Securing shared folders
Windows uses two types of permissions to secure shared folders. These are shared folder permissions and file/folder permissions:
Shared folder permissions
—Shared folder permissions are applied to the shared folder only and
not to the contents it contains. This means that you cannot use shared
folder permissions to provide a different level of security to
subfolders or files within the share. Furthermore, shared folder
permissions are effective only when accessing the shared folder from the
network. If someone tries to access the folder by logging on to the
computer in which it is shared, shared folder permissions do not limit
access. In most cases, it is recommended that the use of share
permissions be limited and file permissions be used to restrict access
to share folders and the files they contain.
File/folder permissions —File/folder
permissions use NTFS security to limit access to files and folders on a
computer. They are similar to shared folder permissions in that you can
assign access to local or domain users and groups; however, file/folder
permissions provide better security and more granularity when assigning
access. For example, with file/folder permissions you can give domain
users access to client data share, but limit access to a file within
that share to only people in the accounting department. In most cases,
file/folder permissions are the preferred method for managing access to
network file shares and the files and folders they contain.
When both shared folder and
file/folder permissions are used, the most restrictive applies. For
example, if John is given Full Control using shared folder permissions
and is given Read-Only using file/folder permissions, his effective
permissions are Read-Only. You should also understand that every time a
deny permission is set, it trumps any other permissions. For example,
let us assume that John is a member of the accounting group. John’s
account is given Full Control permission to the ClientData shared
folder. The accounting group is denied read permissions to the
ClientData shared folder. Since John’s account is a member of the
accounting group, his effective permissions deny him access to the
ClientData shared folder even though his individual account has rights
to this folder. When multiple file/folder permissions are used, the
effective rights are a combination of the user and group rights unless
an explicit deny is used. For example, assume that John is a member of
the accounting group. John is given read access to the ClientData shared
folder. The accounting group is given modify rights to the shared folder. John’s effective permissions to the ClientData shared folder are modify.
Now that you have an
understanding of permissions, we will take a look at the permissions
setup on the shared folder we created in the previous section.
1. | Right click on the shared folder and select Properties.
|
2. | Click on the Sharing tab. Then click the Advanced Sharing button (see Figure 5).
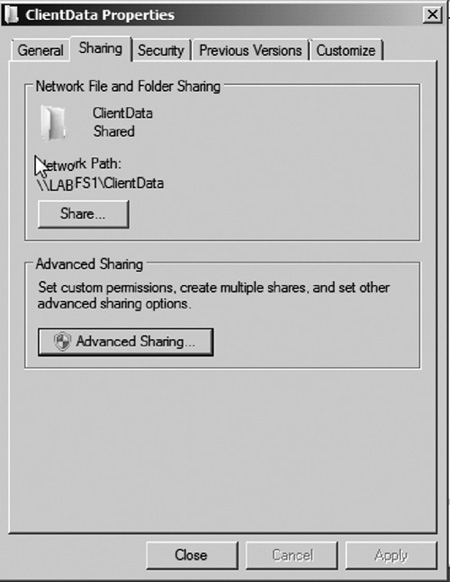
|
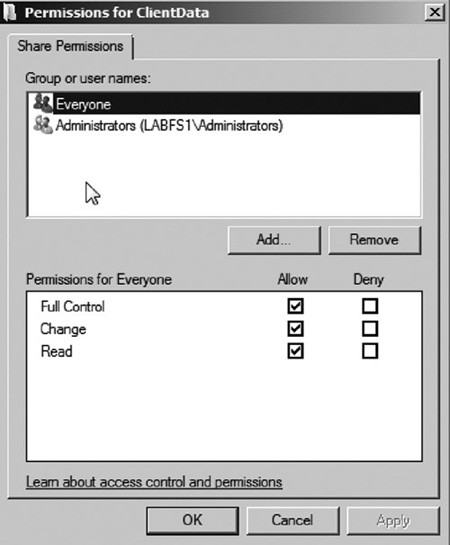
3. | Click the Permissions button. This will display the shared folder permissions as seen in Figure 6.
Notice that by default, the Everyone group is assigned Full Control
access at the shared folder level. This does not necessarily mean that
everyone has access to this share folder. You will see that file/folder
permissions restrict who can access the share folder. Remember that the most restrictive of file/folder permissions and shared folder permissions is used.
|
4. | Click Cancel. Then click the Security tab.
|
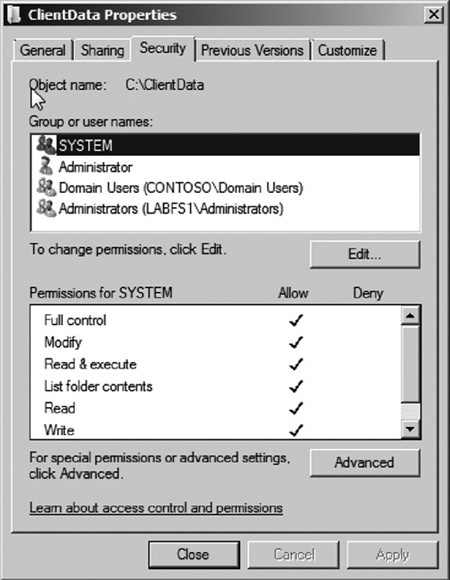
5. | You will now see the file/folder permissions for the folder (shared) as seen in Figure 7. You will notice that three groups and one user have access in our example:
- SYSTEM —This is the group used
by the operating system to perform tasks to the folder. In most cases,
you will want to leave this permission assigned.
