2.2. Modifying firewall behavior using the Windows Firewall INF file and unattend.txt
If the service is installed without
modification, then the firewall is installed as enabled, and all
unsolicited traffic will be blocked. Administrators should configure the
service pack installation so that the firewall is installed with
appropriate settings for their networks. Use the Windows Firewall INF
file (netfw.inf) when performing an interactive installation. Use the unattend.txt file, to configure settings for unattended installations of the service pack.
The Windows Firewall INF file (netfw.inf)
is a configuration file that can be used by administrators to modify
the behavior of the Windows Firewall. Use Notepad or another text editor
to modify netfw.inf and use the new
version during installation of the service pack to configure the
firewall during installation. Modify the local netfw.inf after installation to modify firewall behavior. The netfw.inf
file is located on a Windows XP CD-ROM in the I386 directory. There are
several reasons why changes to the default behavior are necessary,
including the following:
A third-party vendor firewall is your default.
Installed programs require filters configured for the Windows Firewall to enable traffic.
Network services such as remote management are used in your network and, therefore, specific ports must be open.
To modify behavior, modify the ICF.AddReg.DomainProfile and/or ICF.AddReg.StandardProfile
sections of the file. These profiles determine how the firewall is
configured when the computer is connected to a domain or not,
respectively. If the Windows computer is not a member of a domain, the ICF.AddReg.StandardProfile will always be enforced.
To reconfigure the netfw.inf file on an existing Windows XP SP 2 system, use Notepad or another text editor to open the %windir%\Inf\netfw.inf file, as shown in Figure 8.
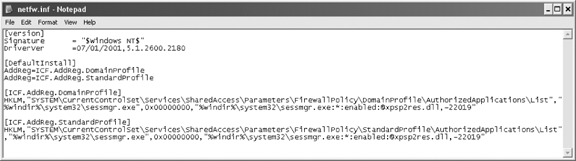
Make changes and save the file. Run the command netsh firewall reset
from a command prompt. Firewall behavior is determined by registry
settings included in the file. To make changes, add or adjust values
located at the paths:
or:
Table 2 lists and describes the values that may be changed in the netfw.inf file.
Table 2. Firewall INF settings
| Value | Setting | Description |
|---|
| EnableFirewall | 0x00010001,1 | The firewall is enabled. |
| DoNotAllowExceptions | 0x00010001,1 | If
the firewall is enabled and this setting is configured, the firewall
blocks all unsolicited traffic, including that identified in an
exception list. |
| DisableNotifications | 0x00010001,1 | Turns
off notification when a program not already included in the exceptions
list attempts to add itself or its traffic to an exceptions list. |
| DisableUnicastResponsesToMulticastBroadcast | 0x00010001,1 | Prevents
incoming unicast response packets. By default, the firewall allows
these packets in responses to outgoing multicast or broadcast packets. |
| RemoteAdminSettings: Enabled | 0x00010001,1 | Enables
remote administration by statically opening ports TCP 135 and TCP 445
to unsolicited incoming traffic. Communication via named pipes is also
permitted. These ports are required for Remote Procedure Call (RPC) and
Distributed Component Object Model (DCOM) communications. They are
blocked by default. When this setting is enabled, additional ports
required by RPC are dynamically opened. |
| RemoteAdminSettingsRemoteAddresses | 0,00000000,"scope" | When RemoteAdminSettings is enabled, you may specify a scope of addresses from which this traffic is allowed. |
| IcmpSettings | "ICMP MessageType",0x00010001,1 | Allows ICMP message types as specified. |
| GloballyOpenPorts\List | "Port number:protocol",
0x00000000, "port number:protocol:scope:mode:port's friendly name" | Statically opens this list of ports. (See the following discussion.) |
When opening TCP 135 and TCP 445 for remote
administration, you should carefully limit the scope of addresses from
which traffic may be accepted. By default all IP addresses are accepted,
and this increases risk unacceptably. A large number of attacks are
based on using these Windows ports. Narrow the scope of acceptable
addresses to those used by administrators. While you can use the term
LocalSubnet in the Firewall INF file to restrict incoming traffic to the
local subnet, a better option is to create a custom scope by including a
dotted decimal subnet mask or a prefix length. A list of IP addresses
delimited by commas is also acceptable. Examples of scopes are
192.168.0.0/255.255.255.0 and 192.168.5.6, 192.168.5.10, 192.168.5.12.
