One of the great strengths of mobile computers is
their ability to connect to wireless networks. Today, most mobile
computers come with built-in wireless capabilities, and you can connect
to wireless networks within the company and in public places.
Windows 7 supports all the
standard wireless protocols. If your wireless devices and wireless NICs
support it, so does Windows 7. This includes 802.11a, 802.11b, 802.11g,
and 802.11n. Windows 7 also supports the newer WPA2 authentication
options that significantly improve wireless network security. In this
section, you'll learn about
Using wireless security
Configuring wireless on Windows 7
Connecting to a wireless network
Troubleshooting wireless connections
1. Using Wireless Security
When wireless networks
were first designed, the primary goal was ease of use. The designers
wanted to make it easy to discover, connect to, and use wireless
networks. They did a great job. However, security was more of an
afterthought.
They came up with Wired Equivalent Privacy (WEP)
to provide the same level of privacy for a wireless network as you'd
have in a wired network. Unfortunately, WEP had significant problems and
was later cracked. Attackers could download software from the Internet
and easily crack WEP-protected networks.
Wi-Fi Protected Access (WPA)
is the first improvement over WEP. One of the primary benefits of WPA
is that it is compatible with most of the same hardware that used WEP.
WPA was intended to be an interim fix for WEP until a more permanent
solution was identified. Although WPA is more secure than WEP, attackers
have cracked it.
Wi-Fi Protected Access 2 (WPA2)
is the permanent fix for WEP. It is also known as 802.11i. If you have a
choice among WEP, WPA, and WPA2, use WPA2. WPA2 provides the strongest
security.
|
WEP is not recommended
for use today. You should use at least WPA, but use WPA2 whenever
possible. WEP is easy to crack. Even though WPA has vulnerabilities, it
isn't as vulnerable as WEP.
|
|
When configuring Windows 7
to connect to a wireless network, you should have an understanding of
the security types and encryption types available. First, it's important
to understand what each of these is doing:
Security type
The security
type identifies the type of authentication used. Authentication is used
to verify a client prior to allowing access.
Encryption type
After the client connects,
the data can be encrypted. This provides confidentiality by preventing
others from being able to read the data. Advanced Encryption Standard
(AES) is a strong, efficient encryption algorithm. WEP can also be
selected as an encryption type for some security types. However, WEP is
the weakest.
Consider Figure 1.
It shows the security settings for a wireless profile named
WileyNetwork. As you can see, it is using the WPA2-Enterprise security
type and AES as the encryption type. These are the strongest settings
available.
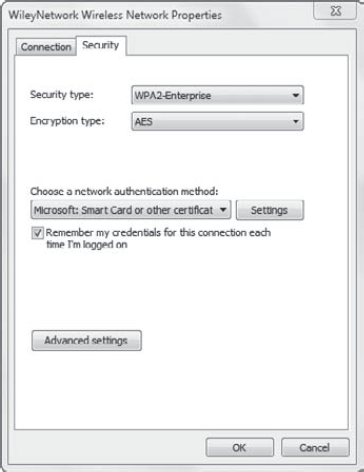
This figure also shows the
Choose A Network Authentication Method drop-down box. These selections
are available only for the WPA-Enterprise and WPA2-Enterprise security
types. The Microsoft: Smart Card Or Other Certificate option (selected
in the figure) is the strongest authentication method available. You can
also choose the Microsoft: Protected EAP (PEAP) authentication method.
It's important to realize that
you must match these settings to the wireless network. In other words,
if your network is using a wireless access point with WPA2-Personal, you
must configure Windows 7 to use WPA2-Personal. Otherwise, the Windows 7
system won't connect.
Windows 7 supports the following security types:
- No Authentication (Open)
This uses no authentication. It is not recommended for use in a production environment but can be used for testing.
You can select either WEP or
None for encryption. If you select WEP, you also need to enter a
pre-shared key (PSK). This is also known as a password or passphrase.
