implementation of 802.11i, where the IEEE 802.1x authentication protocol
is used along with a centralized authenticator service running RADIUS.
Windows Vista inherently supports WPA2-Enterprise, whereas Windows XP
required an update. This security model also requires a Public Key
Infrastructure to hand out certificates for the same reasons described
for WPA-Enterprise.
Exam Alert
When determining which security feature to employ for a given scenario, consider the following ideals:
If a centralized authentication server is available and all clients are Windows Vista, use WPA2-Enterprise.
If
a centralized authentication server is unavailable for use, and a
Public Key Infrastructure is not available, the highest level of
security that you can use is WPA-Personal or possibly WPA2-Personal if
available.