3. Layer 3: Hardening the system
Layer 3 is where you can begin to rely on
Vista's features to protect your systems. On this layer, you have access
to several different methods for system protection. Vista does a great
job of limiting attack surfaces, but you still need to apply additional
protection configurations. At this layer, you need to work with the
following Vista features:
Local Security Policy and Security Configurations
BitLocker Full Drive Encryption
User Account Control
USB Device Control
Windows Defender
Automatic Update Management
Wireless and Wired Network Configurations
Each of these items is part of the configuration
of this layer. Of course, you also need to keep in mind your staging
practices for the PC itself.
3.1 Local Security Policy and security configurations
One very good example of a system type where you would
use multiple LSPs is the kiosk PC. This PC needs to be locked down when
normal users work with it. Therefore, you apply the three LSPs in the
following manner:
Apply
the LSP at the computer level to completely lock down the system. This
LSP will apply to the public when they work with the kiosk PC.
Apply
the second LSP to users who are nonadministrators, but have an account
in your network. These users may have a less restricted environment.
Apply the final LSP to administrators, letting them modify settings and update the configuration of the PC.
In addition, you should apply GPOs to the system
by using the Loopback feature to ensure that no matter who logs on, the
system's settings will always reset to a locked-down environment after
it is put back to public usage.
You can of course export and import individual
settings from an LSP to another. But when you create a comprehensive
configuration for a system and you want to apply this configuration to
every system of this type as soon as it is built, you must go beyond the
LSP. For this reason, Vista includes the ability to create Security
Templates and apply these templates to any system through the Security
Configuration and Analysis tool. Both tools are snap-ins that are
assigned to custom Microsoft Management Consoles. To work with these
tools, you must create your own console because one does not exist by
default.
To create your custom console, follow these steps:
Choose Start Menu =>
Search to type mmc and press Enter.
Accept the UAC prompt. Doing this opens a blank MMC console.
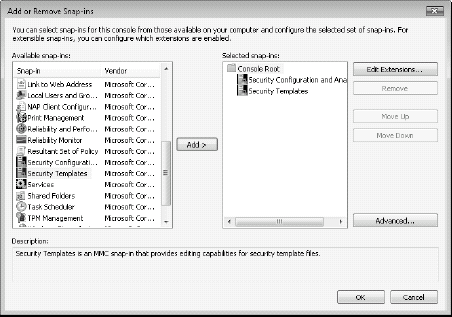
Choose File =>
Add/Remove Snap-in, scroll down the
list to the left, select Security Configuration and Analysis (SCA), and
click Add. Repeat for the Security Templates snap-in. The two snap-ins should be listed in the selected snap-ins column as shown in Figure 1.
Click OK. You should now have a new console with two items contained within it. Save the console.
Choose File =>
Save and save it under your Documents folder (this will make it easier to find later on). Name it Security Console.
Now you're ready to begin working with your security console. Security templates can include several settings from the LSP:
Account Policies
Local Policies
Event Log
Restricted Groups
System Services
Registry
File System
Each of these lets you configure how the
elements it controls will be configured on the local system. Also,
remember that when you apply an LSP, it will be overridden by the
settings found in Group Policy because of the GPO application order.
Therefore, you can use security templates in two different situations:
You can use templates to apply settings
to standalone computers — computers that will not be part of a domain
and will not receive GPO settings that may override the local settings.
You
can use templates to apply settings that would not normally be applied
by a GPO. This way, there are no conflicting settings, and the settings
you apply locally will always remain the same.
The most common application of security
templates, especially in a Vista environment, is the second one. And, as
funny as it sounds, most often, administrators do not use the template
to apply additional security, but rather to loosen security settings.
That's because Vista has a very tight configuration by default. Windows
Resource Protection (WRP), the system that protects core system files
and registry keys, does a great job of locking down the system. But this
great job often has a negative impact on legacy applications, applications that have not been designed for Vista and must write in some protected areas of the system.
Therefore, what you need to do is identify which
files and registry keys an application needs access to and change its
security settings. The best way to do this is to use two utilities
FileMon and RegMon. FileMon scans the file system and captures any files
that are accessed by the application during operation. RegMon does the
same for registry keys. Basically, you run both tools, run the
application, and perform as many operations with the application as
possible. You capture the affected files and registry keys by outputting
them from the two utilities. Once armed with the files and registry
keys to change, you use your security console to generate a template
that will modify the files and registry keys appropriately for the
application to run with standard user rights. The resulting template you
create can then be delivered and applied each time you install the
application on a system, guaranteeing that the application will run on a
locked-down Vista system.
