Round Robin Example
The Web server
named server1.lucernepublishing.com has three network adapters and three
distinct IP addresses. In the stored zone (either in a database file or
in Active Directory), the three A resource records mapping the host
name to each of its IP addresses appear in this fixed order:
server1 IN A 10.0.0.1
server1 IN A 10.0.0.2
server1 IN A 10.0.0.3
The first DNS client—Client1—that queries the
server to resolve this host’s name receives the list in this default
order. However, when a second client—Client2—sends a subsequent query to
resolve this name, the list is rotated as follows:
server1 IN A 10.0.0.2
server1 IN A 10.0.0.3
server1 IN A 10.0.0.1
Disabling Round
Robin
When you clear the
Enable Round Robin check box, round robin is disabled for the DNS
server. In this case, when clients query the DNS server to resolve the
host name of a multihomed computer, the server always returns the
matching A resource records in the order in which those records appear
in the zone.
Secure Cache
Against Pollution
By default, the
Secure Cache Against Pollution option is enabled. This setting allows
the DNS server to protect its cache against referrals that are
potentially polluting or nonsecure. When the setting is enabled, the
server caches only those records with a name that corresponds to the
domain for which the original queried name was made. Any referrals
received from another DNS server along with a query response are simply
discarded.
For example, if a query is
originally made for example.microsoft.com, and a referral answer
provides a record for a name outside the microsoft.com domain name tree
(such as msn.com), that name is discarded if the Secure Cache Against
Pollution option is enabled. This setting helps prevent unauthorized
computers from impersonating another network server.
When this option is
disabled, however, the server caches all the records received in
response to DNS queries—even when the records do not correspond to the
queried-for domain name.
Name Checking
By default, the
Name Checking drop-down list box on the Advanced tab of the DNS server
properties dialog box is set to Multibyte (UTF8). Thus, the DNS service
by default verifies that all domain names handled by the DNS service
conform to the Unicode Transformation Format (UTF). Unicode is a 2-byte
encoding scheme, compatible with the traditional 1-byte US-ASCII format,
that allows for binary representation of most languages.
Figure 2 shows the four name-checking methods you can
select from the Name Checking drop-down list box, and each is described
in Table 2.
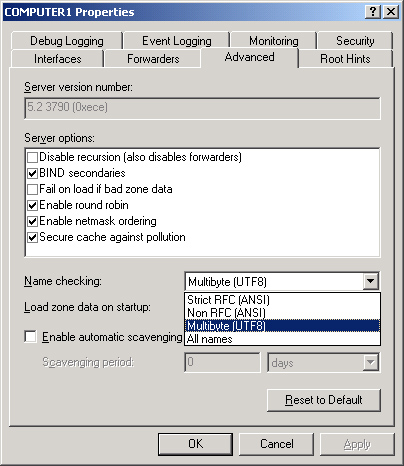
Table 2. Name-Checking Methods
| Method | Description |
|---|
| Strict RFC (ANSI) | Uses
strict checking of names. These restrictions, set in Request for
Comments (RFC) 1123, include limiting names to uppercase and lowercase
letters (A-Z, a-z), numbers (0-9), and hyphens (-). The first character
of the DNS name can be a number. |
| Non RFC (ANSI) | Permits names
that are nonstandard and that do not follow RFC 1123 Internet host
naming specifications. |
| Multibyte (UTF8) | Permits recognition
of characters other than ASCII, including Unicode, which is normally
encoded as more than one octet (8 bits) in length. |
| | With
this option, multibyte characters can be transformed and represented
using UTF-8 support, which is provided with Windows Server 2003. |
| | Names
encoded in UTF-8 format must not exceed the size limits clarified in
RFC 2181, which specifies a maximum of 63 octets per label and 255
octets per name. Character count is insufficient to determine size
because some UTF-8 characters exceed one octet in length. This option
allows for domain names using non-English alphabets. |
| All Names | Permits any naming
conventions. |
Despite the
flexibility of the UTF-8 name-checking method, you should consider
changing the Name Checking option to Strict RFC when your DNS servers
perform zone transfers to non-Windows servers that are not UTF-8–aware.
Although DNS server implementations that are not UTF-8–aware might be
able to accept the transfer of a zone containing UTF-8 encoded names,
these servers might not be able to write back those names to a zone file
or reload those names from a zone file.
You should use the
other two Name Checking options, Non RFC and All Names, only when a
specific application requires them.
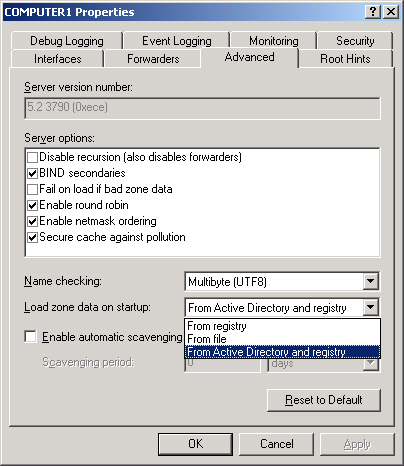
Load Zone Data On
Startup
By default, the Load Zone
Data On Startup drop-down list box is set to the From Active Directory
And Registry option. Thus, by default DNS servers in Windows Server 2003
initialize with the settings specified in the Active Directory database
and the server Registry.
However, this setting
includes two other options, From Registry and From File, as shown in Figure 3.
When you select the From
Registry option for the Load Zone Data On Startup setting, the DNS
server is initialized by reading parameters stored in the Windows
Registry. When you select the From File option, the DNS server is
initialized by reading parameters stored in a boot file, such as those
used by BIND servers.
To use such a file, you
should supply a copy of a boot file from a BIND-based DNS server. On
BIND-based DNS servers, this file is typically called the Named.boot
file. The format of this file must be the older BIND 4 format, not the
more recent BIND 8 boot file format. When a boot file is used, settings
in the file are applied to the server, overriding the settings stored in
the Registry on the DNS server. However, for any parameters not
configurable using boot file directives, Registry defaults (or stored
reconfigured server settings) are applied by the DNS Server service.
Enable Automatic
Scavenging Of Stale Records
By default, the Enable Automatic Scavenging Of
Stale Records option is cleared on the Advanced tab. According to this
setting, DNS servers in Windows Server 2003 by default do not
automatically delete stale or outdated resource records from a zone for
which Aging has been enabled.
When this setting
is enabled, scavenging of stale resource records is performed
automatically at the interval configured in the Scavenging Period.