Managing change in any network is a daunting task.
You have to really know what is happening to be able to understand how
your network evolves with use. In Windows, the best way to find out what
is going on is to audit all system and user activity. The only way to
do this is to use a two-part approach. First, you must create an audit
policy. Second, you have to indicate which objects and which users you
want to audit.
1. Turning on the audit policy
You need to turn on the audit policy. Do this by
using either the Local Security Policy or through central Group Policy.
Use the Local Security Policy if you want to audit a single computer or
if it is part of a workgroup. If you have more than one system, then
use Group Policy. That's because it provides centralized policy
deployment to multiple systems — create the policy once and deploy it to
any number of systems.
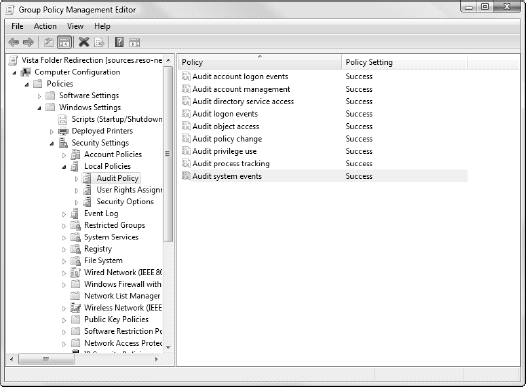
Despite the fact that Vista now brings 800 new
settings to Group Policy management, the audit policies have not
changed. Vista allows you to audit nine different types of events just
as you could in Windows XP and Windows Server 2003, as shown in Figure 1.
Whether you use Group Policy or the LSP, you need to turn on each of
the events you want to monitor. Use the following process:
Click Start Menu, Search, type GMPC.MSC, and press Enter. Accept the UAC prompt.
After
the GPMC is launched, expand the Forest to view all subitems in the
Tree pane. Navigate to the Default Domain Policy, right-click on it, and
select Edit. The Default Domain Policy is used because it applies to every system in the network.
In GPEdit, choose Computer Configuration =>
Windows Settings =>
Security Settings =>
Local Policies =>
Audit Policy.
Double-click each setting to modify it.
Modify the settings as appropriate. To learn more about each setting, click on the Explain tab in the setting's dialog box.
Preparing the policy, local or central, is only
the first part of the auditing process. The second step is to change the
security descriptor of the items you want to audit. For example, to
audit file access on a given shared folder, you need to:
Right-click the shared folder and select Properties.
Select the Security tab, click the Advanced Security button, and move to the Audit tab.
Select whom you want to audit.
Fortunately, you can use groups to monitor the
activities of all the users in your organization, which makes it simpler
to assign. You must repeat this activity on each server or workstation
you want to monitor and for each object you need to watch.
Audited events are recorded in the Security
Event Log and can be seen through the Event Viewer. Because events are
recorded locally on each system that is affected, you need to visit each
and every system to obtain a global picture of events on your network.
Doing this is a bit tedious if you don't have an event collection
mechanism — or a system that automatically collects key events and
forwards them to a central location. Fortunately, Vista can also collect
events.
Vista's Event Log can now automatically act on
events and send them to a central location, which can be another Vista
system or a server running Windows Server 2008. In addition, you'll soon
discover that the Event Log now records a host of events that were
unheard of in previous versions of Windows.
In these previous versions, Microsoft used a
number of different mechanisms to record events. Many products and
subfeatures of Windows recorded information in their own logs as if they
didn't even know the Event Log existed. It's no wonder that most
administrators didn't even bother to verify any logs unless an untoward
event occurred and they were spurred on by others: security officers,
for example. It was just too much work. With Vista, most of these tools
now record events properly and store them into the Event Log. This is
bound to make your life easier, but of course, only when all your
systems have been upgraded to Vista.
2. Exploring the Vista Event Log
For Windows Vista, Microsoft scrapped all of its
previous Windows code and started from scratch to rewrite the whole
thing. With all the security issues Windows had been facing in the past
few years, rewriting the code with security in mind was a must. But this
approach also provides added benefits. For example, when Microsoft
programmers were working on the Vista Event Log, not only did they
rewrite the code, but they also took advantage of the opportunity to
give it a complete overhaul. The new Vista Event Log sports a new
interface and a significant number of new event categories making it
much more useful than ever before. It now includes the following new
features:
The Event Viewer interface
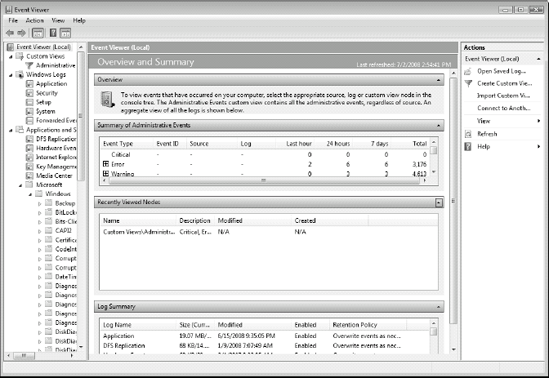
The first thing you'll notice when you launch
the Event Viewer in Windows Vista is the new look and feel. When you
first open it, the Event Viewer presents its summary view. The new Event
Viewer lays out its contents into three panes, as shown in Figure 2,
because it is based on the Microsoft Management Console version 3.0.
The left pane is still the tree view which will be familiar to most
Windows technicians. It includes several nodes: Custom Views, Windows
Logs, Applications and Services Logs, and Subscriptions. The center pane
is as it was before: the details pane. When the focus is on the Event
Viewer node, you see a summary view which lists all events according to
importance as well as audited events. Finally, the right pane lists
actions you can perform. Like context menus, the contents of this action
pane will change with the views you select.
