Your first line of
defense in securing your computer is to protect it from attacks by
outsiders. Once your computer is connected to the internet, it becomes
just another node on a huge global network. A firewall
provides a barrier between your computer and the network to which it's
connected by preventing the entry of unwanted traffic while allowing
transparent passage to authorized connections.
Using a firewall is
simple, essential, and often overlooked. You'll want to be sure that all
network connections are protected by a firewall. You might be comforted
by the knowledge that your portable computer is protected by a
corporate firewall when you're at work and that you use a firewalled
broadband connection at home. But what about the public hot-spots you
use when you travel?
And it makes sense to run a firewall on your computer (sometimes called a personal firewall)
even when you're behind a residential router or corporate firewall.
Other people on your network might not be as vigilant as you are about
defending against viruses, so if someone brings in a portable computer
infected with a worm and connects it to the network, you're toast—unless
your network connection has its own firewall protection.
Warning:
This bears repeating. In today's environment, you should run firewall software
on each networked computer; don't rely on corporate gateway firewalls
and gateway antivirus solutions to protect your computer from another
infected computer inside the perimeter. Although it's not a good idea to
run more than one software firewall on a computer, you should run a
software firewall as an extra layer of protection behind your hardware
firewall.
Windows includes
a two-way stateful-inspection packet filtering firewall called,
cleverly enough, Windows Firewall. Windows Firewall is enabled by default for all connections, and it begins protecting your computer as it boots. The following actions take place by default:
The firewall
blocks all inbound traffic, with the exception of traffic sent in
response to a request sent by your computer and unsolicited traffic that
has been explicitly allowed by creating a rule.
All outgoing traffic is allowed unless it matches a configured rule.
You notice nothing if a packet is dropped, but you can (at your option) create a log of all such events.
Note:
Some people wonder why Windows Firewall, unlike some third-party firewalls, doesn't block outbound
traffic by default. You'll find security experts on both sides of this
argument, but the reason is that Windows Firewall is designed to protect
and maintain a secure computer. If malware is making outbound
connections, your computer has already been compromised.
(The misbehaving program should be caught by your antivirus or
antispyware defenses.) Blocking outbound traffic by default would
generate many pop-up warning messages (because so many programs
legitimately connect to the internet or other network computers), which
some experts feel would greatly dilute their significance, causing many
users to simply ignore them.
|
Most firewalls work, at least in part, by packet filtering—that
is, they block or allow transmissions depending on the content of each
packet that reaches the firewall. A packet filter examines several
attributes of each packet and can either route it (that is, forward it
to the intended destination computer) or block it, based on any of these
attributes:
Source address The IP address of the computer that generated the packet Destination address The IP address of the packet's intended target computer Network protocol The type of traffic, such as Internet Protocol (IP) Transport protocol The higher level protocol, such as Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) Source and destination ports The number that communicating computers use to identify a communications channel
Packet filtering alone is an
inadequate solution; incoming traffic that meets all the packet filter
criteria could still be something you didn't ask for or want. Stateful-inspection packet filtering
goes a step further by restricting incoming traffic to responses to
requests from your computer. Here's a simplified example of how
stateful-inspection filtering works to allow "good" incoming traffic:
You enter a URL in your browser's address bar. The
browser sends one or more packets of data, addressed to the web server.
The destination port is 80, the standard port for HTTP web servers; the
source port is an arbitrary number from 1024 through 65535. The firewall saves information about the connection in its state table, which it will use to validate returning inbound traffic. After
the web server and your computer complete the handshaking needed to
open a TCP connection, the web server sends a reply (the contents of the
webpage you requested) addressed to your computer's IP address and
source port. The
firewall receives the incoming traffic and compares its source and
destination addresses and ports with the information in its state table.
If the information matches, the firewall permits the reply to pass
through to the browser. If the data doesn't match in all respects, the
firewall silently discards the packet. Your browser displays the received information.
|
Compared with the firewall included in Windows XP, Windows Firewall has been enhanced in several ways:
Windows Firewall supports monitoring and control of both incoming and outgoing network traffic.
Through
its Windows Firewall With Advanced Security console, Windows Firewall
provides far more configuration options, and it can be configured
remotely. A new wizard makes it easier to create and configure rules.
Configuration of Internet Protocol security (IPsec)—a mechanism that
provides for authentication, encryption, and filtering of network
traffic—is also done in the Windows Firewall With Advanced Security
console.
In
addition to the usual criteria (addresses, protocols, and ports),
firewall rules can be configured for services, Active Directory accounts
and groups, source and destination IP addresses for incoming and
outgoing traffic, transport protocols other than TCP and UDP, network
connection types, and more.
Windows
Firewall maintains three separate profiles, with the appropriate one
selected depending on whether the computer is connected to a domain, a
private nondomain network, or a public network.
Note that, if you use Windows
XP Mode, the virtual machine should have its own firewall enabled.