- Administrator —This is the local computer administrator account.
- Domain Users
—This is the domain group that we assigned read access to during
initial setup of the share. Notice that access was set up using
file/folder permissions opposed to shared folder permissions.
- Administrators
—This is the local computer administrators group. By default the
administrators group is granted access to all shared folders unless
explicitly removed or denied access.
|
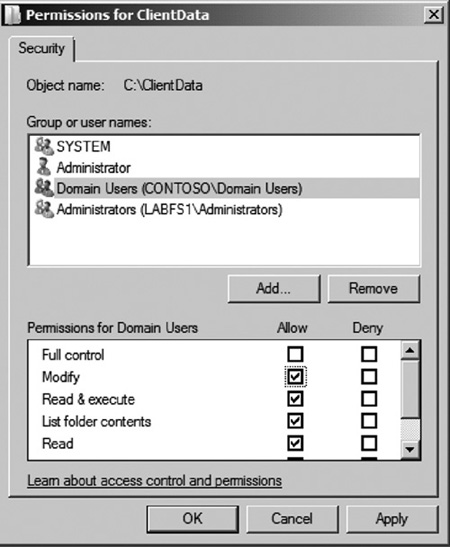
6. | From
the security tab you can add, remove, or change access rights to the
shared folder. For example, let us give domain users modify rights to
the ClientData shared folder. This will give them the ability to not
only read files but also add and change files within the shared folder.
To give domain users modify rights, click on the Edit button. Then select the Domain Users group. Next select the Allow checkbox as seen in Figure 8. Click the OK button. Users within the domain users group now have modify access to the ClientData folder.
|
As you can see,
file/folder permissions provide the ability to give access to files and
folders in a very granular fashion. File/folder permissions have six
main access levels. They are defined in Table 1.
Table 1. Standard Permissions
| Permission | Access |
|---|
| Full Control | This
is the highest level of access to a file or folder. Full control gives
the user full access to the file or folder allowing him to make any
changes including changing permissions and taking ownership. |
| Modify | Modify
permission gives the user the ability to make changes to existing files
or create new files. This is typically the permission used to give
users read/write access to a folder/file. |
| Read & Execute | Read
& Execute access gives the user the ability to read files and
folder contents and execute applications from a folder. This is the
permission typically used to give a user read-only access to a folder. |
| List folder contents | List
folder contents does just that. It gives the user the ability to only
list the contents of a folder. This right does not give the user the
ability to open files within the folder. |
| Read | Read
access gives the user the ability to read files and folder contents.
This access is automatically added when Read & Execute is selected. |
| Write | Write access gives the user the ability to write new files and folders, but not necessarily the ability to read them. |
In
most cases, standard permissions can be used to provide the level of
access required by users. However, there may be occasions where more
granular access settings may be required. In those cases, you can use
Special Permissions to set user access. Special permissions can be
accessed by selecting the Advanced button from the Security tab. Then click Change Permissions. Select the user or group whose permissions you wish to change, then click Edit. The special permissions window will appear as seen in Figure 9. Here, you can set special permissions for the selected file or folder. Special access permissions are defined in Table 2.