When
configuring scope by creating a list of IP addresses, do not leave
spaces between the IP addresses in the list, or else the list will be
ignored and traffic from all IP addresses will be accepted. |
|
Scope may also be limited when defining statically opened ports. When defining the entry for GloballyOpenPorts\List,
you should consider the scope option as well as add information to help
identify the port in the Windows Firewall GUI. It is also possible to
list ports that should not be statically opened. In the parameters for
the option, use the following:
Port number
This is the number assigned to the port.
Protocol
This is either TCP or UDP.
Scope
This is an IP address range.
Mode
This is either "enabled" or "disabled." Use disabled to explicitly require the port not to be statically opened.
Port's friendly name
This is a description you provide to help identify the statically opened port in the GUI (for example, "web server TCP 80").
An unattended installation of the service pack
can reduce the need to provide feedback during service pack
installation. Options for creating different types of service pack
installations (including an unattended one) are fully discussed in the
documentation accompanying SP2. To read and use the documentation prior
to installation, unzip the deploy.cab file located on the service pack CD-ROM. This file is located in the Support\Tools folder. Extract the deploy.chm file and double-click on it to open. Specific information on unattend.txt can be found by extracting and consulting the ref.chm help file.
If you are installing from a command line or simple script, develop an unattened.txt file and use it during installation by entering xpsp2.exe unattend:unattend.txt.
While there are many options that can be configured, those important to
Windows Firewall installation are listed here. Modifications to the unattend.txt file that affect the Windows Firewall operation are in the sections.
[WindowsFirewall]
This references the other sections.
[WindowsFirewall.Domain]
These are settings that affect the computer when it is connected to the domain.
[WindowsFirewall.Standard]
These are settings that affect the computer when it is not connected to the domain.
[WindowsFirewall .program_name]
This adds a program by the name of program_name to the exceptions list.
[WindowsFirewall .service_name]
This adds a predefined service such as File and Print to the exceptions list.
[WindowsFirewall .portopening_name]
This adds a port to the exceptions list.
[WindowsFirewall .icmpsetting_name]
This adds ICMP message types to the exception list.
Example 1 is a sample firewall section from the unattend.txt file as described in ref.chm. In the file, the number 1 is used to indicate that the feature is enabled.
Example 1. Sample firewall section from unattend.txt
[WindowsFirewall]
Profiles = WindowsFirewall.Domain, WindowsFirewall.Standard
LogFile = %WINDIR%\Pfirewall.log
LogSize = 4096
LogDroppedPackets = 1
LogConnections = 1
[WindowsFirewall.Standard]
Type = 3
Mode = 1
Exceptions = 1
Notifications = 1
MulticastBroadcastResponse = 1
AllowedPrograms = WindowsFirewall.RemoteAssistance
Services = WindowsFirewall.RemoteDesktop
PortOpenings = WindowsFirewall.WebService
IcmpSettings = WindowsFirewall.EchoRequest
[WindowsFirewall.Domain]
Type = 3
Mode = 0
[WindowsFirewall.RemoteAssistance]
Program = "%WINDIR%\System32\Sessmgr.exe"
Name = "Remote Assistance"
Mode = 1
Scope = 2
Addresses = "192.168.0.5,LocalSubnet"
[WindowsFirewall.RemoteDesktop]
Type = 2
Mode = 1
Scope = 2
Addresses = "192.168.0.5,LocalSubnet"
[WindowsFirewall.WebService]
Protocol= 6
Port = 80
Name = "Web Server (TCP 80)"
Mode = 1
Scope = 2
Addresses = "192.168.0.5,LocalSubnet"
[WindowsFirewall.EchoRequest]
Type = 8
Mode = 1
|
2.2.1. Modifying firewall settings using the Control Panel
After service pack installation, the "Protect
my computer and network by limiting or preventing access to this
computer from the Internet" checkbox is removed from the Advanced tab of
a network connection Properties pages. While the Setting button
remains, it launches the new Firewall applet in the Control Panel.
