Internet Explorer includes several advanced settings
that you can manipulate to control how IE functions. These settings are
located in the Advanced tab of the Internet Options screen.
The Security category is the most important section on the Advanced tab. Figure 1 shows the Advanced tab with the Security section showing.
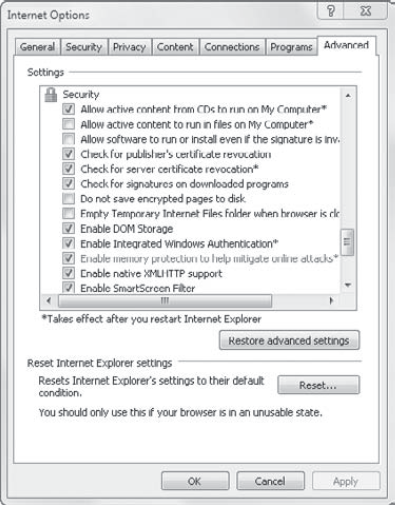
Several categories of settings exist on the Advanced tab:
- Accessibility
These settings can be manipulated to make the web pages user friendly for people with disabilities.
- Browsing
These settings can be
modified to affect how pages are displayed. This category also includes
settings for some new features such as Suggested Sites and the
Accelerator button.
- HTTP 1.1 Settings
These setting are used to indicate that HTTP 1.1 will be used over HTTP 1.0. HTTP 1.1 was widely adopted in 1996.
- International
These settings allow you to
manipulate how internationalized domain names (IDNs) are used. IDNs can
be used to support different character sets. You can also use the
Unicode Transformation Format - 8 (UTF-8) display set.
- Multimedia
These settings allow
you to manipulate how multimedia elements such as pictures, animations,
and sounds are treated. You can enable or disable any of the elements.
- Printing
Only a single setting is included here. It allows you to choose to print background colors and images.
- Search From The Address Bar
This controls what information is sent to the search provider and how the results are displayed.
- Security
This is the one of the most
important sections from an enterprise administrator's perspective. You
can control many of the important security settings from this screen.
Several of these settings are explored in more depth in the following
sections.
1. Certificate Settings
The Security tab
includes several settings related to certificates. Before covering these
settings, it's worthwhile understanding how certificates are used with
IE.
Certificates are used on the Internet to establish secure sessions using HTTPS. Consider Figure 2.
A client starts an HTTPS session by clicking a link. The web server
then returns a certificate that includes a public key. The public key is
matched to a private key on the web server. The client and the web
server use the public/private keys to establish a secure SSL session.
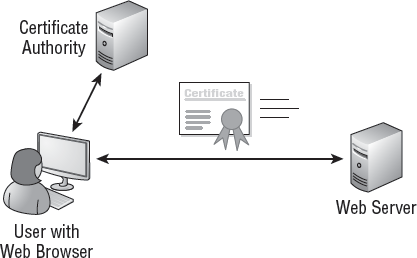
However, there's more to the
story. The client makes several checks to ensure that the certificate
passed from the web server is to be trusted.
The first check ensures that
the certificate that was sent matches the server that sent it.
Certificates are issued to specific servers. If someone tries to use the
certificate on another server, this check will fail and the user will
see an error.
The next check ensures
that the certificate from the web server was issued from a CA in the
Trusted Root Certification Authorities store. Most e-commerce websites
purchase certificates from well-known CAs. These CAs have agreements
with Microsoft to place the certificates in the Trusted Root
Certification Authorities store.
You can view the Trusted Root Certification Authorities store by clicking Tools =>
Internet Options, selecting the Content tab, clicking Certificates, and
selecting Trusted Root Certification Authorities store. If the web
server purchased a certificate from one of these CAs, the check will not
return an error.
On the other hand, if the web
server uses a certificate that was created from a CA that is not in the
Trusted Root Certification Authorities store, the user will see an
error. The error indicates that the certificate is not trusted and
encourages the user to not continue.
