5. Layer 5: Working with external access
The final layer of defense involves external
access. In PC terms, this means working with the way PCs access your
resources when outside your network. As such, this means working with
the following items:
Windows Firewall with Advanced Security
Virtual Private Network (VPN) Connections
Public Key Infrastructures
Network Access Protection
Each of these is discussed here as they apply to PCs.
5.1 Working with the Windows Firewall with Advanced Security
Vista includes a powerful firewall that helps
protect each individual PC running it. In fact, it includes two
different firewall products. The first is a basic firewall that focuses
on whether or not protection is turned on. The second is a much more
comprehensive tool that is once again managed through Group Policy.
Like Windows Defender, the Basic Firewall is accessed through the Security Center (Control Panel => Security =>
Security Center), just click the link in the left pane to launch the
Firewall. You'll also remember that the firewall comes up immediately
after you install Windows Vista as part of the initial security
configuration of your PC. Of course, you need administrative credentials
to view or modify its settings.
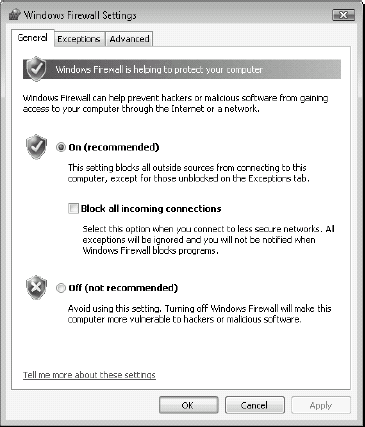
As shown in Figure 10,
the basic firewall has two main settings: On or Off. You should keep it
on at all times. There are also two additional tabs for basic firewall
configuration. Exceptions list the type of exceptions you can set on the
firewall. Firewalls basically control which of the 65,000 TCP/IP ports
are open or not on your machine. You can of course manage the firewall
at the port level if you want (just click the Add port button), but it
is much easier to manage it at the application level. You want to be
able to make Remote Assistance connections to a PC and then allow the
application in the basic firewall settings.
Many applications will be Windows Firewall aware
— in fact, you should make sure that each application you choose is
Firewall aware — and will automatically make the appropriate changes in
the firewall when installed. Being Firewall aware is part of the Windows
Logo compliance settings Microsoft publishes for independent software
vendors so that they can make their applications as compatible to Vista
as possible.
The last tab is the Advanced tab. This tab lets
you configure different Firewall settings for different network
connections if they exist. You need to make sure the Basic Firewall is
turned on at all times.
The best way to ensure your firewall is turned
on at all times is to use the Windows Firewall with Advanced Security
(WFAS). This firewall control center is accessed through Group Policy
(Computer Configuration => Policies => Windows Settings => Security Settings => Windows Firewall with Advanced Security). As shown in Figure 11, WFAS provides much more comprehensive control over firewall behavior.
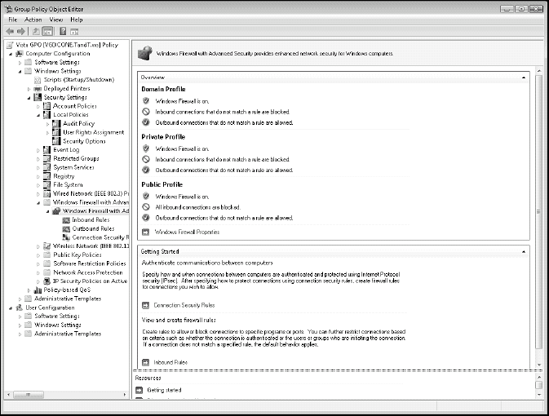
The first thing you will notice is the network
profiles associated with the firewall. Each time Windows Vista connects
to a network, it identifies what kind of network you are connecting to.
Three choices are possible from the end user point of view: Private,
Public, and Home.
Vista configures the firewall settings for the
network depending on the choice made by the user. Private networks allow
some connections as do Home networks. But Public networks are very
restrictive and do not allow inbound connections. For this reason, you
should instruct your users to always select Public network when they
connect to an unknown network. When they do so, Vista will create the
most restrictive connection, protecting their PC from potential
malicious content.
WFAS, however, includes one different network
profile, the Domain profile. The Domain profile controls firewall
behavior when the system is connected to your network. This feature is
what makes WFAS so much more comprehensive than the Basic Firewall:
being able to control the behavior of the Firewall based on the type of
connection profile it is using.
As shown in Figure 11,
the Firewall state is not configured by default. You should configure
these settings for each of the three profiles even if they are not
currently in use. By taking this step, you ensure that your PCs are
protected no matter what happens. The three profiles include:
Domain:
This profile applies when the computer is connected to the network
containing an Active Directory with the computer's account, normally
your own network.
Private:
This profile applies when the computer connects to a network that does
not contain its account, for example a home network that runs through a
Workgroup.
Public: This profile applies when the computer connects to an unknown network such as one in airports or coffee shops.
