Once you start peeking under Windows' hood, you'll
notice some of the tools that have been included to help the system run
smoothly. Some of these tools actually work, but it's important to know
which ones to use and which ones are simply gimmicks.1. Viruses, Malware, and SpywareMalware, or malicious software,
is a class of software designed specifically to wreak havoc on a
computer—your computer. Malware includes such nasty entities as viruses,
Trojan horses, worms, and spyware. If
you're experiencing frequent crashing, nonsensical error messages,
pop-up advertisements (other than when surfing the Web), or
slower-than-normal performance, the culprit may be one of the following
types of malware (as opposed to a feature authored by Microsoft):
Viruses
A
virus is a program or piece of code that "infects" other software by
embedding a copy of itself in one or more executable files. When the
software runs, so does the embedded virus, thus propagating the
"infection." Viruses can replicate themselves, and some (known as polymorphic viruses) can even change their virus signatures each time to avoid detection by antivirus software. Unlike worms,
defined next, viruses can't infect other computers without assistance
from people (a.k.a. you), a topic discussed in detail in the next
section. One particular type of virus, a Trojan horse, spreads itself by masquerading as a benign application (as opposed to infecting an otherwise valid file), such as a screensaver or even, ironically, a virus removal tool.
Worms
A worm
is a special type of virus that can infect a computer without any help
from its user, typically through a network or Internet connection. Worms
can replicate themselves like ordinary viruses, but do not spread by
infecting programs or documents. A classic example is the W32.Blaster.Worm, which exploited a bug in Windows XP, causing it to restart repeatedly or simply seize up.
Spyware and adware
Spyware
is a little different than the aforementioned viruses and worms, in
that its purpose is not necessarily to hobble a computer or destroy
data, but rather something much more insidious. Spyware is designed to
install itself transparently on your system, spy on you, and then send
the data it collects back to an Internet server. This is sometimes done
to collect information about unsuspecting users, but most often to serve
as a conduit for pop-up advertisements (known as adware).
Many
of these advertisements are pornographic in nature, and will make no
exceptions for the age or personal preference of those viewing them. The
good news is that this type of attack, whether designed to change your
default home page, display pop-up ads, or glean sensitive information
from your hard disk, is easily stoppable and clearly preventable. |
|
Aside
from the ethical implications, spyware can be particularly troublesome
because it's so often very poorly written, and as a result, ends up
causing error messages, performance slowdowns, and seemingly random
crashing. Plus, it uses your computer's CPU cycles and Internet
connection bandwidth to accomplish its goals, leaving fewer resources
available for the applications you actually want to use. Now,
it's often difficult to tell one type of malicious program from
another, and in some ways, it doesn't matter. But if you understand how
these programs work—how they get into your computer, and what they do
once they've taken root—you can eliminate them and keep them from coming
back. 1.1. How malware spreadsOnce
they've infected a system, viruses and the like can be very difficult
to remove. For that reason, your best defense against them is to prevent
them from infecting your computer in the first place. The
most useful tool you can use to keep malware off your computer is your
cerebral cortex. Just as malware is written to exploit vulnerabilities
in computer systems, the distribution of malware exploits the stupidity of users. Malware is typically spread in the following ways:
Email attachments
One
of the most common ways viruses make their way into computers is
through spam. Attachments are embedded in these junk email messages and
sent by the millions to every email address in existence, for
unsuspecting recipients to click, open, and execute. But how can people
be that dumb, you may ask? Well, consider the filename of a typical
Trojan horse: -
kittens playing with yarn.jpg .scr
Since Windows has its filename extensions hidden by default , this is how the file looks to most Vista users: -
kittens playing with yarn.jpg
In other words, most people wouldn't recognize that this is an .scr (screensaver) file and not
a photo of kittens. (The long space in the filename ensures that it
won't be easy to spot, even if extensions are visible.) And since many
spam filters and antivirus programs block .exe files, but not .scr files—which just happen to be renamed .exe
files—this innocuous-looking file is more than likely to spawn a nasty
virus on someone's computer with nothing more than an innocent
double-click. So, how do
you protect yourself from these? First, don't open email attachments you
weren't expecting, and manually scan everything else with an up-to-date
