Understanding Stub
Zones
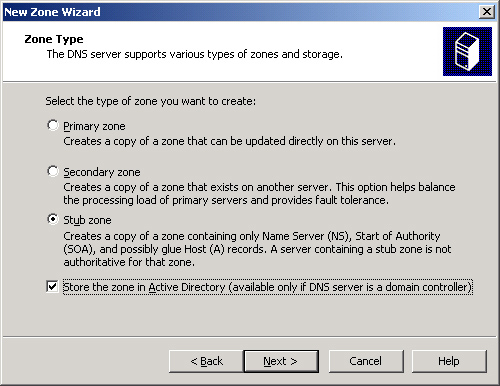
When you configure a new
zone using the New Zone Wizard, you have the option of creating the new
zone as a primary, secondary, or stub zone, as shown in Figure 1. When you create a stub zone, a zone is
configured that maintains only those records—NS resource records—needed
to locate the name servers of the master zone specified by the name of
the stub zone.
Stub zones are used to
keep all the NS resource records from a master zone current. To
configure a stub zone, you need to specify at least one name server, the
master, whose IP address doesn’t change. Any new name servers that you
add to the master zone later are updated to the stub zone automatically
through zone transfers.
You cannot modify a stub
zone’s resource records. Any changes you want to make to these records
in a stub zone must be made in the original primary zone from which the
stub zone is derived.
To add a stub zone,
complete the following steps:
1. | Open the DNS console.
|
2. | In the
console tree, right-click a DNS server, and then select New Zone to open
the New Zone Wizard.
|
3. | Follow the
instructions to create a new stub zone.
|
Benefits of Stub
Zones
Stub zones
allow you to achieve the following benefits:
Improve name resolution Stub zones enable a DNS server to perform recursion
by using the stub zone’s list of name servers without querying the root
server.
Keep foreign
zone information current By updating
the stub zone regularly, the DNS server hosting the stub zone maintains
a current list of name servers for a different zone, such as a
delegated zone on a different DNS server.
Simplify DNS
administration By using stub zones
throughout your DNS infrastructure, you can distribute zone information
without using secondary zones.
Important
Stub zones do
not serve the same purpose as secondary zones and are not an
alternative when planning for fault tolerance, redundancy, or load
sharing. |
When to Use Stub
Zones
Stub zones are most
frequently used to keep track of the name servers authoritative for
delegated zones. Most often, stub zones are hosted on the parent DNS
servers of those delegated zones.
A DNS server that has
delegated a child zone to a different DNS server is usually informed of
new authoritative DNS servers added to the child zone only when the
resource records for these new DNS servers are added to the parent zone
manually. With stub zones, a DNS server can host a stub zone for one of
its delegated (child) zones and obtain updates of that zone’s
authoritative servers whenever additional name servers are added to the
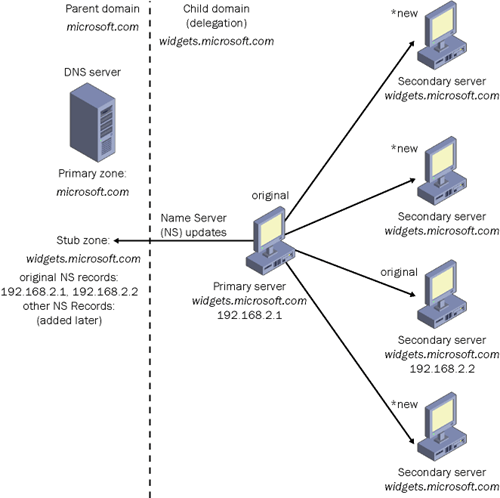
master zone. This functionality is explained in the following example,
illustrated in Figure 2.
