Internet Connection Sharing
(ICS) is not a part of firewall services on Windows systems. However,
if ICS is implemented, a firewall should also be used. ICS allows a
Windows computer to act as a router between other hosts on an internal
network and an external network such as the Internet. It provides
network address translation (NAT), DHCP, and name resolution (DNS Proxy)
services for other computers on the local network. Users can access the
Internet and use the Outlook Express application as if their computers
were directly connected to the Internet. It can also be configured to
allow Internet access to computers on the local network such as web
servers. ICS is most often used in small business and home or home
office networks. Using ICS in a larger organization is not recommended,
because the ICS-enabled computer will respond to DHCP client requests.
Enabling ICS is, therefore, enabling a rogue DHCP server and can
interfere with communications on the local network. (Hosts may obtain
ICS network addresses instead of those required to communicate with
servers and clients on the local network.)
The
Internet Connection Firewall (ICF) and the Network Bridge feature are
available on Windows Server 2003 Standard Edition and the 32-bit version
of Windows Server 2003. They are not available with Windows Server 2003
Web Edition, Datacenter Edition, or the 64-bit versions of Windows
Server 2003. |
|
When used, the ICS
computer is rarely a dedicated router. Instead, the computer running ICS
is used for daily work and pleasure if it is a workstation, and for
other services (such as file and print) if it is a Windows server. You
should understand its function so that you can disable its use in your
Windows domain when necessary, or to ensure that it is securely deployed
if you decide to implement it.
To fully understand the capabilities of ICS, you should have an understanding of the following:
Enabling ICS
Enabling Internet access to local services
Using a network bridge with ICS
Securing ICS
Managing ICS via Group Policy
1. Enabling ICS
In the typical small
network, all computers are connected to the same network and ICS is
implemented to provide all computers access to the Internet. To set up
ICS, select and configure one computer as the ICS computer. The ICS
computer must have two network connections: an Ethernet connection to
the local network and a connection to the Internet (via modem, ISDN,
DSL, or cable modem). If these network connections are in place, and you
have successfully tested the Internet connection, enable ICS as
follows.
Click Start and
select the Control Panel. Double-click Network Connections. Right-click
the network connection to be shared and select Properties. Select the
Advanced tab and click "Allow other network users to connect through
this computer's Internet connection," as shown in Figure 1. In the figure, the network connection has been renamed to Internet.
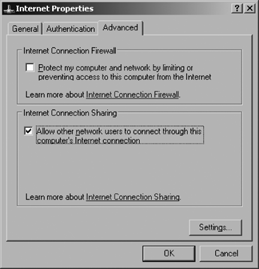
Click OK. Configure clients on the network to dynamically obtain an IP address.
When ICS is enabled, the following changes are made:
The local
network connection is assigned the IP address 192.168.0.1. Consequently,
any connections to other computers on the network will be lost. In
addition, any Internet connections must also be refreshed.
The ICS service is started.
A
DHCP allocator is available to assign addresses with a default range of
192.168.0.0 with a subnet mask of 255.255.255.0. The ICS host address
is reserved, and clients are assigned addresses in the range of
192.168.0.2 to 192.168.0.254.
A local DNS proxy is enabled.
Autodial is enabled.
You cannot disable the DHCP allocator or change the default range of addresses.
ICS
can be used to enable all computers on a network to access a VPN
connection. The VPN connected must be ICS-enabled. For other computers
to share the connection, the VPN connection must first be created on the
ICS computer. |
|
2. Enabling Internet Access to Local Services
ICS uses NAT to provide
computers on the internal network access to the Internet. While NAT is
not meant to provide security for internal hosts, external hosts do not
know the actual IP address of internal hosts. Therefore, if you want to
provide access to services such as web services, FTP services, or SMTP
services, you must explicitly configure access. Begin by clicking Start
and selecting the Control Panel. Double-click Network Connections.
Right-click the ICS network connection and select Properties. Select the
Advanced tab and click the Settings button to display a list of
services, as shown in Figure 2.
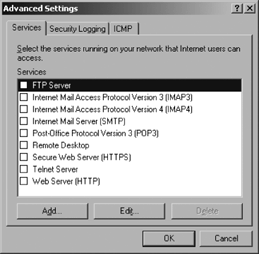
Click to select the
service you wish to provide access to. On the Service Settings page
enter the name of the host that offers this service, as shown in Figure 3, then click OK.
