IT departments often address information security
through a set of tactical initiatives, such as carrying out a network
vulnerability scan or deploying antivirus programs. Although these are
important tools for securing your IT environment, their effectiveness
can be limited unless they are part of an overall security program.
A security program is an
ongoing organizational effort to align security policies and practices
with your business goals and regulatory requirements. An effective
security program requires involvement and support from upper-management.
In a corporate environment, ultimate responsibility for information
security and regulatory compliance rests with the executive management
and board of directors. The security program defines an enterprise
security architecture including policies, standards, and practices for
addressing security within your organization. The enterprise security
architecture should form the basis of your strategic, tactical, and
operational initiatives to address information security. Organizations
today are at various stages of maturity in terms of implementing a
security program. Many are just starting or have not started at all,
whereas other organizations have made extensive efforts and have robust
security programs.
|
Similar to other aspects of
IT, security programs tend to go through the steps portrayed in
Microsoft’s Infrastructure Optimization Model (IO Model), used to assess the maturity of organizations’ IT operations.
The
Infrastructure Optimization Model categorizes the state of one’s IT
infrastructure, describing the impacts on cost, security risks, and the
ability to respond to changes. Using the model in Figure 1, you can identify where your organization is, and where you want to be.
Basic— Reactionary, with much time spent fighting fires Standardized— Gaining control Rationalized— Enabling the business Dynamic— Being a strategic asset
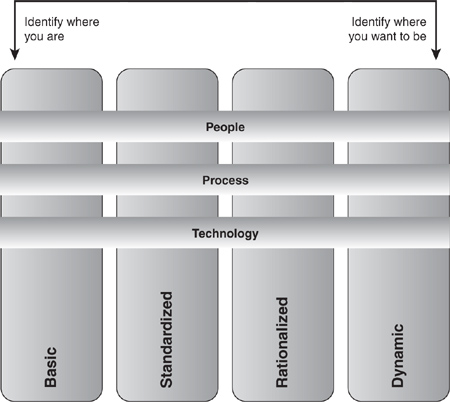
Although most
organizations are somewhere between the basic and standardized levels in
this model, typically you should prefer to have a strategic asset
rather than fighting fires. This is as true in managing security as in
managing desktops.
|
As an IT professional,
you should become familiar with your organization’s security program and
engage the appropriate resources to support your efforts to implement
security effectively within the scope of your responsibility. To
implement ConfigMgr security in
a way that is appropriate and beneficial to your organization, you need
to understand ConfigMgr security issues and apply them according to the
policies and methodology of your enterprise security program.
The principal
objectives of information security are to protect the Confidentiality,
Integrity, and Availability (known as the CIA or AIC triad) of
information assets. A fourth objective included by many security experts
is alternately called accountability or auditability. These objectives
can be described as follows:
Confidentiality—
Protecting company secrets, private employee information and
information belonging to customers, partners and suppliers is essential
to avoid potential legal sanctions and financial losses. Confidentiality
is even more important in military organizations. Configuration Manager
2007 provides access to data stored on client machines through its
inventory and remote management capabilities. The site database also
contains configuration data that an attacker can use to find
vulnerabilities in your network and systems. Protecting your ConfigMgr
infrastructure is, therefore, vital to ensuring confidentiality for
sensitive data. Integrity—
In addition to protecting data from unauthorized disclosure, effective
security must protect information and systems from unauthorized
modification. A poorly designed software package or malicious use of
ConfigMgr tools can easily compromise the integrity of your environment.
Protecting the integrity of information systems is, therefore, a
paramount concern in ConfigMgr security. Availability—
In many cases, an interruption of vital services might cause business
losses equal to or greater than a lapse in confidentiality or integrity.
