Windows Firewall
One of the major
complaints on Windows operating system security has always been the
issue of a built-in firewall. With Windows XP Service Pack 1, a limited
firewall was first implemented. Windows Vista now provides a more
complete security configuration in the included firewall by allowing for
control of outbound connection requests as well as inbound connection
attempts.
Configuring the Windows
Vista Firewall begins with the firewall profile selected when you set
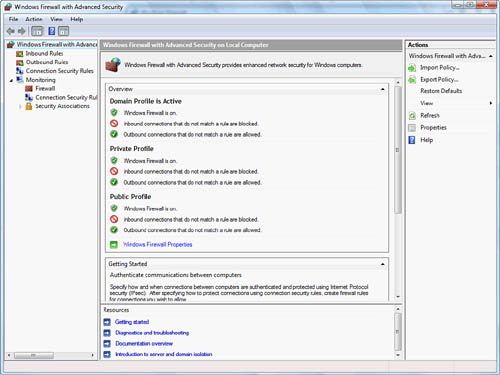
up the network location type. Figure 3 shows the three firewall profiles described earlier in
the discussion of network profiles.
Configuring firewall
settings within the Windows Firewall with Advanced Security console
involves setting granular controls for specific protocols and for
inbound and outbound directions. You can access Windows Firewall with
Advanced Security by clicking Start > Administrative Tools > Windows
Firewall with Advanced Security.
Initially,
you should configure the firewall profiles first to satisfy how Windows
Firewall will function when a network location type is selected for any
new connection. To access the properties of the firewall profiles,
select the top node in the MMC on the left labeled Windows Firewall with
Advanced Security on Local Computer. Right-click this item and select
the Properties option from the menu. Figure 4 shows what is displayed after you follow these
steps.
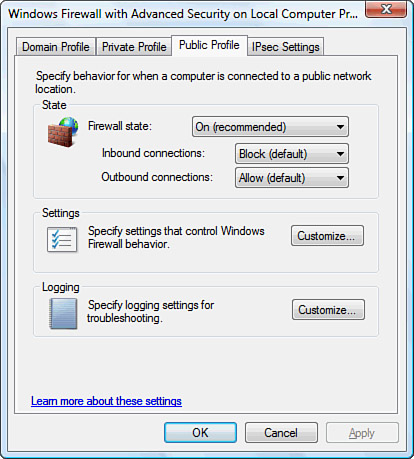
For each of the firewall profiles, you are
able to configure the characteristics of the firewall state, Inbound and
Outbound firewall functionality, settings that control notifications,
Unicast response, whether rules are merged, and logging of firewall
traffic for troubleshooting.
The firewall state refers
to whether Windows Firewall is set to On for that particular firewall
profile.
Inbound and Outbound
connection settings can be configured to one of three settings:
Block— Blocks all connections that do not have firewall
rules that explicitly allow the connection.
Block All Connections— Blocks all connections even if there is an explicit
firewall rule that allows a connection. This applies to only inbound
connections.
Allow— Allows all connections unless there is a firewall
rule that explicitly blocks a particular connection.
There is a
notification setting available when you customize the settings of a
firewall profile. The notification settings determine whether a
notification is sent to the local user if a program is blocked from
receiving an inbound connection. The default setting for this is Yes.
A Unicast response setting
determines whether a unicast response may be sent for multicast or
broadcast traffic. This setting can help certain types of malicious
attacks where multicast or broadcast traffic from a bad guy is used to
illicit traffic, such as ICMP responses or requests from the local
computer.
Rule merging settings are
managed through Group Policy, but their outcome is displayed here. These
settings determine whether the local firewall rules and local
connection security rules merge with Group Policy settings that are
applied to the local computer.
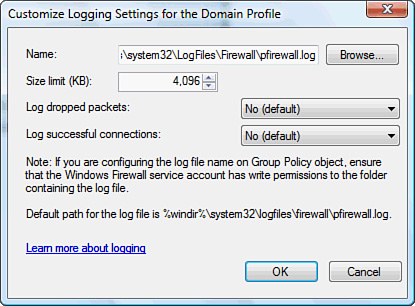
The settings for
Logging configuration for the Windows Firewall allow the local
administrator to log packets that are dropped as well as log successful
connections.
Alert
Note
that the name of the log file created by default for Windows Firewall
logging is pfirewall.log. Because the
firewall policy can be set to block outgoing as well as incoming
connections, when logging dropped packets, you are able to log packets
that are dropped by the local firewall when attempting an outbound
connection as well. This capability aids in troubleshooting granular
configuration of outbound rules that permit a particular protocol for an
application. By reviewing the log when an application fails to make an
outbound connection, you are then able to determine if all ports
outbound as well as inbound for an application are configured
appropriately.
Figure 5 shows configuration of the logging
settings for Windows Firewall.
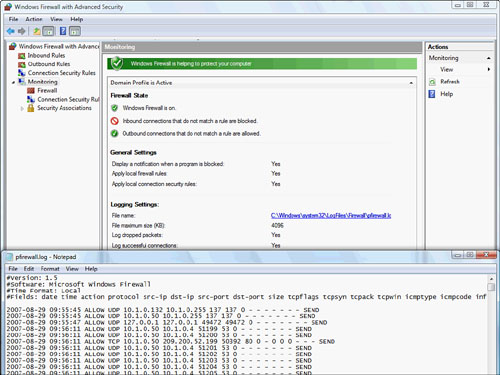
To view the contents of the
log when it is in use, you can select the Monitoring node in the console screen of Windows Firewall
with Advanced Security. In the right pane, you see a hyperlink to the
log in use. Figure 6 shows how to access this log and view
its contents.
Alternatively, you can use
Windows Explorer to access the firewall log found by default at C:\Windows\system32\Logfiles\Firewall\pfirewall.log. The log file must be stored in a directory where the
Windows Firewall service account has Write permissions. Failure to
ensure this permission assignment to that account prohibits the firewall
service from logging to the pfirewall.log file.
Caution
Why Isn’t Anything
Logged? The Windows Firewall
service account is known more affectionately as NT Service\MpsSvc.
When you are creating a custom location for this log file, ensure that
the account NT Service\MpsSvc is assigned the Write NTFS permission to
the folder where the log file is located. Support article 929455
describes this issue when the permission assignment has not been made
and discusses the corresponding resolution.