Protecting Yourself Against Email Viruses
Until just a few
years ago, the primary method that computer viruses used to propagate
themselves was the floppy disk. A user with an infected machine would
copy some files to a floppy, and the virus would surreptitiously add
itself to the disk. When the recipient inserted the disk, the virus copy
would come to life and infect yet another computer.
When the Internet became a
big deal, viruses adapted and began propagating either via malicious
websites or via infected program files downloaded to users’ machines.
Over the past couple of
years, however, by far the most productive method for viruses to
replicate has been the humble email message. Melissa; I Love You;
BadTrans; Sircam; Klez. The list of email viruses and Trojan horses is a
long one but they all operate more or less the same way: They arrive as
a message attachment, usually from someone you know. When you open the
attachment, the virus infects your computer and then, without your
knowledge, uses your email client and your address book to ship out
messages with more copies of itself attached. The nastier versions will
also mess with your computer by deleting data or corrupting files.
You can avoid getting infected by one of these viruses by implementing a few common sense procedures:
- Never open an attachment that comes from someone you don’t know.
- Even
if you know the sender, if the attachment isn’t something you’re
expecting, assume that the sender’s system is infected. Write back and
confirm that the sender emailed the message.
- Some
viruses come packaged as scripts that are hidden within messages that
use the Rich Text (HTML) format. This means that the virus can run just
by viewing the message! If a message looks suspicious, don’t open it,
just delete it. (Note that you’ll need to turn off the Outlook Express
preview pane before deleting the message. Otherwise, when you highlight
the message, it will appear in the preview pane and set off the virus.
Select View, Layout, deactivate the Show Preview Pane check box, and
click OK.)
- Install a top-of-the-line antivirus program,
particularly one that checks incoming email. Also, be sure to keep your
antivirus program’s virus list up to date. As you read this, there are
probably dozens, maybe even hundreds, of morally challenged scumnerds
designing even nastier viruses. Regular updates will help you keep up.
In addition to these
general procedures, Outlook Express also comes with its own set of virus
protection features. Here’s how to use them:
1. | In Outlook Express, select Tools, Options.
| 2. | Display the Security tab.
| 3. | In the Virus Protection group, you have the following options:
| Select the Internet Explorer Security Zone to Use |
From the perspective of Outlook Express, you use the security zones to
determine whether active content inside an HTML-format message is
allowed to run:Internet Zone—If you choose this zone, active content is allowed to run. Restricted
Sites Zone—If you choose this option, active content is disabled. This
is the default setting and it’s the one I recommend.
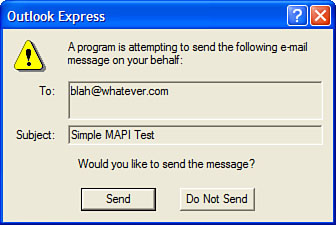
| | Warn Me When Other Applications Try to Send Mail as Me | As
I mentioned earlier, it’s possible for programs and scripts to send
email messages without your knowledge. This is done using Simple MAPI
(Messaging Application Programming Interface) calls, which can be used
to send messages via your computer’s default mail client, and it’s all
hidden from you. When this check box is activated, Outlook Express
displays a warning dialog box (see Figure 1)
when a program or script attempts to send a message using Simple MAPI.
Click Send to allow the message; click Do Not Send to cancel the
message. |
|
Activating the Warn Me
When Other Applications Try to Send Mail as Me option protects you
against scripts that attempt to send surreptitious messages using Simple
MAPI calls. However, there’s another way to send messages behind the
scenes. It’s called Collaboration Data Objects (CDO), and it’s installed by default in Windows XP. Here’s a sample script that uses CDO to send a message:
Dim objMessage
Set objMessage = CreateObject("CDO.Message")
With objMessage
.To = "[email protected]"
.From = "[email protected]"
.Subject = "CDO Test"
.TextBody = "Just testing..."
.Send
End With
Set objMessage = Nothing
The Warn Me When Other Applications Try to Send Mail as Me option does not
trap this kind of script, so bear in mind that your system is still
vulnerable to Trojan horses that send mail via your Windows XP accounts.
|
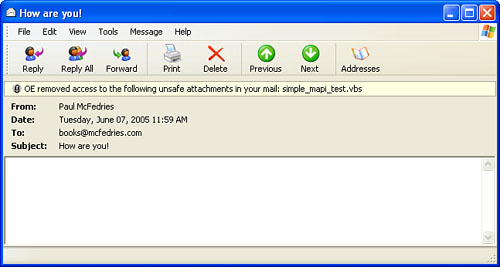
| Do Not Allow Attachments to Be Saved or Opened That Could Potentially Be a Virus | When
this check box is activated, Outlook Express monitors attachments to
look for file types that could contain viruses or destructive code. If
it detects such a file, it disables your ability to open or save that
file, and it displays a note at the top of the message to let you know
about the unsafe attachment, as shown in Figure 2. |
|
The file types that
Outlook Express disables are defined by Internet Explorer’s built-in
unsafe-file list. This list includes file types associated with the
following extensions: .ad, .ade, .adp, .bas, .bat, .chm, .cmd, .com, .cpl, .crt, .exe, .hlp, .hta, .inf, .ins, .isp, .js, .jse, .lnk, .mdb, .mde, .msc, .msi, .msp, .mst, .pcd, .pif, .reg, .scr, .sct, .shb, .shs, .url, .vb, .vbe, .vbs, .vsd, .vss, .vst, .vsw, .wsc, .wsf, .wsh.
|
Tip
What do you do if you
want to send a file that’s on the Outlook Express unsafe file list and
you want to make sure that the recipient will be able to open it? The
easiest workaround is to compress the file into a .zip file, which won’t be blocked by Outlook Express (or Outlook or any other mail client that blocks file types).
| 4. | Click OK to put the new settings into effect. |
Filtering Out Spam
Spam—unsolicited
commercial messages—has become a plague upon the earth. Unless you’ve
done a masterful job at keeping your address secret, you probably
receive at least a few spam emails every day, and it’s more likely that
you receive a few dozen. The bad news is most experts agree that it’s
only going to get worse. And why not? Spam is one of the few advertising
mediums where the costs are substantially borne by the users, not the
advertisers.