For example, a customer-facing
website might not store or process sensitive information, but if it is
down, the company’s Internet presence is lost until the service is
restored. Even in military settings where confidentiality and integrity
are generally the foremost concerns, disruption of vital command,
communications, or intelligence systems during combat operations can
have catastrophic consequences. Your ConfigMgr infrastructure needs to
be resilient enough to provide services reliably while at the same time
avoiding any negative effects on other network or system functionality.
Although ConfigMgr service availability often is not considered mission
critical, if your patch management infrastructure is down when you need
to deploy a critical patch, your entire environment could be at risk. If
you enforce Network Access Protection (NAP), clients might need to
access ConfigMgr services for remediation to gain access to your
network. Accountability—
To demonstrate you follow security policies and allow you to take
corrective action if a breach of security occurs, you must maintain
effective audit logs to track security sensitive operations on a per
user basis. With increasing emphasis on regulatory compliance, the
completeness and integrity of audit logs and records of user activity is
an integral part of any security program. ConfigMgr provides the
ability to track user actions, and additional audit capabilities are
available within Windows, SQL Server, and in many cases through your
network infrastructure devices.
A guiding principle in security is the concept of risk management. It is not possible for any organization to keep its assets absolutely secure. Some basic risk management concepts include
A vulnerability
is a weakness that could result in compromise of the confidentiality,
integrity, or availability of your information or systems. A threat
is a potential danger to your information systems. Keep in mind that
threats include both malicious and inadvertent actions. Good security
helps protect against honest mistakes by users and deliberate breaches
by hackers and malware creators. A risk is the likelihood of a threat being realized and the associated business impact if the threat is realized.
There are four
possible approaches for dealing with risk, and your organizational
policies determine how you choose or recommend a strategy for each set
of potential risks:
Risk avoidance—
You might decide that the business value of undertaking a technology
initiative simply does not justify the risk. For example, you might
decide that the value to your company of Internet-based client
management (IBCM) is not sufficient to justify exposing your ConfigMgr
infrastructure to the Internet. Risk mitigation—
You might decide to implement countermeasures to address potential
threats to reduce risk. For example, you might decide to implement a
Public Key Infrastructure (PKI) and deploy Configuration Manager 2007 in
native mode to reduce the chances of a network-based attack on
ConfigMgr communications. Risk acceptance—
You might decide to accept certain risks if both the business value of
the activity and the cost of implementing additional controls to
mitigate risk outweigh the potential losses posed by the risk. For
example, you might decide to
accept the risk of using a system as a branch distribution point (BDP)
that does not meet the normal security standards of your server
infrastructure. You would choose to accept this risk if you determine
the value of the services the BDP provides is sufficient to justify the
risk, and the cost of implementing a higher level of security is not
justified by the risk mitigation it would provide. Risk transfer—
In some cases you can purchase insurance to protect your organization
from losses due to certain risks. Risk transfer is mentioned here for
completeness, but this strategy is generally not applicable to the
security choices you make in your ConfigMgr deployment.
Every organization must
assess the value of its assets and weigh the probable losses from
threats to those assets against the costs of implementing additional
security measures to counter those threats. Risk mitigation strategies, also known as controls, fall into three categories:
Technical—
Technical controls are often the first things that come to mind when
thinking of information security. Firewalls, antimalware programs,
access controls, and cryptography are examples of tools you can use to
implement technical controls. Microsoft provides extensive guidance on
technical controls relevant to ConfigMgr under the Security and Privacy
for Configuration Manager 2007 topic at the System Center TechCenter (http://technet.microsoft.com/en-us/library/bb680768.aspx).
Administrative—
Administrative controls are every bit as essential to information
security as technical controls. These controls include policies,
standards, and procedures that integrate sound security practices into
the way your organization does business and how you provide IT services. Physical—
Physical controls prevent unauthorized physical access to your IT
assets. These controls include building access systems, cameras, guards,
and alarm systems. Physical security is an integral part of information
security, and there is a growing trend to unify information security
and physical security, although most IT professionals are not directly
responsible for physical security services.
|