Windows Firewall has been standard since Windows XP. In Windows XP SP2, it was enabled by default, and it has steadily improved over the years.
A firewall is designed to
protect a computer or network by controlling inbound and outbound
traffic. Most firewalls operate with an implicit deny philosophy. In
other words, all traffic is blocked (implicit deny) unless there is a
rule that explicitly allows the traffic.
Windows Firewall on Windows 7 also uses an implicit deny philosophy. The only traffic that is allowed is the following:
Traffic that is explicitly allowed by an exception or a rule. Both inbound and outbound rules can be configured.
Return
traffic that has been requested. For example, if a user requests a web
page from a website, the web page is allowed as return traffic.
Windows Firewall works as both a packet-filtering firewall and a stateful firewall.
Packet-filtering firewall
A packet-filtering
firewall can filter traffic based on IP addresses, ports, and some
protocols. The firewall examines packets individually. Packets can be
allowed or blocked based only on what is in each packet. A
packet-filtering firewall can't evaluate packets based on the entire
communication.
Stateful firewall
A stateful firewall can
monitor the state of a connection. In other words, instead of examining
each packet individually, it evaluates the packets in the conversation.
This allows a stateful firewall to detect and block many attacks.
As a stateful firewall, it can inspect and filter all IPv4 and IPv6 traffic.
1. Checking the Firewall Status
If you suspect problems with the
firewall, one of the first things you should check is the status. You
can check it via the Control Panel. Type in Firewall in the Search Control Panel box, and click Check Firewall Status. Figure 1 shows the firewall status screen.
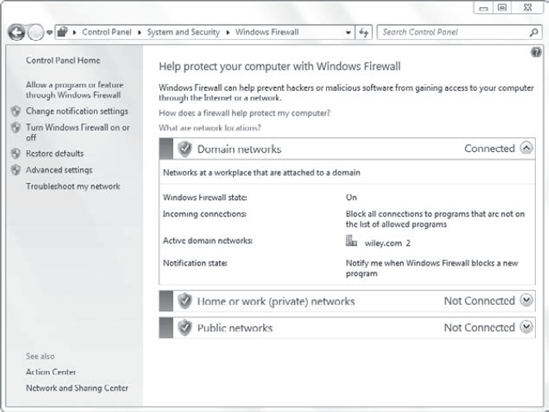
Notice that it shows the
firewall is controlled using the Domain Networks settings. The firewall
has detected that the system is connected to the domain. This figure
also shows both the Home Or Work (Private) Networks and Public Networks
as Not Connected. If the system was connected to a public network, the
Public Networks would appear as Connected, and the firewall would be
controlled with the Public Networks settings.
This display shows that
the firewall is on and configured to block all connections that aren't
on the list of allowed programs. It is also configured to provide a
notification when Windows Firewall blocks a program.
1.1. Determining Whether a Port or a Protocol Needs to Be Enabled
Some applications require
that certain ports be opened or traffic using certain protocols be
allowed. If the traffic is blocked, the application won't work. When
configuring newly installed applications that aren't working, you should
consider the possibility that an exception needs to be created in the
firewall.
The top link on the left of the
Windows Firewall status screen is labeled Allow A Program Or Feature
Through Windows Firewall. You can see this link on Figure 11.16.
If you click this link, you'll see the display shown in Figure 2. This can be used to create an exception for different applications. When an exception is enabled, traffic will be allowed.
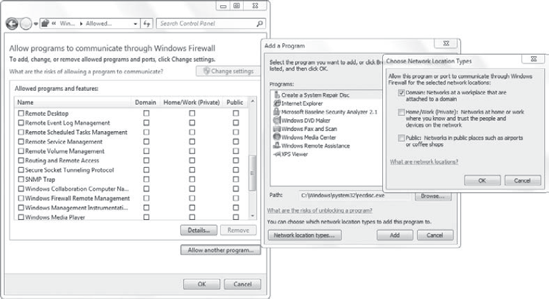
To create an exception, you
can check the box for any of the features listed. You can create an
exception for an application by clicking the Allow Another Program
button. Most installed programs will automatically appear in this list,
but you can also click Browse to locate the application.
2. Designing Firewall Rules
You can create firewall
rules from the Windows Firewall Advanced Settings screen. You can modify
preexisting rules or create your own rules.
New rules can be created to allow traffic based on the following:
Custom rules allow you to specify traffic for specific protocols, protocol numbers, and ports.
Figure 3
shows a partial list of the predefined rules. Settings that are enabled
are shown with a check mark in a green circle. Any of these settings
can be enabled or disabled by right-clicking and selecting Enable Rule
or Disable Rule.
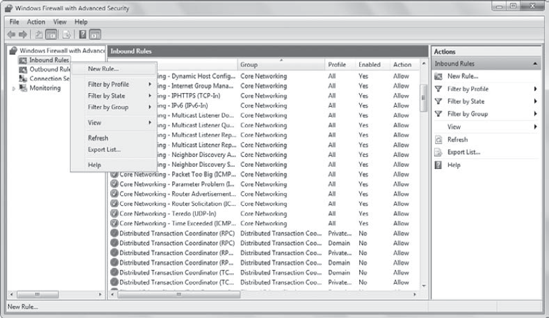
Most of the properties in the
predefined rules can't be modified. However, you can re-create any rule
to meet specific requirements.
You can also create rules in Group Policy. The Computer Configuration => Policies => Windows Settings => Security Settings =>
Windows Firewall with Advanced Security node can be used to create new
inbound rules, outbound rules, or connection security rules. Although
none of the predefined rules are shown by default, they can be selected
when creating a new rule.
Launch the Windows Firewall Advanced Settings screen. Click Start => Control Panel. Type Firewall and select Windows Firewall. Click Advanced Settings. Select Inbound Rules. Right-click Inbound Rules and select New Rule. On the Select Rule Type page, you can select Program, Port, Predefined, or Custom. Select Port and click Next. Select either TCP or UDP based on the traffic you want to allow. Enter the port numbers you want to allow. Click Next. On
the Action page, notice that you can select one of three settings:
Allow The Connection, Allow The Connection If It Is Secure, or Block The
Connection. Select Allow The Connection and click Next. The
Profile page appears. You can have this rule apply to the Domain,
Private, and/or the Public network profiles. They are all checked by
default. Click Next. Name your rule and enter a description if desired. Click Finish, and it is created.
|