Because the virtual machine runs Windows XP Service Pack 3 (SP3), it
uses the Windows XP firewall. For more information about XP Mode.
|
Windows Firewall is designed to be compatible with firewall programs from third-party
providers. When you install a third-party firewall, it can register
itself to take ownership of and manage certain firewall categories, such
as port blocking, IPsec policy, and boot-time policy. The third-party
program reports its status in Action Center, just as Windows Firewall
does.
Even if you have a
third-party firewall, you should leave Windows Firewall turned on and
leave the Windows Firewall service set to run automatically. This is
needed to enforce IPsec policies, and it also ensures that Windows
Firewall continues to manage any categories that are not protected by
the third-party program.
|
1. Using Windows Firewall in Different Network Locations
Windows Firewall
maintains a separate profile (that is, a complete collection of
settings, including rules for various programs, services, and ports) for
each of three network location types:
Domain
Used when your computer is joined to an Active Directory domain. In
this environment, firewall settings are typically (but not necessarily)
controlled by a network administrator.
Private Used when your computer is connected to a home or work network in a workgroup configuration.
Public
Used when your computer is connected to a network in a public location,
such as an airport or library. It's common—indeed, recommended—to have
fewer allowed programs and more restrictions when you use a public
network.
If you're simultaneously
connected to more than one network (for example, if you have a Wi-Fi
connection to your home network while you're connected to your work
domain through a virtual private network, or VPN, connection), Windows
uses the appropriate profile for each connection with a feature called multiple access firewall profiles
(MAFP). (This is not the case in Windows Vista. That operating system
uses the most restrictive applicable profile whenever you connect to
multiple networks at the same time.)
You make settings
in Windows Firewall independently for each network profile. The
settings in a profile apply to all networks of the particular location
type to which you connect. (For example, if you allow a program through
the firewall while connected to a public network, that program rule is
then enabled whenever you connect to any other public network. It is not
enabled when you're connected to a domain or private network, unless
you allow the program in those profiles.)
2. Managing Windows Firewall
Windows Firewall is a
Control Panel application that provides a simple interface for
monitoring firewall status and performing routine tasks, such as
allowing a program through the firewall or blocking all incoming
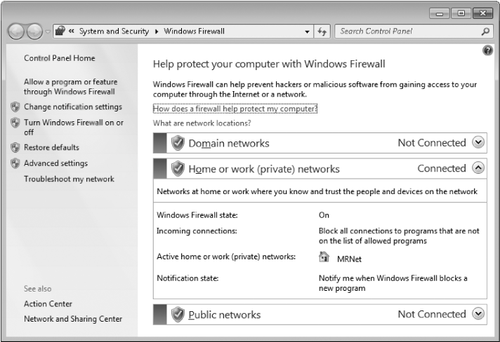
connections. To open Windows Firewall, type firewall in the Start menu search box or in Control Panel. Click Windows Firewall to display a window similar to the one shown in Figure 1.
3. Enabling or Disabling Windows Firewall
The main Windows Firewall application, shown in Figure 1,
is little more than a status window and launchpad for making various
firewall settings. The first setting of interest is to enable or disable
Windows Firewall. To do that, click Turn Windows Firewall On Or Off to
open the screen shown next. From here you can enable (turn on) or
disable (turn off) Windows Firewall for each network type. In general,
the only reason to turn off Windows Firewall is if you have installed a
third-party firewall that you plan to use instead of Windows Firewall.
Most of those, however, perform this task as part of their installation.
As you'll discover
throughout Windows Firewall, domain network location settings are
available only on computers that are joined to a domain. You can make
settings for all network location types—even those to which you're not
currently connected. Settings for the domain profile, however, are often
locked down by the network administrator using Group Policy.
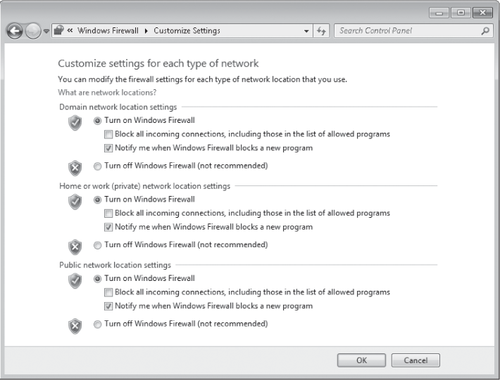
The Block
All Incoming Connections check box in Customize Settings provides
additional safety. When it's selected, Windows Firewall rejects all
unsolicited incoming traffic—even traffic from allowed programs or that
would ordinarily be permitted by a rule. (For information about
firewall rules, see Section 15.4.4
on the next page.) Invoke this mode when extra security against outside
attack is needed. For example, you might block all connections when
you're using a public wireless hotspot or when you know that your
computer is actively under attack by others.
Note:
Selecting Block
All Incoming Connections does not disconnect your computer from the
internet. Even in this mode, you can still use your browser to connect
to the internet. Similarly, other outbound connections—whether they're
legitimate services or some sort of spyware—continue unabated. If you
really want to sever your ties to the outside world, open Network And
Sharing Center and disable each network connection. (Alternatively, use
brute force: physically disconnect wired network connections and turn
off wireless adapters or access points.)