The configurations you should apply in WFAS
should become more and more restrictive as you work through the
profiles. To configure the settings for each profile, follow these
steps:
Launch the Group Policy Management Console by choosing Start Menu =>
Search =>
gpmc.msc.
Locate a GPO that applies to all systems. This GPO should be assigned to the PCs OU, right-click it, and select Edit.
Navigate to the WFAS by choosing Computer Configuration =>
Policies =>
Windows Settings =>
Security Settings =>
Windows Firewall with Advanced Security), expand its contents, and click the Windows Firewall with Advanced Security subnode.
In the Details pane, click Windows Firewall Properties under the list of profiles.
Begin with the Domain Profile. At the very least, use the Recommended and Default settings, as shown in Figure 12. The Firewall should be turned on, Inbound connections should be Blocked unless explicitly allowed, and Outbound connections should be Allowed.
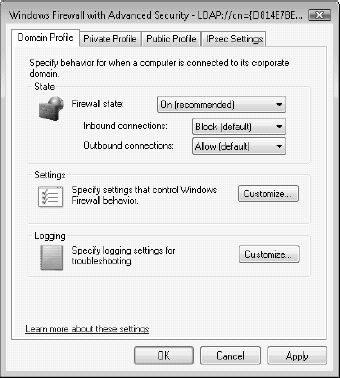
Click
the Customize button under Settings to open a second dialog box that
displays several settings. Once again, select the Defaults at the very
least.
It is a good idea to display notifications, so that users will know when a program is attempting a connection that is blocked.
Allow
Unicast responses because this option will let the system wait up to
three seconds for a response. After three seconds, all responses will be
blocked. Note that this does not affect DHCP responses, which are
always allowed.
Allow local firewall rules only if you want to allow non-GPO rules to apply to the PC as well. The default is to allow them.
Allow
local connection security rules only if you want to allow non-GPO rules
to apply to be defined on the PC as well. The default is to allow them.
In
most cases, you should set only GPO rules. Although allowing local
rules can be convenient when you configure a new application on a PC, it
can become quite cumbersome when you are troubleshooting a
non-functioning device. If you want to test new applications, do it in a
test environment, not in your production network.
Repeat the operation for the Private and Public tabs.
The last tab focuses on IPsec Settings.
Click the Customize button to modify these settings. These settings
deal with secure connections from the PC to other systems. Each of the
settings in this dialog box is set to defaults. This means that some
form of IPsec is turned on by default. To view the default values, click
on the What are the default values?
link at the bottom of the dialog box. You can change each setting by
clicking on Advanced and then the Customize button. Click on OK when done.
NOTE
Make sure you verify with your server
administrators to coordinate these settings with them. IPsec will be
configured on the server as well as on the PC and settings must match
for the connection to occur properly.
If you do modify the IPsec
settings, you can also allow exemptions for ICMP from IPsec. This means
you could use the PING utility to identify if a computer is awake or
not. While this might be useful inside your network, it is definitely
not a good idea for portable systems that travel outside your network.
The best bet is to leave it off.
Click OK to apply the changes to the profiles.
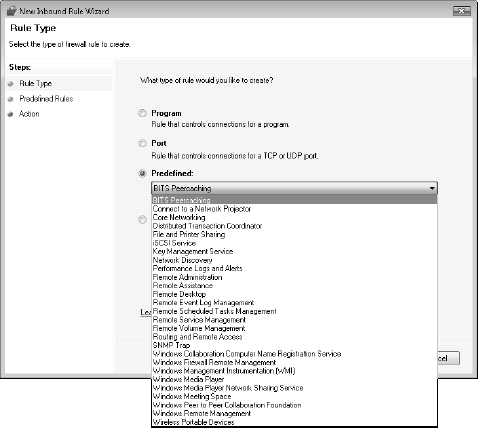
You can also create Inbound, Outbound and
Connection Security Rules for your systems. Each node uses a wizard to
generate the rule, as shown in Figure 13.
Once again, it is easiest to base rules on programs rather than ports.
You can also rely on the Predefined rules that come with the Firewall.
Use custom rules only if you have a specific unknown program to install.
The best way to create Inbound, Outbound, or
Connection Security Rules is to work with both Firewalls. Do this
through the following steps:
Set up a PC using a typical configuration.
Enable all of the applications you deem necessary for this PC. This may include items such as Remote Assistance, Remote Desktop, and Windows Remote Management among others.
Open the Windows Firewall through Control Panel and move to the Exemptions tab.
Go to your GPO and apply each of the rules found in the Exemptions tab of the Basic Firewall to your Group Policy.
Test the policy before deploying it.
This approach will let you more easily configure
the Group Policy and it will ensure your systems are working as they
should while protecting them from malicious connections.
NOTE
Virtual Private Network connections rely on
IPsec to connect to the system. WFAS allows you to configure both the
Firewall and IPsec in the same integrated environment. If you are
relying on Windows Server to create the VPN connections, then work with
your server team to properly configure these settings. If you are using a
third-party VPN tool, then look up the appropriate client from the list
found at http://support.microsoft.com/kb/929490.