Tip
Expect to be
tested on stub zones on the 70-291 exam. First and foremost, you need to
be able to recognize scenarios in which deploying a stub zone is
appropriate. |
Stub Zone Example
A DNS server
authoritative for the parent zone microsoft.com delegated a child zone,
widgets.microsoft.com, to separate DNS servers. When the delegation for
the child zone widgets.microsoft.com was originally performed, it
contained only two NS resource records for the widgets.microsoft.com
zone’s authoritative DNS servers. Later, administrators of this zone
configured additional DNS servers as authoritative for the zone but did
not notify the administrators of the parent zone, microsoft.com. As a
result, the DNS server hosting the parent zone is not informed of the
new DNS servers authoritative for its child zone, widgets.microsoft.com,
and continues to query the only two authoritative DNS servers that
exist in the stub zone.
You can remedy this
situation by configuring the DNS server authoritative for the parent
zone, microsoft.com, to host a stub zone for its child zone,
widgets.microsoft.com. When the administrator of the authoritative DNS
server for microsoft.com updates the resource records for its stub zone,
it queries the master server for widgets.microsoft.com to obtain that
zone’s authoritative DNS server records. Consequently, the DNS server
authoritative for the parent zone learns about the new name servers
authoritative for the widgets.microsoft.com child zone and is able to
perform recursion to all of the child zone’s authoritative DNS servers.
Other Uses for
Stub Zones
You can also use stub
zones to facilitate name resolution across domains in a manner that
avoids searching the DNS namespace for a common parent server. Stub
zones can thus replace secondary zones in cases where achieving DNS
connectivity across domains is important but providing data redundancy
for the master zone is not. Also note that stub zones improve name
resolution and eliminate the burden to network resources that would
otherwise result from large zone transfers.
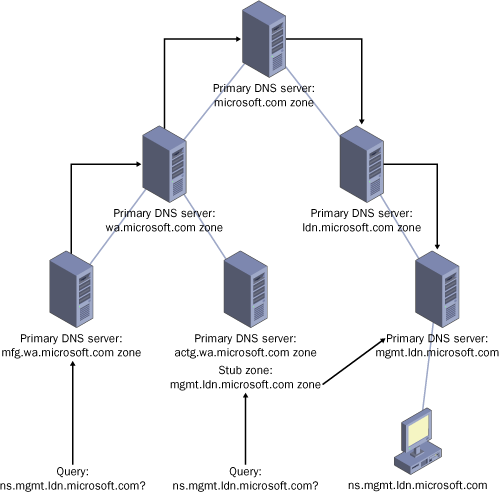
Figure 3
illustrates using stub zones to facilitate name resolution in this way.
In the example, a query for the host name ns.mgmt.ldn.microsoft.com is
submitted to two different name servers. In the first case, the server
authoritative for the mfg.wa.microsoft.com domain accepts the query.
Many other name servers must then be contacted before the destination
name server authoritative for the appropriate domain
(mgmt.ldn.microsoft.com) receives the query. In the second case, the DNS
server authoritative for the actg.wa.microsoft.com domain receives a
query for the same name, ns.mgmt.ldn.microsoft.com. Because this second
server also hosts a stub zone for the destination
mgmt.ldn.microsoft.com, the server already knows the address of the
server authoritative for ns.mgmt.ldn.microsoft.com, and it sends a
recursive query directly to the authoritative server.
Stub Zone
Resource Records
A stub zone contains SOA,
NS, and A glue resource records for authoritative DNS servers in a zone.
The SOA type identifies the primary DNS server for the actual zone
(master server) and other zone property information. The NS resource
record type contains a list of authoritative DNS servers for a zone
(primary and secondary servers). The A glue resource records hold the IP
addresses of the DNS servers authoritative for the zone.
Note
As with
delegations, stub zones contain glue records in the zone data, but these
glue records are not visible in the DNS console. |
Stub Zone
Resolution
When a DNS client
performs a recursive query operation on a DNS server hosting a stub
zone, the DNS server uses the stub zone’s resource records to resolve
the query.
The DNS server then queries the authoritative
servers specified in the stub zone’s NS resource records. If the DNS
server cannot find any of the authoritative name servers listed in its
stub zone, it attempts standard recursion.