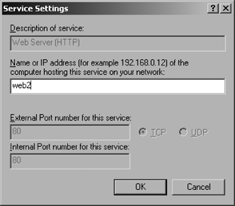
Click OK twice to exit the network settings Properties pages.
3. Using a Network Bridge with ICS
In a more complex
small network, the ICS computer may have more than one private network
connection. To enable ICS when the host computer is connected to
multiple LAN segments, you must bridge the private networks before
enabling ICS
Begin by clicking
Start and selecting the Control Panel. Double-click Network Connections.
Select and hold down the Shift key and then click each of the adapters
for the connections that should be included in the bridge. Wireless
network connections, Ethernet, IEEE-1394 adapters, and telephone line
connections can be included in a bridge. Do not include the network
connection to the Internet.
Release the Shift key.
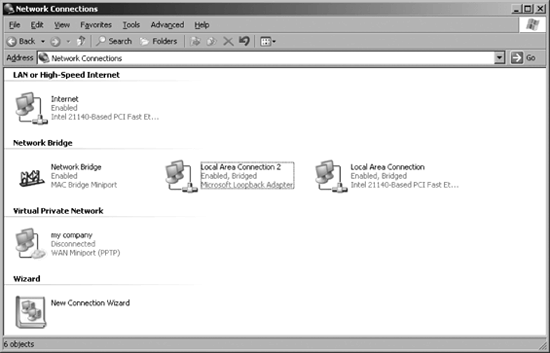
Click on the Advanced menu and select Bridge Connections. The bridge is
added to the Network Connections page and identifies the network
connections that are bridged, as shown in Figure 4.
Select the Internet network connection and enable ICS, as explained in the earlier section "Enabling ICS."
Do
not bridge connections to the Internet. If you do so, you expose hosts
on the internal network to the Internet. Some types of Internet
connections (such as DSL, modem, and cable modem connections) cannot be
added to a network bridge. Other connections (such as an Ethernet
connection to a router that is connected to the Internet) can be
bridged, but it should not be. |
|
4. Securing ICS
ICS does not add security
to the Internet connection. It does, however, provide NAT services that
hide the IP address of the hosts on the internal network. Even so, it
is
still possible for
an Internet-based attack to be successful. It is also possible to
misconfigure ICS and expose the ICS host and computers on the private
network to the risk of compromise. Take the following steps to secure
ICS services:
Implement
a firewall. A separate firewall can be placed between the ICS host and
the Internet, the Windows built-in firewall can be enabled, or some
other personal firewall can be installed. Be sure not to set up ICS
without turning on the Windows Firewall. If no other firewall sits
between the ICS host and the Internet, then the Windows Firewall (or
some other firewall) should be used.
When
configuring ICS, ensure that ICS is enabled on the Internet connection,
not on the connection to the private network. If ICS is configured on
the private network connection, hosts on the internal network are
subject to attack from the Internet if the ICS host is connected to the
Internet.
If a network bridge is created, ensure that the Internet connection is not part of the bridge.
Avoid
providing access to private network services. If they must be allowed,
configure them via the Settings page for ICS, and only configure those
services that are necessary.
Harden the ICS host computer and, if at all possible, dedicate it to this task.
5. Managing ICS via Group Policy
By default,
management of ICS is not restricted via Group Policy. A local
administrator can enable the ICS, on a member computer. A good practice
is to disable this service using Group Policy. The following two
location-aware Administrative template policies can be configured to do
so:
Prohibit use of Internet Connection Sharing on your DNS domain network.
When enabled,
administrators cannot enable ICS on the local computer. When disabled or
not configured, administrators can enable ICS on the local computer.
Prohibit installation and configuration of Network bridge on your DNS domain network.
When enabled,
administrators cannot create a network bridge on the local computer.
When disabled or not configured, administrators can create a network
bridge on the local computer.
Location-aware
policies operate only when a computer is connected to the same DNS
domain network as the one it was connected to when the policy was
refreshed. This means that administrators of laptop computers will not
be able to enable ICS when the laptop is connected to its domain, but
they will be able to enable ICS when the laptop is connected to a
different network (such as a hotel or conference network).