Members of the local Administrators group can configure general settings
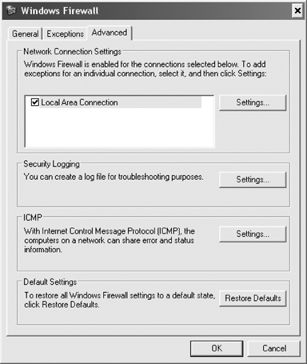
and exceptions by using this applet. Figure 9 show the page from the Advanced tab, while Table 3 lists and describes the settings available on this page.
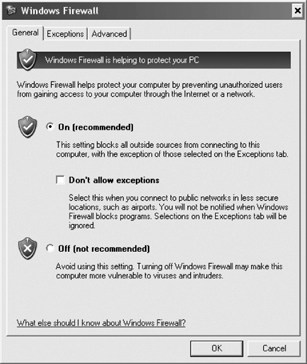
Table 3. General firewall settings
| Setting | Description |
|---|
| On | The default. Enables the firewall. |
| Don't allow exceptions | When
selected, all traffic (even that configured via exceptions) is not
allowed. Use this checkbox to temporarily disable exceptions when using
the computer in a more risky situation (for example, in a hotel room or
at a public setting such as a conference or wireless hotspot). |
| Off (not recommended) | Disables the firewall. |
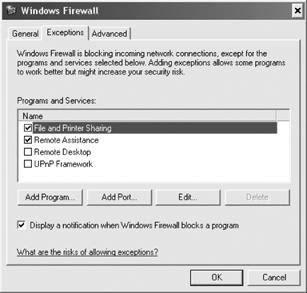
Click the Exceptions tab, as shown in Figure 10,
to select or add programs that external clients are allowed to access.
Selecting the program in the interface (or by using the Add Program
button) asks the Windows Firewall to determine which ports should be
opened.
By
default, both File and Printer Sharing and Remote Assistance programs
are enabled. Both of these programs may be necessary to allow remote
administration. However, if they are not used for remote administration,
disable them here by unchecking the box. |
|
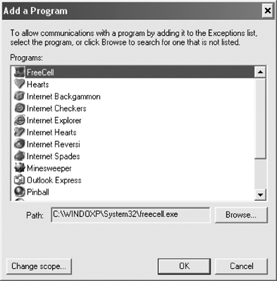
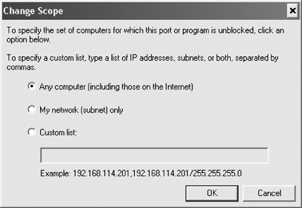
Selecting the Add Program button allows browsing to any executable on the local hard drive, as shown in Figure 11. The "Change scope... " button is used to restrict the computers that can access these local programs, as shown in Figure 12. You
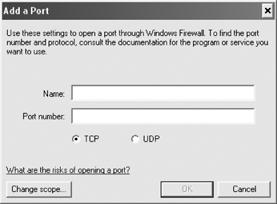
can also simply add a port filter using the "Add port" button, as shown in Figure 13.
Settings configured by using the Windows
Firewall applet are set for all network connections by default. Use the
Advanced tab shown in Figure 10 to configure settings for individual network connections, to configure logging, ICMP, or to restore the default settings.
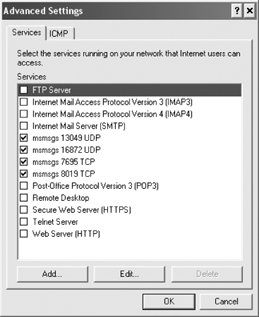
Selecting an interface, clicking the Settings
button, and choosing the Advanced tab provides you with options for
configuring different services and ICMP settings for unique network
interfaces, as shown in Figure 15.