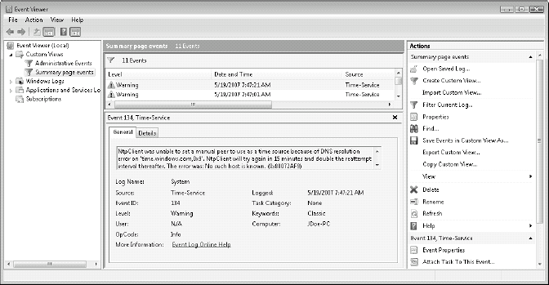
When you change views, for example, when you
focus on a specific log and view the events it contains, the details
pane becomes your Event Viewer, showing the actual contents of events
without having to open each event and having to juggle windows to try to
see event listings at the same time as you see event details as shown
in Figure 3. This makes it much easier to work with events.
New event categories
Another major improvement of the Event Log is
that it is now designed to collect every single event on the system.
Although previous versions of Windows stored event information in
different locations — databases, flat files, event logs — Vista now
stores all events in the Event Log. Therefore, it now includes a whole
series of new event categories. These are located under the Applications
and Services Logs node in the tree pane. Perhaps the most important
change is in the Microsoft sub-node. This sub-node now includes 53
different categories under the Windows sub-node. Each category is
focused on a specific service within Windows — BitLocker, Event
Collector, Group Policy, User Access Control, and much more.
Subcategories are listed for each — administrative, operational,
analytic and so on — making it very easy to drill down deep into any
issue.
In addition, each application that is
Vista-ready will store its events inside this event category. Windows
includes its own — Distributed File System (DFS) Replication, Hardware
Events, Internet Explorer, Key Management Service, and Media Center.
Third-party applications also store their events here. This proves that
the Event Log is now the one and only store for events in Vista.
New event filters
In addition, in the Custom Views node under the
tree pane, you see that Vista already includes a custom view: the
Administrative Events view. This view is based on a filter as shown in Figure 9.17
and is used to automatically collect events that are of interest to
system administrators, saving you from having to generate your own
filters. Because this is a default view, this filter is read-only, but
you have full flexibility to create other filters based on any event
attribute.
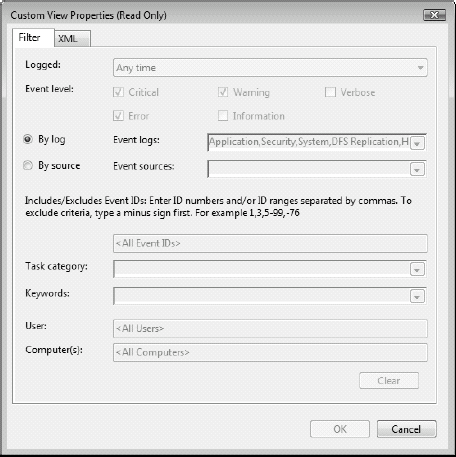
The filters can be based on a whole series of
attributes. Logged time is one of the first attributes you can focus on
with six predefined time periods and the ability to create your own
custom time period. Event level is next, letting you select critical,
errors, warning, verbose, or information events. Then, you can filter
either by log or by source. By log gives you a tree pane that lets you
check the logs you need. Source lets you select any potential event
source. Finally, you can filter by event ID, tasks that may be
associated with the event, keywords contained inside the event, user,
and computer generating the event.
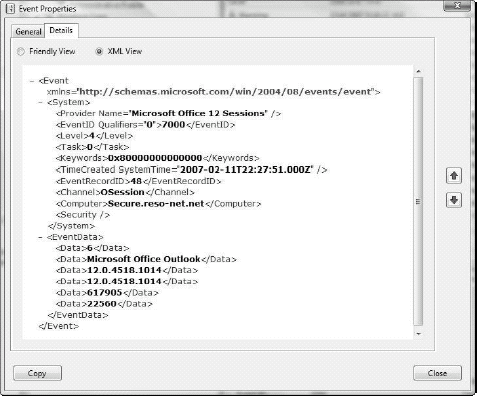
New event language: XML
Filtering is now so powerful because Vista
events are now completely structured, using an Extended Markup Language
(XML) structure. Previous versions of Windows provided some structure
for event reporting, but it was mostly only evident to programmers using
the Win32 application programming interface. With Vista, everything
changes because they rely on XML with a published schema as shown in Figure 5.
Each event now includes an XML description, which makes filtering out
events (that might be considered garbage) much easier and lets you focus
on the events that are of interest to you. This filtering strategy will
go a long way toward making it easier to audit change and manage
systems running Windows Vista.
New event command line
For those who love the command line, you won't
be disappointed with the new Event Log. Vista includes a new command
that is designed to let you manage and administer events in character
mode:
wevtutil.exe
Wevtutil, for Windows Event Utility,
includes a whole series of functions and switches, all aimed at event
management. For example, you can find out all of the publishers who are
registered on a system. That's because with the new Event Log,
publishers must register themselves on the system. Wevtutil lists not
only publishers but also their configuration on the system and all of
the events they might log on a system. Nobody can hide from
administrators anymore!
Wevtutil will also let you install or uninstall
event manifests, run queries against events, export and archive logs as
well as clear them, all from the command line. If you're into the
command line, then take the time to explore this powerful new tool.
As you can see, the Event Viewer is considerably
different from previous versions of Windows, even at just the interface
level. But that's not all. With Vista, you can integrate events with
tasks, you can automate tasks based on events, and you can forward key
events to central locations.