Firewalls were originally
implemented at the perimeters of networks to protect hosts on a trusted
network against hosts on an untrusted network. The firewall was
implemented on a device with multiple interfaces. One interface
connected to the Internet or public (untrusted) network, and the other
connected to the organization's trusted or private network. These early
firewalls often allowed all outbound packets to pass from the private
network to the public and blocked all inbound communications.
If a web server, DNS
server, FTP server, or other host offered services that should be
accessible from the public network, the host sat outside the firewall.
Later, a second firewall was added to protect these public-facing hosts,
and still later the single-perimeter firewall model added filters that
allowed inbound packets to specific services available on the private
network. The firewall inspected, rejected, or passed on all traffic
attempting to pass through it, based on rules configured on the
firewall.
Perimeter firewalls are
still the most common example of firewalls today. However, a growing
number of organizations are implementing firewalls on internal network
segments, and organizations and individuals are implementing host-level
firewalls. In some cases, the host firewall may be the only perimeter
protection the host receives. These implementations recognize that there
is risk on every network, even one placed behind a perimeter firewall.
Windows Server 2003 and
Windows XP provide a native host firewall, as well as several ways to
create rudimentary firewall services on the host. To implement Windows
host firewalls correctly, and to determine if they are the best
firewalls for the job, you must consider their capabilities.
The first firewalls were little more than packet-filtering routers
. The firewall filtered all traffic bound from one network to the other
and blocked or permitted packets based on internal rules that designated
the ports and IP addresses that were unacceptable. Modern firewalls
also provide stateful filtering
and possibly application layer filtering
. Stateful filtering only permits inbound packets that are responses to
requests from hosts on the private network. The firewall maintains a
table of current outbound connections, including source and destination
IP addresses and ports. When an inbound packet arrives, its information
is compared to entries on the list. If a match is found, the packet is
allowed; if not, it is dropped. An application layer firewall blocks and
permits based on packet content, not just header information. Traffic
bound for port 80 on an internal web server must meet additional
conditions beyond IP address and port information.
Some host firewalls offer all these services and some do not. Another difference between perimeter firewalls
and host-level firewalls is that some host-level firewalls only offer
ingress (or inbound) traffic filtering, while others offer both ingress
and egress (or outbound) filtering.
Figure 1
illustrates a packet-filtering router/firewall. In the figure, a short
rule list indicates the traffic that is allowed to pass. This firewall's
job is to block all port 80 traffic, except traffic bound to the web
server at IP address 192.168.5.60. Note that the log sample included
shows that access to port 80 on 192.168.5.60 is allowed, but access to
port 80 on 192.168.5.10 is blocked.
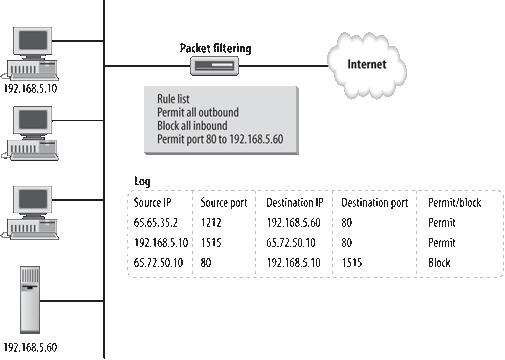
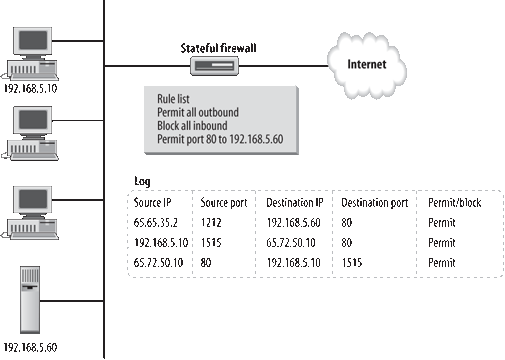
Figure 2
shows a firewall with stateful inspection. Traffic may be passed to
hosts on the internal network in response to their requests. In the
figure, workstation 192.168.5.10 requests a web page from the
Internet-based server and a response is returned.
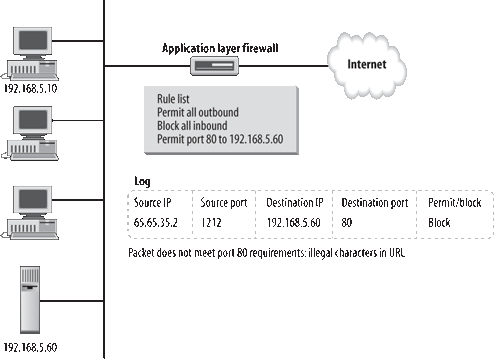
Figure 3
shows an example of an application layer firewall. Packets are
inspected not just by port and IP address, but also by content. Note
that access to the web server, while permitted, is blocked after
examination of the packet. The description in the log, of course, will
be determined by the programming of the application layer firewalls.
Ingress and egress
filtering is an important part of network protection. While ingress
filtering seeks to protect hosts on the internal network from the actions of hosts on the external network, egress filtering
seeks to protect hosts on all networks from hosts on the internal
network. Recent malicious software (or malware) may require connection
to external hosts to complete the infection, may provide remote control
to external attackers, or may infect additional hosts. By provided
egress filtering, you are not only being a good "Internet citizen" but
also containing your losses by preventing the completion of the
infection.
Each of these
capabilities forms an important part of firewall protection and should
be a part of your decisions on which type of firewall, perimeter
firewall, or a host firewall, to select. It may appear to be a simple
decision (that is, select the firewall that offers all of these
services). However, other factors to consider including ease of
management,
protection during startup, cost, and support make that decision more
complicated. In addition, some factors such as ease of management more
important to host-level protection.
A good starting point is an examination of Internet Connection Sharing.