2.2.2. Modifying alerting and notification using the registry
Three registry settings values can be used to
control the alerting and notification feature. Each one represents one
of the security tools. Add the DWORD values to HKEY_LOCALMACHINE\SOFTWARE\Microsoft\Security Center and change the value to 1 in order to suppress the alert and notification. The values are as follows:
AntiVirusDisableNotify
FirewallDisableNotify
UpdatesDisableNotify
2.2.3. Modifying firewall behavior using Group Policy
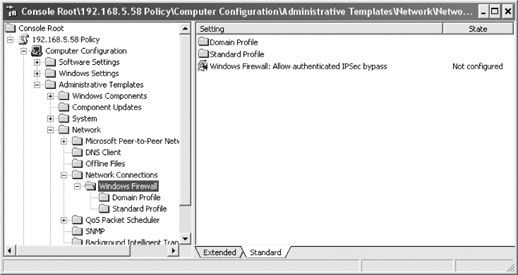
In an Active Directory domain, new Group Policy options can be used to manage the behavior of the Windows Firewall
. Windows Server 2003 or Windows 2000 domain controllers can be configured to
support the deployment of these options for
Group Policy Objects (GPOs) linked to organizational units (OUs) that
include computer accounts for updated Windows Server 2003 SP1 and/or
Windows XP SP2 computers.
To use the settings, install the service pack
on a client computer joined to a test network domain. The service pack
includes an updated system.adm file.
After the post service pack installation reboot, log on as an
administrator on the updated system and either add the Group Policy
Object Editor snap-in to an MMC console, or open Group Policy Management
Console. Select a GPO on a DC in the test network domain of which the
client computer is a member. Expand the console tree and browse to
Computer Configuration → AdministrativeTemplates → Network →
NetworkConnections → WindowsFirewall. The updated system.adm
file on the client can be used to configure the Group Policy. However,
to use the new settings, you must use an updated system.adm file to
replace the system.adm file on all
domain controllers. You should test the use of these new settings in a
test network before deploying on your production network. When
satisfied, update all production GPOs that support updated clients.
Configure the policy. The first setting, shown in Figure 16, determines if authenticated IPSec traffic is excluded from the firewall's rule sets.
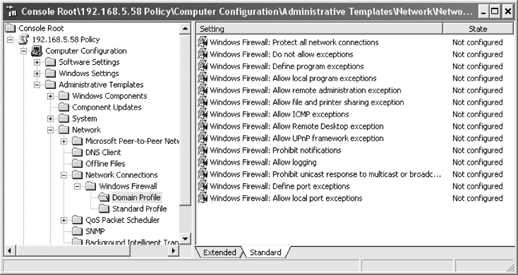
Additional policy settings can be configured separately for standard or domain profiles. Figure 17 shows a list of policy settings.
Configure the setting for "Allow authenticated
IPSec bypass" and then configure settings for both profiles. If "Allow
authenticated IPSec bypass" is enabled, then the computer will not
process IPSec-secured traffic from specified computers. IPSec-secured
traffic is allowed by default. To enable this setting you must also add a
Security Descriptor Definition Language (SDDL) string for the group
accounts for the computers the policy should apply to. The string is
added to the policy definition in the Group Policy properties. An SDDL
string is of the form O:DAG:DAD(A;;RCGW;;;sid)
where sid represents the Security Identifier (SID) of a group account. To obtain the SID, use the Windows Resource Kit tool Getsid.exe.
Because Getsid is usually used to compare SIDs, you must enter the DC
and group name twice. A sample command line that can be used to specify
the DC DC1 group REDTeam is as follows:
Getsid \\DC1 REDTeam \\DC1 REDTeam
Remember to establish settings for the
appropriate profile (domain or standard). Profile settings are located
underneath the Standard profile and Domain profile path. The domain
profile is used when the computer is connected to the domain, and the
standard profile is used when it is not. If neither of the profiles is
configured, their defaults are used. The preservice pack upgrade setting
"Prohibit use of Internet Connection Firewall on your DNS domain
network" is still available for use in networks where some computers
exist that have not been updated. Each profile includes the settings
described in Table 4.
