Windows Defender is a tool designed to
reduce the risk of specific types of malware for small office and home
users. Though Windows Defender is not designed for use in large
enterprises, it does provide some integration with Active Directory
Group Policy and can retrieve updates from an internal Windows Software
Update Services (WSUS) server.
Windows Defender will interact with users if
potentially unwanted software is detected Therefore, users must be
trained before Windows Defender is deployed so that they understand how
to respond to the various prompts and can distinguish between genuine
Windows Defender prompts and other software that might impersonate those
prompts (a common social engineering technique).
1. Understanding Windows Defender
Windows Defender provides two types of protection, both enabled by default:
Automatic scanning
Windows Defender scans the computer for potentially malicious software
on a regular basis. By default, Windows Defender is configured to
download updated definitions and then do a quick scan daily at 2 A.M.
You can configure scanning frequency on the Windows Defender Options
page.
Real-time protection
Windows Defender constantly monitors computer usage to notify you if
potentially unwanted software might be attempting to make changes to
your computer.
The sections that follow describe each type of protection in more detail.
Automatic Scanning
Windows Defender provides two different types of scanning:
Quick Scan
Scans the portions of a computer most likely to be infected by malware,
such as the computer’s memory and portions of the registry that link to
startup applications. This is sufficient to detect most malware
applications.
Full Scan
Scans every file on the computer, including common types of file
archives as well as applications already loaded in the computer’s
memory. A full scan typically takes several hours, but it may take more
than a day, depending on the speed of the computer and the number of
files to be scanned. The user can continue to work on the computer
during a quick scan or a full scan; however, these scans do slow the
computer down, and will consume battery power on mobile computers very
quickly.
By default, Windows Defender runs a quick scan
daily. This is usually sufficient. If you think a user might have
malware installed, you should run a full scan to increase the chances of
removing every trace of the malware. In addition to quick scans and
full scans, you can configure a custom scan to scan specific portions of
a computer. Custom scans always begin with a quick scan.
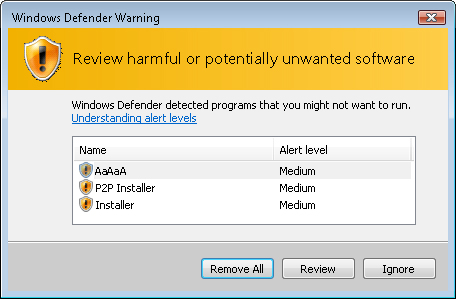
If Windows Defender finds potentially unwanted software, it will display a warning, as shown in Figure 1.

Most
of the time, the user should simply choose to remove all of the
potentially unwanted software. However, Windows Vista will display four
options for each item detected:
Ignore
Allows the software to be installed or run on your computer. If the
software is still running during the next scan, or if the software tries
to change security-related settings on your computer, Windows Defender
will alert you about this software again.
Quarantine
When Windows Defender quarantines software, it moves it to another
location on your computer, and then prevents the software from running
until you choose to restore it or remove it from your computer.
Remove Deletes the software from your computer.
Always Allow
Adds the software to the Windows Defender allowed list and allows it to
run on your computer. Windows Defender will stop alerting you to
actions taken by the program. Add software to the allowed list only if
you trust the software and the software publisher.
Real-Time Protection
Real-time protection might alert you when software attempts to install itself or run on your computer, as shown in Figure 2.
Depending on the alert level, users can choose to remove, quarantine,
ignore, or always allow the application, just as if the problem were
encountered during a scan.
If potentially unwanted software is allowed to
run on your computer, it sometimes attempts to make changes to system
settings so that it will automatically run the next time you start your
computer. Of course, legitimate software also makes similar changes, so
it’s up to the user to determine whether the change should be allowed.
If Windows Defender real-time protection detects software attempting to
make a change to important Windows Settings, the user will be prompted
to Permit (allow the change) or Deny (block the change).
Real-time protection provides the following security agents, all of which are enabled by default:
Auto Start
Monitors lists of programs that are allowed to automatically run when
you start your computer. Malware typically wants to run after you
restart your computer, and frequently adds itself to one of the several
lists of autostart programs.
System Configuration (Settings)
Monitors security-related settings in Windows. Malware often attempts
to disable security software to make it more difficult for users to
detect or remove the malware and to allow other applications to install
without the user’s permission.
Internet Explorer Add-ons
Monitors programs that automatically run when you start Internet
Explorer. Malware can masquerade as web browser add-ons and run without
the user’s knowledge.
Internet Explorer Configurations (Settings)
Monitors browser security settings, which are your first line of
defense against unwanted content on the Internet. Malware can try to
change these settings without the user’s knowledge to make it easier to
make browser configuration changes.
Internet Explorer Downloads
Monitors files and programs that are designed to work with Internet
Explorer, such as ActiveX controls and software-installation programs.
These files can be downloaded, installed, or run by the browser itself.
Unwanted software is often included with these files and installed
without the user’s knowledge.
Services and Drivers Monitors
services and drivers as they interact with Windows Vista and
applications. Malware often attempts to use services and drivers to gain
access to protected areas of the operating system.
Application Execution
Monitors when programs start and any operations they perform while
running. Malware can use vulnerabilities in previously installed
applications to run unwanted software without the user’s knowledge. For
example, spyware can run itself in the background when a user starts
another frequently used application. Windows Defender monitors
applications and alerts the user if suspicious activity is detected.
Application Registration
Monitors tools and files in the operating system where applications can
register to run at any time, not just when you start Windows Vista or
another program. Malware can register a program to start without notice
and run at a scheduled time each day, for example. This allows the
program to collect information about the user or gain access to
important software in the operating system without the user’s knowledge.
Windows Add-ons
Monitors add-on programs (also known as software utilities) for Windows
Vista. Add-ons are designed to enhance your computing experience in
areas such as security, browsing, productivity, and multimedia. However,
add-ons can also install programs that will collect information about
users and expose sensitive, personal information, often to advertisers.