You can also rely on templates provided by other
organizations to tighten security on your systems. For example, the
Vista Security Guide includes templates and GPOs for additional
security. But Microsoft is not the only source of templates. The
National Security Agency (NSA) and the Center for Internet Security
(CIS) also offer templates that help you secure systems. You can
download and use these templates to secure your own systems. Finally,
you can also obtain security templates from third-party vendors.
What's really nice is that the Security
Configuration and Analysis snap-in lets you run these templates in
analysis mode so that you can simply view what settings would be
changed, letting you understand the content of the templates before
adding them.
Whether you want to tighten or loosen security settings, the operations will be the same. Do the following:
Return to your security console. Expand the Security Templates section until you see the search path. Templates are automatically loaded into this console when they are found. By default this search path is %UserProfile%\Documents\Security\Templates.
If you obtain new templates from an external source, place them in this
folder to automatically view their contents. You can change this folder
location by selecting New Template Search Path from the context menu of
the Security Templates item.
If
you don't have a third-party template, select New Template by
right-clicking on the Search Path. Name the template and give it a
description and click OK.
To
ensure that your settings will not be modified by Group Policy,
restrict your own changes to the Registry and the File System items. To
modify either, first expand the template, then right-click on the item
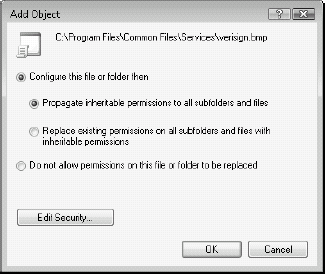
and select Add Key for registry settings or Add File for files. After the file or setting is selected, a security dialog box appears.
Apply appropriate settings and click OK.
As shown in
Figure 2, you
now need to decide if you want to Propagate inheritable permissions,
Replace permissions or Block permission replacement on this object.
Click OK when done.
Repeat for each of the files or registry settings you want to change.
Save the changes to the template by right-clicking the template name and selecting Save.
There it is. Your first template is created. Now
you use the Security Configuration and Analysis tool or its command
line equivalent to apply it or you can apply it to a GPO and assign it
appropriately.
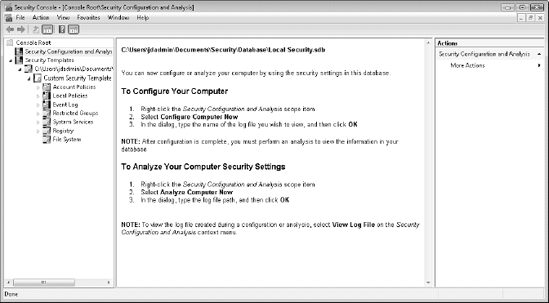
Use
the Security Configuration Analyzer (SCA) to analyze your computer and
compare its settings to those in the template. Click on the SCA to
change the focus of the console and then right-click SCA and select Open
database.
Find a database if one exists or type in a new database name; then click OK. Like the templates, the databases are stored in %UserProfile%\Documents\Security\Databases.
Now select the template you want to test and click OK. The Details pane now displays the next steps, as shown in Figure 3.
To analyze your computer, right-click SCA and choose Analyze Computer Now. Doing this opens a dialog box requesting the location of the log file for the analysis.
Type in the name and click OK.
The
analysis is performed. To view differences between the template and the
system, move to the setting you wish to view in the Tree pane. Differences will be displayed in the Details pane. Items that are changed include a small question mark on their icon.
If
you want to update the database setting by using a setting originating
from the computer, double-click it and select Define this policy in the
database; modify the setting and click OK.
Choose Save from the SCA context menu to save your changes.
Select Configure Computer Now from the SCA context menu. Identify the log file and click OK. Doing this applies the changes and saves the database when done.
If
you want to create a template from a preconfigured computer, then
repeat the steps to generate the database, name a new template, analyze
the computer, and then select Export Template from the SCA context menu.
Preconfiguring a system and then capturing the
template from it may be easier than generating a template manually and
doing the reverse. You can also analyze and configure computers from the
command line. Use the following command to configure computers
automatically:
secedit /configure /db filename.sdb /log filename.log
Make sure that you create these templates and then use the secedit command to apply them at computer setup. You can use the Runonce command to automatically apply your security templates after the system reboots the first time once Vista is installed.