You need to enter the same PSK on the Windows 7 system as is used on the
wireless device.
- Shared
Shared uses a PSK for
authentication and WEP for encryption. WEP uses the same PSK that you
enter for authentication. Shared is not recommended for use in a
production environment but can be used for testing. It is marginally
better than No Authentication (Open) but can be easily cracked.
- WPA-Personal
WPA-Personal uses a pre-shared key for authentication. This PSK provides limited authentication.
You can select either
Advanced Encryption Standard (AES) or Temporal Key Integrity Protocol
(TKIP) for encryption. TKIP is compatible with older hardware, but AES
is preferred if your hardware supports it.
- WPA-Enterprise
WPA-Enterprise
is similar to WPA except that it uses an 802.1x server for
authentication. The 802.1x server will distribute the keys to each
client instead of the clients using a PSK. It can also use either smart
cards or Protected Extensible Authorization Protocol (PEAP) for
authentication. Smart cards provide better security, but they also
require more resources on your network. For example, you must have a
Public Key Infrastructure (PKI) to issue certificates for the smart
cards.
You can select either AES or TKIP for encryption. AES is preferred.
- WPA2-Personal
WPA2-Personal
is similar to WPA-Personal except it uses the stronger WPA2
authentication instead of WPA. WPA2-Personal uses a PSK. You enter the
same PSK on the Windows 7 system and the wireless devices.
You can select either AES or TKIP for encryption. AES is preferred.
- WPA2-Enterprise
WPA2-Enterprise
is the strongest security type available with Windows 7. It uses an
802.1x server for authentication just as WPA-Enterprise does. It can use
either smart cards or PEAP for authentication. Smart cards provide the
best authentication.
You can select either AES or TKIP for encryption. AES is preferred.
- 802.1x
The 802.1x security
type was intended to provide better protection for WEP by providing a
better authentication mechanism when WEP was used. With WEP no longer
recommended, this is also not recommended.
802.1x uses WEP for encryption.
|
There's an important
distinction when using 802.1x servers. The 802.1x security type is not
recommended because it uses WEP, and WEP is not secure. However,
WPA-Enterprise and WPA2-Enterprise both use 802.1x servers.
WPA2-Enterprise provides the best security, and it is recommended for
use in enterprise environments.
|
|
Both WPA and WPA2 can use
either Personal or Enterprise mode. When Personal is used (as in
WPA-Personal or WPA2-Personal), it uses a pre-shared key (PSK). This PSK
can be a password or passphrase. When Enterprise is used (as in
WPA-Enterprise or WPA2-Enterprise), an 802.1x server is used.
2. Configuring Wireless on Windows 7
You can configure a Windows 7
computer to work with three different wireless configurations. You can
connect to wireless access point or a wireless router in a network. You
can also configure a Windows 7 system to connect to an ad hoc network.
2.1. Wireless Access Point
A wireless access point (WAP)
can be used to provide access from a wireless device to a wired
network. WAPs are commonly used in larger networks to provide this
access.
Figure 2
shows how a Windows 7 system can connect to a WAP in a network. Once
the Windows 7 system is connected, it can access resources in the
network just as if it were a wired computer.
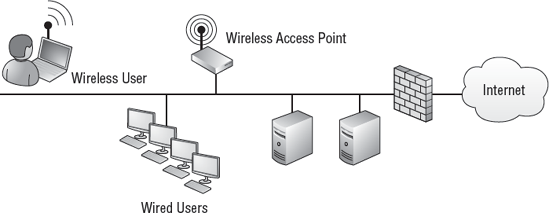
The wireless client will be
able to connect to servers in the network. If other clients have
Internet access, the wireless client will also have Internet access.
2.2. Wireless Routers
A wireless router is a WAP with additional capabilities. Many small offices, home offices (SOHOs) and home users commonly use a wireless router. Figure 3 shows how a wireless router can be used to provide connectivity for users in a network.