The second check is to
ensure that the certificate is still valid. Certificates expire, but
sometimes the certificate becomes compromised and the CA will revoke it.
Every certificate has a serial number, and this serial number uniquely
identifies it. When a CA revokes a certificate, it publishes the serial
number on a Certificate Revocation List (CRL, pronounced "crill").
There are two ways a certificate is checked to see if it's been revoked:
- Check the CRL
The client can request a
copy of the CRL. The client then checks to see if the serial number of
the certificate is on the CRL. If it is, it's been revoked and the
client receives an error encouraging the client not to use it.
- Use OCSP
The Online Certificate
Status Protocol (OCSP) can also be used to check the certificate. The
client uses OCSP to send the serial number of the certificate to the CA.
The CA then answers by indicating the certificate is healthy, not
healthy (revoked), or unknown (indicating it's an invalid serial
number).
There are two ways to verify
that you have a secure connection. HTTPS (instead of just HTTP) shows in
the address bar, and a lock icon appears at the end of the address bar.
You can view the web server's certificate anytime you have established a secure connection using one of two methods. Figure 3 shows what appears if you click the lock icon. You can click the View Certificates link to view the certificate.
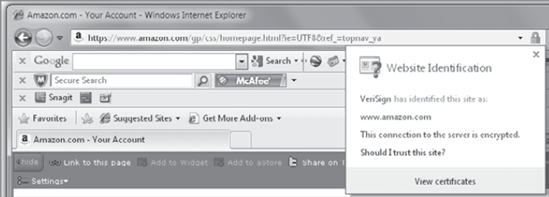
|
If the
certificate isn't valid, the Website Identification section will appear
with a warning, and the address bar will have a red background.
|
|
You can also select Page =>
Properties and click the Certificates button. Whether you click the
Certificates button from the Page Properties screen or click the View
Certificates link from the lock icon, you'll see the same certificate
details as shown in Figure 4.
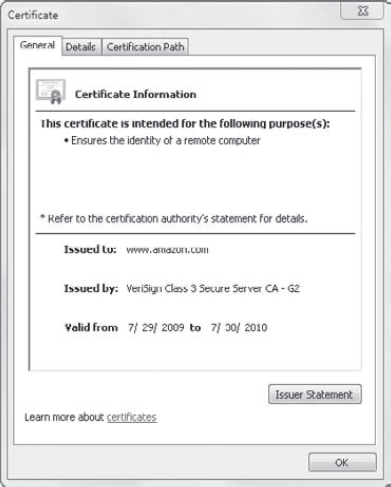
With this background
information, the certificate-related settings in the Advanced tab are
easier to explain. The following certificate settings are available:
- Check For Publisher's Certificate Revocation
When this is checked, the CA's certificate is examined to see if it has been revoked. This setting is checked by default.
- Check For Server Certificate Revocation
When this is checked,
IE examines the certificate from the web server to see if it has been
revoked. This setting is checked by default.
- Use SSL 2.0 and Use SSL 3.0
SSL is used to establish HTTPS sessions. Both SSL 2.0 and SSL 3.0 are supported in IE 8. This setting is checked by default.
- Warn About Certificate Mismatch
If the certificate
presented by the server doesn't match the server, this setting will
ensure that an error is presented to the user. This sometimes occurs
when the website operator changes the name of the server. This setting
is checked by default.
- Check For Signatures On Downloaded Programs
When this is checked, IE checks signatures for any programs that have been downloaded. This setting is checked by default.
- Allow Software To Run Or Install Even If The Signature Is Invalid
When this is unchecked,
software with invalid signatures will not be installed. This is useful
because malware will either not be signed or not have a valid signature.
This setting is not checked by default.
2. Active Content
The Security tab includes
two settings related to active content. Active content is content that
includes scripts or ActiveX controls. Although active content can be
useful, it can also contain malware.
By default, the following two settings are unchecked. This prevents active content from running from within IE.