Table 4. Windows Firewall Group Policy settings
| Setting | Description | Ports opened | Microsoft recommendation |
|---|
| Protect all network connections | All connections will have the firewall enabled. | None | Enabled |
| Do not allow exceptions | All
unsolicited traffic is dropped, even if exceptions are configured. If
the setting "Protect all network connections" is not set, a local
administrator can bypass the firewall entirely by disabling it. | None | Not configured |
| Define program exceptions | Defines allowed unsolicited traffic. The full path for the program must be identified. Variables such as %Program Files%
can be used in the path statement. Windows Firewall only opens ports
for these programs when they are running and listening for traffic. | Those defined | Configured for those applications allowed by policy |
| Allow local program exceptions | Enables local configuration of exceptions. | Those defined | Enabled |
| Allow remote administration exception | Enables
remote administration using tools such as MMC consoles and Windows
Management Instrumentation (WMI). If this setting is disabled, SVCHOST.EXE and LSASS.EXE are added to the programs exception list with a status of disabled. | TCP 135 and 445, as well as dynamically required RPC ports and incoming ICMP Echo Request messages | Disabled |
| Allow file and print sharing exception | Enables file and print traffic. | UDP 137, UDP 138, TCP 139, TCP 445, and incoming ICMP Echo messages | Enabled only if computers are file and print servers |
| Allow ICMP exceptions | Specifies ICMP traffic types that are allowed. | ICMP | Enabled for diagnostic or management purposes |
| Allow Remote Desktop exception | Opens ports for a Remote Desktop connection. | TCP 3389 | Enabled if remote desktop management is used |
| Allow UPnP framework exception | Enables unsolicited UPnP message traffic. | UDP 1900, TCP 2869 | Enabled if UPnP devices are used on the network |
| Prohibit notifications | Disables
notification. When an application starts to listen on a port, the
Windows Firewall adds the program to the exceptions list with a status
of disabled and then notifies the user with a request to allow or
disallow traffic to this port. | Those required by the program if this setting is not configured or disabled | Disabled |
| Allow logging | Configures
the log file and enables logging of dropped traffic and successful
connections. If enabled, the path to the log file must be selected or
added and a maximum size must be specified. | N/A | Not configured |
| Prohibit unicast response to multicast or broadcast requests | If
enabled, discard unicast packets received in response to multicast or
broadcast request messages. By default (if disabled or not configured),
these packets are allowed for three seconds following a multicast or
broadcast message. Unicast messages that are a response to a DHCP
broadcast message are not dropped if this setting is enabled. It can
interfere with NetBIOS name conflict detection. NetBIOS name conflict
detection can prevent the use of duplicate computer names on the
network. | None | Disabled |
| Define port exceptions | Specifies
exceptions using ports. The port number, type (TCP or UDP), status
(Enabled or Disabled) must be entered. Scope is optional. | Those defined | Enabled as required |
| Allow local port exceptions | Local configuration of port exceptions is allowed. | Those defined | Enabled if required |
If
ports are explicitly opened to allow unsolicited traffic, setting an
exception to explicitly disable them via program name will not prevent
the program from running or block them from receiving traffic. |
|
When configuring exceptions, take advantage of
the scope setting. The scope setting allows you to specify computers
from which this type of traffic is allowed. Always keep in mind that the
firewall protects the computer from attacks that use specific ports.
These same ports may be used by legitimate traffic. If you open these
ports for legitimate traffic, you also open it for malicious traffic.
You can limit the risk of compromise by specifying the computers from
which traffic is accepted. This is not a foolproof solution, but it does
limit your risk.
If
you specify programs more than once and use conflicting scopes or
status, then any system specified by any entry can send messages. |
|
2.2.4. Modifying firewall behavior using Netsh
Netsh is a network configuration utility that
can be used at the command line or in scripts. Syntax is defined in the
whitepaper Deploying Windows Firewall Settings for Microsoft Windows XP with Service Pack 2. Netsh commands are available to configure the Windows Firewall and include the following:
Add allowedprogram
This adds program exceptions.
Set allowedprogram
This modifies the settings of an existing program exception.
Delete allowedprogram
This deletes a configured program exception.
Set icmpsetting
This specifies ICMP-accepted traffic.