virus scanner (discussed later in this section). Next, employ a good,
passive spam filter, and ask your ISP to filter out viruses on the server side. Where
do these email attachments come from, you may ask? As part of their
objective to duplicate and distribute themselves, many viruses hijack
your email program and use it to send infected files to everyone in your
address book. In nearly all cases, these viruses are designed to work
with the email software most people have on their systems, namely
Microsoft Outlook and Windows Mail (formerly Outlook Express). If you
want to significantly hobble your computer's susceptibility to this type
of attack, you'd be wise to use any other email software, such as Mozilla Thunderbird (http://www.mozilla.com) or stick with web-based email like Gmail (http://www.gmail.com) or Windows Live Mail (http://mail.live.com). |
|
Infected files
Viruses
don't just invade your computer and wreak havoc, they replicate
themselves and bury copies of themselves in other files. This means that
once your computer has been infected, the virus is likely sitting
dormant in any of the applications and even personal documents stored on
your hard disk. This not only means that you may be spreading the virus
each time you email documents to others, but that others may be
unwittingly sharing viruses with you. One of the most common types of viruses involves macros,
small scripts (programming code) embedded in documents. By some
estimates, roughly three out of every four viruses is actually a macro
written for Microsoft Word or Excel. These macros are executed
automatically when the documents that contain them are opened, at which
point they attach themselves to the global template so that they can
infect every document you subsequently open and save. Both Word and
Excel have security features that restrict this feature, but these
measures are clumsy and most people disable them so they can work on the
rest of their documents. In other words, don't rely on the virus
protection built in to Microsoft Office to eliminate the threat of these
types of viruses.
Peer-to-peer (P2P) file sharing
Napster
started the P2P file-sharing craze years ago, but modern file sharing
goes far beyond the trading of harmless music files. It's estimated that
some 40% of the files available on these P2P networks contain viruses,
Trojan horses, and other unwelcome guests, but even these aren't
necessarily the biggest cause of concern. To facilitate the exchange of files, these P2P programs open network ports
and create gaping holes in your computer's firewall, any of which can
be exploited by a variety of worms and intruders. And since people
typically leave these programs running all the time (whether they intend
to or not), these security holes are constantly open for business. But
wait... there's more! If the constant threat of viruses and Trojan
horses isn't enough, many P2P programs themselves come with a broad
assortment of spyware and adware, intentionally installed on your system
along with the applications themselves. Kazaa, one of the most popular
file-sharing clients, is also the biggest perpetrator of this, and the
likely culprit if your system has become infected with spyware. (Note
that other products like Morpheus, BearShare, Imesh, and Limewire do
this, too, just in case you were thinking there was a completely "safe"
alternative.)
Web sites
It may
sound like the rantings of a conspiracy theorist, but even the act of
visiting some web sites can infect your PC with spyware and adware. Not
that it can happen transparently, but many people just don't recognize
the red flags even when they're staring them in the face. Specifically,
these are the "add-ins" employed by some web sites that provide custom
cursors, interactive menus, or other eye candy. While loading a web
page, you may see a message asking if it's OK to install some ActiveX
gadget "necessary" to view the page (e.g., Comet Cursor); here, the
answer is simple: no. Just
as many viruses are written to exploit Microsoft Outlook, most spyware
and adware targets Microsoft Internet Explorer. By switching to a
browser like Firefox, you can eliminate the threat posed by many of
these nasty programs.
|
|
Network and Internet connections
Finally,
your network connection (both to your LAN and to the Internet) can
serve as a conduit for a worm, the special kind of virus that doesn't
need your help to infect your system. Obviously, the most effective way
to protect your system is to unplug it from the network, but a slightly
more realistic solution is to use a firewall. Vista comes with a
built-in firewall, although a router provides much better protection.
1.2. How to protect and clean your PCThe
most popular and typically the most effective way to rid your computer
of malware is to use dedicated antivirus software and antispyware
software. These programs rely on their own internal databases of known
viruses, worms, Trojans, spyware, and adware, and as such, must be
updated regularly (daily or weekly) to be able to detect and eliminate
the latest threats. Vista
is the first operating system to include an antispyware tool, known as
Windows Defender (found in Control Panel and shown in Figure 1).