The DNS server
stores the resource records it receives from a stub zone’s authoritative
servers in its cache and not in the stub zone itself; only the SOA, NS,
and A resource records returned in response to the query are stored in
the stub zone. The resource records stored in the cache are cached
according to the Time to Live (TTL) value in each resource record. The
SOA, NS, and A resource records, which are not written to the cache,
expire according to the interval specified in the stub zone’s SOA
resource record, which is created during the creation of the stub zone
and updated during transfers to the stub zone from the original primary
zone.
When a DNS server
receives a query for which recursion has been disabled, the DNS server
returns a referral pointing to the servers specified in the stub zone.
Stub Zone Updates
When a DNS server loads a
stub zone, it queries the zone’s master server for the SOA resource
record, NS resource records at the zone’s root, and A resource records.
During updates to the stub zone, the master server is queried by the DNS
server hosting the stub zone for the same resource record types
requested during the loading of the stub zone. The SOA resource record’s
refresh interval determines when the DNS server hosting the stub zone
attempts a zone transfer (update). Should an update fail, the SOA
resource record’s retry interval determines when the update is retried.
Once the retry interval has expired without a successful update, the
expiration time as specified in the SOA resource record’s Expires field
determines when the DNS server stops using the stub zone data.
You can use the DNS
console to perform the following stub zone update operations:
Reload This
operation reloads the stub zone from the local storage of the DNS server
hosting it.
Transfer From Master
The DNS server hosting the stub zone determines whether the serial
number in the stub zone’s SOA resource record has expired and then
performs a zone transfer from the stub zone’s master server.
Reload
From Master This operation performs a
zone transfer from the stub zone’s master server regardless of the
serial number in the stub zone’s SOA resource record.
Practice:
Deploying a Stub Zone
In
this practice, you create a stub zone on Computer1 that pulls transfers
from the delegated subdomain sub.domain1.local.
Exercise 1:
Creating a Stub Zone
In this exercise, you run
the New Zone Wizard on Computer1 to create a stub zone.
Important
The following
exercise assumes that you have installed the DNS server on Computer2 by
using the Windows Components Wizard. In this case, zone transfers from the
Sub.domain1.local zone are enabled by default but restricted to
authoritative name servers. If instead you have installed the DNS server
on Computer2 by using the Manage Your Server window to add the DNS
server role, zone transfers for all locally hosted zones are disabled by
default. In this case, before beginning this exercise, be sure to
enable zone transfers for the Sub.domain1.local zone and restrict zone
transfers to servers listed on the Name Servers tab. |
1. | From Computer1, log on to Domain1 as Administrator.
|
2. | At a
command prompt, type the following command: dnscmd
computer2/recordadd sub.domain1.local @ ns computer1.domain1.local.
This command adds Computer1 to the Name Servers tab in the
Sub.domain1.local Properties dialog box in the DNS console on Computer2.
|
3. | Open the
DNS console, right-click the Forward Lookup Zones node, and select New
Zone.
The New Zone Wizard launches.
|
4. | Click
Next.
The Zone Type page appears.
|
5. | Select
Stub Zone, clear the Store The Zone In Active Directory check box, and
click Next.
The Zone Name page appears.
|
6. | In the
Zone Name text box, type sub.domain1.local,
and then click Next.
The Zone File page appears.
|
7. | Click Next
to accept the default selection, Create A New File With This File Name.
The Master DNS Servers page appears.
|
8. | In the IP Address text
box, type the IP address currently assigned to Computer2, click Add, and
then click Next.
The Completing The New Zone Wizard page appears.
|
9. | Click
Finish.
The sub.domain1.local zone now appears in the DNS console tree
under the Forward Lookup Zones node.
|
10. | Right-click
the Sub.domain1.local node in the console tree (not the details pane),
and then select Transfer From Master.
Tip If you receive an
error message, wait 10 seconds and try step 15 again. |
|
11. | When the
zone loads successfully, the node shows only three resource records: the
SOA resource record for the zone and the NS resource records pointing
to Computer2 and Computer1.
|
12. | Log off
Computer1. |