Set multicastbroadcastresponse
This specifies a unicast response to a muiltcast or broadcast request.
Set notifications
This enables or disables notifications.
Set logging
This configures logging options.
Set opmode
This sets the mode to Enable, Disable, or "Do not allow exceptions."
Add portopening
This creates a port-based exception.
Set portopening
This modifies the settings of an existing port-based exception.
Delete portopening
This deletes a configured port-based exception.
Set service
This enables or disables predefined file and printer sharing, remote administration, remote desktop, and UPnP exceptions.
Reset
This resets the configuration to the default.
Show
This is used to display the current configuration.
2.2.5. More modifications
Following are a few other changes to the firewall and its administration:
Don't allow exceptions operating mode
In addition to Enabled or Disabled, there
is a new operating mode that prevents the addition of exceptions. If
this mode is established, all incoming traffic is dropped, even if
exceptions are configured.
Incoming traffic scoping
Ports may be statically opened for use from specific IP addresses only.
|
If the firewall is enabled, by default you
will not be able to use the Resultant Set of Policy (RSoP) snap-in to
determine the Group Policy status on a remote Windows XP client. If you
wish to retain the ability to use RSoP remotely while keeping the
Windows Firewall enabled, make the following changes to Group Policy:
On the local computer, enable the Windows
Firewall Allow remote Administration exception Group Policy settings.
This setting is located at Computer Configuration → Administrative
Templates → Network → Network connections → Windows Firewall → [Domain |
Standard] Profile\.
To use the Group Policy Management Console
(GPMC) on the administrative computers with the firewall enabled,
upgrade to GPMC SP1. GPMC uses a callback on the administrative
computer. The firewall blocks the callback mechanism of GPMC. To keep
the firewall enabled on the administrative computer, upgrade to GPMC SP1
on a computer that does not use the callback mechanism.
To use RSoP, make these changes to the
administrative computer: Enable the Windows Firewall: Define the program
exceptions option and enter the full path to unsecapp.exe. (By default, unsecapp.exe is located in the C:\Windows\System32\Wbem folder.) Enable the Windows Firewall. Define the port exception policy to open port 135 or
enable the Windows Firewall. Allow a remote administration exception in
the Group Policy setting on the administrative computer. |
Excepted traffic specified by program name
This allows traffic from programs
determined by program name, such as File and Print Sharing or Remote
Assistance. (Program exceptions can also be specified by port numbers.)
Support for Ipv6
This offers built-in support for Ipv6 traffic.
Global configuration settings
Firewall settings will apply to all
network connections. You do not have to reconfigure settings when
multiple network connections are available on the same computer.
(Settings can be configured for individual settings using scope
settings.
New application programming interfaces (APIs)
New APIs provide for more granular programmatic control. For information on these APIs and how to use them, study the Windows Firewall section of the Windows Software Development Kit.
IPSec Policy Aware
If IPSec policies are configured, the
Windows Firewall opens UDP ports 500 and 4500 to allow Internet Key
Exchange (IKE) traffic.
2.3. Windows Server 2003 SP1
The Windows Server 2003 firewall will be updated
by SP1 and will work in a similar fashion to the Windows Firewall
post-Windows XP SP2, with the exception that the Windows Firewall is
disabled by default on Windows Server 2003. Since the firewall is not
enabled by default, if you wish to use the firewall, you must enable it
and configure exceptions. If you do so, the server should be restarted
to enable the operating system to automatically add entries to the
exceptions list for ports opened by programs that are already installed.
Host-based firewalls can provide
excellent protection for servers and workstations. They will do so only
if they are enabled and configured. Major changes to the Windows
Firewall for XP were made in Service Pack 2, and similar changes are
expected for Windows Server Service Pack 1. These changes include
increased configuration control, including new Group Policy and registry
settings, scope configuration for settings, and, for Windows XP, the
firewall is enabled by default. In addition to host-based firewalls,
perimeter firewalls should be in place between trusted and untrusted
networks. The RRAS firewall can provide rudimentary firewall services
for this purpose. The RRAS firewall may not be appropriate in all
situations. You should always consider your firewall requirements before
selecting a firewall.