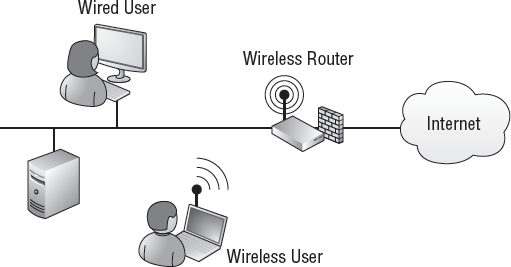
The wireless client is able to
connect to the wireless router and have access to the same resources as
the wired user. Notice how the router has connectivity with the
Internet. On the Internet side, it would have a public IP address issued
from the Internet service provider. On the internal network side, it
would have a private IP address. In addition to being a router, it would
also have network address translation (NAT) capabilities to translate
the internal private IP addresses to external public IP addresses.
Most wireless routers also have
DHCP capabilities. DHCP is used to issue TCP/IP configuration to
internal clients. This includes IP addresses, subnet masks, default
gateway addresses, DNS addresses, and more.
2.3. Ad Hoc Network
Ad hoc
is a Latin phrase that essentially means "as needed." An ad hoc network
is a wireless network without a wireless access point or wireless
router. Imagine that you and a friend or two want to connect your
computers to share some data or even play a game. If all three of your
computers have wireless capabilities, you can create an ad hoc network.
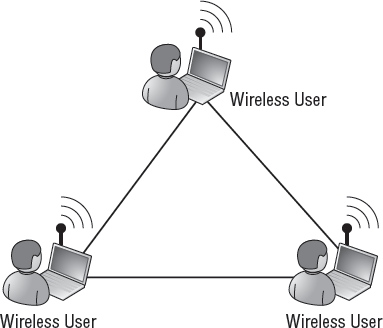
Figure 4
shows three wireless users configured in an ad hoc wireless network.
One of the computers creates the ad hoc network, and the other two
computers connect to it.
An ad hoc network is created for a
specific purpose but is usually destroyed when users disconnect.
However, it is possible to save the network profile for later use.
Figure 5
shows the screen used to create the ad hoc network. You need to give
the network a name. In the figure, I've called it TempAdHoc. You also
need to identify the security type and the security key that will be
used. The security key is a pre-shared key such as a password or
passphrase. All participants in the ad hoc network need to use the same
security type and PSK.

You can get to the screen shown in Figure 5 by clicking Control Panel => Network And Internet =>
Network And Sharing Center. You can also get to the Network and Sharing
Center by entering Network in the Control Panel Search box and
selecting Network And Sharing Center. From there, click Manage Wireless
Networks. Click Add and select Create An Ad Hoc Network.
|
The Manage Wireless
Networks screen will appear only on clients that have wireless NICs. If
your system doesn't have a wireless NIC installed, you will not see this
choice.
|
|
Ad hoc networks support three security types:
- No Authentication (Open)
Data is sent in the
clear. Generally, this is not recommended. However, gamers may choose
this for better performance over a wireless network.
- WEP
If older computers support
only WEP, you can use this. It has known vulnerabilities but is better
than nothing to secure the connection.
- WPA2-Personal
WPA2-Personal provides the best security. An ad hoc network does not support WPA2-Enterprise.
NOTE
WPA-Personal is not available
as a choice for ad hoc networks. WPA Enterprise and WPA2 Enterprise
aren't available as choices either, because you are connected only
between peers. Enterprise choices require a separate 802.1x server to be
used for authentication.
The security key is a shared
secret. Each user will need to enter the same security key in their
wireless profile to connect to the ad hoc network.
Last, if you want to save the ad hoc network for later use, you can check the Save This Network box, as shown in Figure 5 earlier. It will save this as an ad hoc profile that can be used later.
Only the first computer
needs to create the ad hoc network. Once it's created, other computers
can connect to it as if it was a wireless network connection.