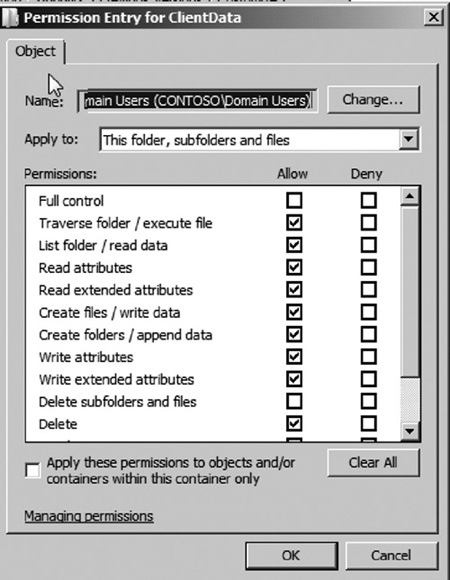
Table 2. File/Folder Special Permissions
| Permission | Access |
|---|
| Traverse folder/execute file | Traverse
folder allows you to move through a folder to access a subfolder. For
example, if you do not have access to the ClientData share, but do have
access to a subfolder named invoices in the ClientData share, the
traverse folder permission gives you the ability to move through the
ClientData folder to access the invoices subfolder. Execute file
permission gives the user the ability to execute files. |
| List folder/read data | List
folder gives the user the ability to view files and folders within a
folder. Read Data gives the user the ability to open a file with
read-only access. |
| Read attributes | Read
attributes give the user the ability to view the attributes of a file
or folder. For example, with this permission a user could look at the
properties of a file or folder to see if it was hidden or classified as a
system file. |
| Read extended attributes | The
read extended attributes permission gives the user the ability to view
metadata fields related to a file or folder. For example, Microsoft Word
documents include an author field. Read extended attributes gives the
user the ability to view this field. |
| Create files/write data | Create files allows the user to create files within a folder. Write data allows the user to overwrite existing data. |
| Create folders/append data | Create
folders gives the user the ability to create new subfolders within the
folder. Append data gives the user the right to add new data to a file. |
| Write attributes | Write
attributes gives the user the ability to change the attributes of a
file or folder. For example with Write attributes rights, a use can make
a file or folder hidden. |
| Write extended attributes | Write
extended attributes gives the user the ability to make changes to
metadata fields such as the author field in Word documents. |
| Delete subfolders and files | This
permission gives the user the ability to delete subfolders and files in
the current folder, even if the user does not have explicit delete
permissions on the subfolders or files. |
| Delete | The Delete permission gives the user the ability to delete the current file or folder. |
| Read permissions | Read
permissions access gives the user the ability to view the current
permissions set on the selected file or folder. Read permissions does
not give the user the ability to actually read the contents of the file
or folder. |
| Change permissions | Change
permissions access gives the user the ability to manage access rights
to the current file or folder. The user can add, remove, or change any
of the current permissions on the file or folder. |
| Take ownership | Take ownership gives the user the ability to take ownership of a file or folder. |
Special permissions give
you the ability to maintain very granular control over file and folder
access. You should always properly document permissions on
network-shared folders.
|
As
best practice, you should limit assigning permissions to users
directly. Use groups whenever possible when assigning permissions to
files and folders.
|
Permissions inheritance
Inheritance is another
important aspect of user access for files and folders. Unless specified
otherwise, folders and files inherit the permissions of their parent
folder. For example, if you create a new folder named invoices in the
ClientData shared folder, it will automatically assume the same
permissions as the ClientData folder.
There may be occasions where
you need to prevent permissions inheritance on specific files or
folders. To remove inherited permissions, perform the following:
1. | Right click on the subfolder or file within the parent folder and select Properties.
|
2. | Select the Security tab. Then click the Advanced button.
|
3. | Click Change Permissions. This will display the Advanced Security Settings window as seen in Figure 10.
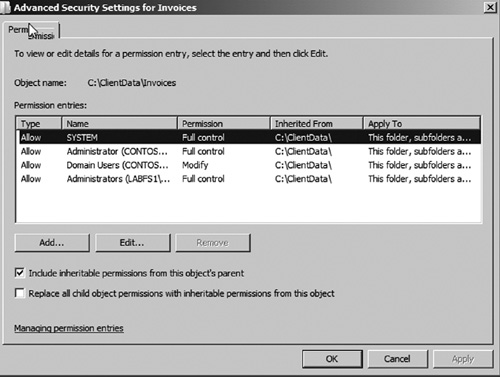
|
4. | Notice that the option Include inheritable permissions from this objects parent is selected. To remove permission inheritance, deselect the checkbox.
|
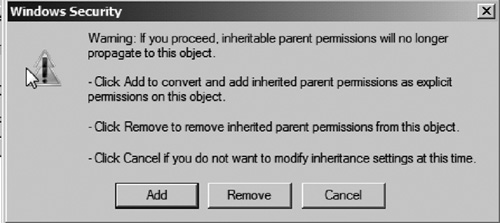
5. | A Windows Security dialog will appear as seen in Figure 11. By choosing the Add
option, the existing inherited permissions will be copied to the
permissions list for the folder or file. Use this option if you want to
simply modify the existing permissions that were being inherited from
the parent. By choosing the Remove option, the existing permissions will be removed from the object and you will need to add new permissions to the object.
|
You may also find yourself needing to force permission inheritance on all objects within a folder. Selecting the option Replace all child object permissions with inheritable permissions from this object
will force all files and subfolders to inherit permissions from the
current folder. This is a great way to quickly reset all permissions of
child objects to match the parent.
Access-based enumeration
Starting with Windows
Server 2003, Microsoft made it possible to prevent users from seeing
files they do not have access to. Prior to that, all files in a
shared folder were visible to a user even if he did not have access to
them. Access-based enumeration (ABE) allows a user to see only the files
he or she has access to. For example, an administrator may create a new
shared folder giving members of the accounting group modify access. The
accounting manager may create a new excel spreadsheet and save it in
this shared folder. She may then restrict access to this file to
herself. If ABE is turned on, all the other members of the accounting
group will not be able to see the file, since they do not have access.
ABE can be turned on per shared folder. To turn on ABE, perform the
following:
1. | Open Server Manager.
|
2. | Expand the nodes Roles | File Services.
|
3. | Select the Share and Storage Management node.
|
4. | In the middle pane, double-click the shared folder that you want to enable ABE on opening the shared folder properties window.
|
5. | Click the Advanced button in the properties window.
|
6. | Select the option to Enable ABE and then click OK. |