The best part about it is that, left to its own devices, Windows
Defender will regularly scan your system and even keep its spyware
definitions up to date. 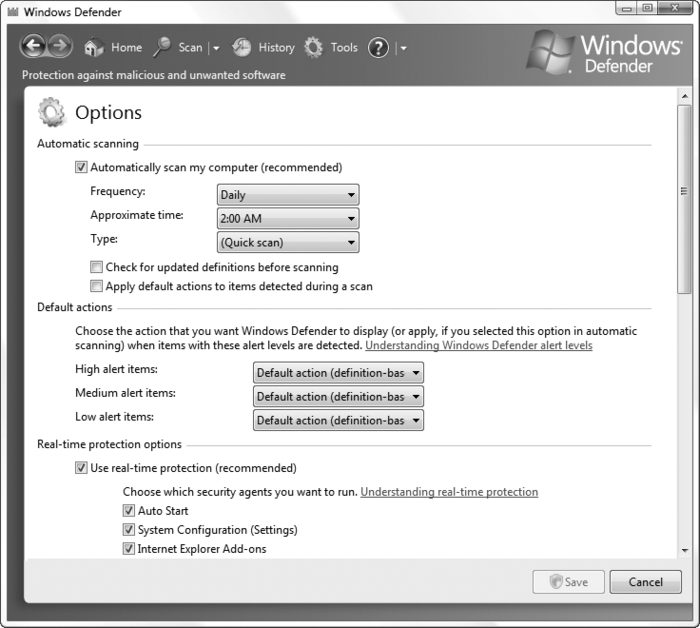
But
Vista still doesn't come with an antivirus tool, mostly to appease the
companies that make money selling aftermarket antivirus software (which
is ironic, since the best tools are free). Following is a list of the
more popular antivirus products.
Avast Home Edition (http://www.avast.com) Freeware, with a slick interface and good feature set.
Avira AntiVir Classic (http://www.free-av.com) Freeware, with frequent updates, but only average detection rates.
AVG Anti-Virus (http://free.grisoft.com) Freeware, a popular yet poor-performing antivirus solution.
Kaspersky Antivirus Personal (http://www.kaspersky.com) Very highly regarded solution with an excellent detection record.
McAfee VirusScan (http://www.mcafee.com) Trusted and well-established all-around virus scanner with an intuitive interface and few limitations.
Panda Anti-Virus Titanium & Platinum (http://www.pandasecurity.com) Lesser-known but capable antivirus software.
Symantec Norton AntiVirus (http://www.symantec.com) Mediocre,
slow antivirus software with a well-known name—but beware of its
expensive subscription plan to keep virus definitions updated.
Antispyware
software is a more complex field, and as a result, you'll have the best
luck using multiple tools in addition to Windows Defender. The top
antispyware products include:
Ad-Aware Personal Edition (http://www.lavasoft.de) Ad-Aware
is one of the oldest antispyware tools around, but its definitions are
still updated frequently. The personal edition is free and very slick,
although it's not usually as effective at removing spyware as Spybot or
Spysweeper, both discussed next. When using Ad-Aware, make sure you click Check for updates now
before running a scan. Also, to turn off the awful, jarring sound
Ad-Aware plays when it has found spyware, click the gear icon to open
the Settings window, click the Tweak button, open the Misc Settings category, and turn off the Play sound if scan produced a result option. |
|
Spybot - Search & Destroy (http://www.spybot.info) Not quite as nice to look at as Ad-Aware, Spybot excels at purging hard-to-remove spyware. And while both Ad-Aware and Spybot remove tracking cookies from Internet Explorer, Spybot supports Firefox as well.
Spy Sweeper (http://www.webroot.com) This
highly regarded antispyware tool, while not free like the first two, is
still a welcome addition to any spyware-fighter's toolbox, and can
often remove malware that the others miss.
So,
armed with proper antivirus and antispyware software, there are four
things you should do to protect your computer from malware: Place a router between your computer and your Internet connection. Scan
your system for viruses regularly, and don't rely entirely on your
antivirus program's auto-protect feature (see the next section). Run a
full system scan at least every two weeks. Scan
your system for spyware regularly, at least once or twice a month. Do
it more often if you download and install a lot of software. Use
your head! See the previous section for ways that malware spreads, and
the next section for some of the things you can do to reduce your
exposure to viruses, spyware, adware, and other malware.