The best way to avoid
spam is to not get on a spammer’s list of addresses in the first place.
That’s hard to do these days, but there are some steps you can take:
- Never use
your actual email address in a newsgroup account. The most common method
that spammers use to gather addresses is to harvest them from newsgroup
posts. One common tactic is to alter (or munge,
in the vernacular) your email address by adding text that invalidates
the address but is still obvious for other people to figure out:
[email protected]_this_to_email_me.com
- When
you sign up for something online, use a fake address if possible. If
you need or want to receive email from the company and so must use your
real address, make sure that you deselect any options that ask if you
want to receive promotional offers. Alternatively, enter the address
from a free Web-based account (such as a Hotmail account), so that any
spam you receive will go there instead of to your main address.
- Never
open suspected spam messages because doing so can sometimes notify the
spammer that you’ve opened the message, thus confirming that your
address is legit. For the same reason, you should never display a spam
message in the Outlook Express preview pane. As described earlier, shut
off the preview pane before highlighting any spam messages that you want
to delete.
- Never, I repeat, never,
respond to spam, even to an address within the spam that claims to be a
removal address. By responding to the spam all you’re doing is proving
that your address is legitimate, so you’ll just end up getting more spam.
Tip
If you create web pages, never put your email address on a page because spammers use crawlers that harvest addresses from web pages. If you must put an address on a page, hide it using some simple JavaScript code:
<script language="JavaScript" type="text/javascript">
<!--
var add1 = "webmaster"
var add2 = "@"
var add3 = "whatever.com"
document.write(add1 + add2 + add3)
//-->
</script>
There are a host of
commercial spam-killers on the market, but with a bit of work you should
be able to eliminate most spam by using nothing more than the built-in
tools available in Outlook Express. I’m talking specifically about using
mail rules:
conditions that look for messages with specific characteristics—for
example, certain words in the subject or body—and actions that do
something with the matching messages—such as delete them.
To filter spam, your rules need to look for incoming messages that meet one or more of the following criteria:
Specific words in the Subject line—
The sneakier spammers hide their messages behind innocuous subject
lines such as “Here’s the information you requested.” But most spam
comes with fairly obvious Subject lines: “Make $$$Money Now!!!” or “FREE
Business Cards.” Instead of creating a rule based on an entire Subject
line, you only need to watch for certain keywords. Here are a few that I
use (I’ve removed some of the more explicit terms that filter out
pornographic spam):
!!!!!!!, $, %,
.name, 18+, about your site, adult, adv, advertise, ameritrade, annual
reports, are you in debt, back taxes, bargain, be 18, britney, bulk, buy
recommendation, cartridges, cash, casino, clients, collect your money,
credit card, credit rating, creditor, debts, descrambler, dieting,
diploma, don’t miss, double your money, dvd movies, earning!, e-mail
marketing, emarketer, erotic, excite game, f r e e, find out anything,
flash alert, free cell, free credit, free pda, free phone, free trial,
free vacation, free!, freee, get out of debt, giveaway, got debt,
guaranteed!, hair loss, hormone, how to make money, increase your sales,
incredible opportunity, interest rates, investment goals, iPod, is this
a picture of you, klez, lemme, life insurance, loans, lose up to, lose
weight, lose while you sleep, losing sleep, low on funds, marketing
services, maximize your income, merchant, millionaire, mlm, mortgage,
new car, new photos from my party, online market, online pharmacy, over
18, over 21, printer cartridge, promote your business, reach millions,
reduce your debt, refinance, refinancing, s e x, satellite, saw your
site, secure your future, seen on tv, sex, singles, snoring, spec sheet,
steroids, stock, stock alert, systemworks, thinning hair, this one’s on
us, too good to be true, trading alert, trading report, uncover
the truth, urgent notice, viagra, web traffic, what are your kids, work
at home, work from home, xxx, years younger, you are a winner, you have
to see this
Specific words in the message body—
The message body is where the spammer makes his or her pitch, so
there’s rarely any subterfuge here. You can filter on the same terms as
you used for the subject line, but there are also a few telltale terms
that appear only in spam messages. Here are some that I use:
///////////////, 100%
satisfied, adult en, adult web, adults only, cards accepted, check or
money order, dear friend, extra income, for free!, for free?,
satisfaction guaranteed, money back, money-back guarantee, one-time
mail, order now!, order today, removal instructions, special promotion
Specific names in the From line— Many spammers spoof
their From address by using a random address or, more likely, an
address plucked from their distribution list. However, some use
addresses that have a common theme, such as “sales@” (for example,
[email protected]). Here are some common From line names to filter:
@mlm, @public, @savvy, ebargains, free, hello@, link2buy, mail@, profits@, sales@, success, success@
Specific names in the To line—
The To line of spam messages usually contains either an address from
the distribution list or “Undisclosed Recipients.” You can’t filter on
the latter, however, because many legitimate mailings also use that
“address.” However, there are a few common To line names to watch for:
anyone@, creditcard@, free@, friend, friend@, nobody@, opportunity@, public@, success@, winners@
|