1.3. The perils of auto-protectAntivirus
software is a double-edged sword. Sure, viruses can be a genuine
threat, and for many of us, antivirus software is an essential
safeguard. But antivirus software can also be a real pain in the neck. The
most basic, innocuous function of an antivirus program is to scan files
on demand. When you start a virus scanner and tell it to scan a file or
a disk full of files, you're performing a useful task. The problem is
that most of us don't remember or want to take the time to routinely
perform scans, so we rely on the so-called "auto-protect" feature, where
the virus scanner runs all the time. This can cause several problems:
Performance hit
Loading
the auto-protect software at Windows startup can increase boot time;
also, because each and every application (and document) you open must
first be scanned, load times can increase. Plus, a virus scanner that's
always running consumes memory and processor cycles, even though you're
not likely to spend most of your time downloading new, and potentially
hazardous, files for it to scan.
Browser and email monitoring
Some
antivirus auto-protect features include web browser and email plug-ins,
which scan all files downloaded and received as attachments,
respectively. In addition to the performance hit, these plug-ins
sometimes don't work properly, inadvertently causing all sorts of
problems with the applications you use to open these files.
Annoying and obtrusive messages
The
constant barrage of virus warning messages can be annoying, to say the
least. For instance, if your antivirus software automatically scans your
incoming email, you may be forced to click through a dozen or so
messages warning you of virus-laden attachments, even though your spam
filter will likely delete them before you ever see them. And nearly
every antivirus program makes a big show each time it receives
definition updates; while it's nice to know the software is doing its
job, it would also be nice to have it do it quietly.
False sense of security
Most
importantly, having the auto-protect feature installed can give you a
false sense of security ("Sure, I'll open it—I have antivirus
software!"), reducing the chances that you'll take the precautions
listed elsewhere in this section and increasing the likelihood that your
computer will become infected. Even if you are diligent about scanning
files manually, no antivirus program is foolproof, and is certainly no
substitute for common sense.
Now,
if you take the proper precautions, your exposure to viruses will be
minimal, if not nil, and you will have very little need for the
auto-protect feature of your antivirus software. Naturally, whether you
disable your antivirus software's auto-protect feature is up to you, but
if you keep the following practices in mind, you should be able to
effectively eliminate your computer's susceptibility to viruses. If
you don't download any documents or applications from the Internet, if
you're not connected to a local network, if you have a firewalled
connection to the Internet, and the only type of software you install is
off-the-shelf commercial products, your odds of getting a virus are
pretty much zero. Viruses can only reside in certain types of files, including application (.exe and .scr) files, document files made in applications that use macros (such as Microsoft Word), Windows script files (.vbs), and some types of application support files (.dll, .vbx, .vxd, etc.). And because ZIP files can contain any of the aforementioned files, they're also susceptible. Conventional wisdom holds that plain-text email messages, text files (.txt), image files (.jpg, .gif, .bmp, etc.), video clips (.mpg, .avi,
etc.) and most other types of files are benign in that they simply are
not capable of being virus carriers. However, things aren't always as
they seem. Case in point: the Bloodhound.Exploit.13
Trojan horse (discovered in 2004) involved certain JPG files and a flaw
in Internet Explorer (and most other Microsoft products). The bug has
since been fixed, but it's not likely to be the last. Actually,
it is possible to embed small amounts of binary data into image files,
which means, theoretically, that an image could contain a virus.
However, such data would have to be manually extracted before it could
be executed; a virus embedded in an image file would never be able to
spontaneously infect your system. |
|
You've
heard it before, and here it is again: don't open email attachments
sent to you from people you don't know, especially if they are Word
documents or .exe files. If someone sends you an attachment and you're tempted to open it, scan it manually beforehand, and then refrain from opening it.
Most antivirus software adds a context-menu item to all files, allowing
you to scan any given file by right-clicking on it and selecting Scan (or something similar). If
you're on a network, your PC is only as secure as the least-secure PC
on the network. If it's a home network, make sure everyone who uses
machines on that network understands the concepts outlined here. If it's
a corporate network, there's no accounting for the stupidity of your
coworkers, so you may choose to leave the auto-protect antivirus
software in place.
|