4. Task Scheduler Security
In
the Windows Vista Task Scheduler, security is vastly improved. Task
Scheduler supports a security isolation model in which each set of tasks
running in a specific security context starts in a separate session.
Tasks executed for different users are launched in separate window
sessions, in complete isolation from one other and from tasks running in
the machine (system) context. Passwords are stored (when needed) with
the Credentials Manager (CredMan) service. Using CredMan prevents
malware from retrieving the stored password, tightening security
further.
In Windows Vista, the burden of credentials
management in Task Scheduler is lessened. Credentials are no longer
stored locally for the majority of scenarios, so tasks do not “break”
when a password changes. Administrators can configure security services
such as S4U and CredMan, depending on whether the task requires remote
or local resources. S4U relieves the need to store passwords locally on
the computer, and CredMan, though it requires that passwords be updated
once per computer, automatically updates all scheduled tasks configured
to run for the specific user with the new password.
Credentials Management
The Credentials Manager stores the
target/credentials pair locally in the user profile CredMan store. Upon
registration, Task Scheduler impersonates the user and stores the
target/credentials pair. This process is also used to access resources
that require non-Windows credentials. The Credentials Manager also
manages credentials for service accounts and extends credentials
handling for computer accounts.
User Security
You can locally and remotely activate tasks and
run them on behalf of a user who is not logged on. Credentials on
distributed tasks can be updated when credentials are changed in the
authentication authority. User security has been extended to function in
a non-Microsoft Active Directory environment across forests and across
firewalls. These features allow tasks to be launched even if the task
accesses a resource that requires non-Windows credentials.
Security Concepts
Task Scheduler uses standard Windows security
functions provided by Service for Users (S4U). Upon registration, Task
Scheduler authenticates credentials as a trusted service and stores
identity only in a domain\user name format. Upon execution, S4U provides
restricted token access based on the identity provided by Task
Scheduler. S4U2Self implements the same functions as S4U for workgroups,
stand-alone computers, and computers that belong to a domain but are
not currently connected to that domain.
Securing Running Tasks
Task Scheduler supports an isolation model in
which each set of tasks running in specific security context are
launched in separate Desktops. The execution defined and launched by the
trigger is handled by engines running in transient processes in a user
or computer context. Tasks can be launched in a system account context,
such as LocalSystem, LocalService, or NetworkService, or in a specified
user account context. Tasks launched in a system account context will
always run non-interactively in Session 0.
The CreateProcess
function used to create tasks ensures that any Winstation created in a
user context will run in a different session than Session 0. By default,
all Winstations will be created in the same session.
Registration Permissions Matrix
The Task Scheduler service adheres to the following task registration permissions rules:
- Any user can schedule any task for himself or herself.
- Any user can schedule any task for anyone whose password they supply at registration.
- An
administrator or system account can schedule tasks for other users or
security groups without supplying a password, with the following
restrictions:
- Only with the Run Only If Logged On flag set, which is similar to a logon script and consistent with current behavior
- Only running in interactive mode
- Tasks scheduled with RunOnlyIfUserLoggedon with no password will run only in interactive mode.
- Tasks scheduled to run in system contexts such as LocalSystem, LocalService, or NetworkService will not run in interactive mode.
5. AT and Task Scheduler v1.0 Compatibility Modes
Task Scheduler provides two backward-compatibility modes:
AT Compatibility Mode
Tasks registered through AT.exe are visible and can be modified by the
Task Scheduler v1.0 GUI and the Task Scheduler command-line utility
SchTasks.exe.
Task Scheduler v1.0 Compatibility Mode Tasks
created or modified in the Task Scheduler v1.0 user interface and the
Task Scheduler command-line utility SchTasks.exe are not accessible or visible through At.exe.
The Task Scheduler parser will determine at
registration time whether the task can be converted to either of these
compatibility modes.
6. Task Scheduler User Interface
The Task Scheduler user interface is now an MMC 3.0 snap-in, as shown in Figure 2.
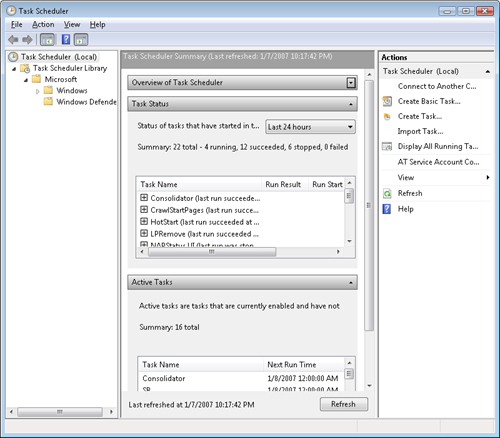
The scope pane on the left contains the
Scheduled Tasks Library sub-node under the root Task Scheduler node by
default. The Library sub-node has all currently defined tasks listed
under it, in a hierarchy of folders. The Microsoft subnode under the
Scheduled Tasks Library contains a Windows subnode with default Windows
system tasks used by operating system components, such as Reliability
Monitor (RAC) and System Restore. Default system tasks are normally not
modified.
The Results Pane in the center shows the task
name and other relevant information about the currently selected task.
The bottom part of the center pane contains a preview pane showing the
definition details of the currently selected task in the list at top.
Task definitions may be modified by either double-clicking the task name
in the list, or selecting and right clicking or clicking the Properties
action in the Actions Pane at right.
The
Actions Pane on the right shows relevant actions for a selected task or
scope node. New tasks can be created using the Create Basic Task action
for wizard-based simple tasks, or using Create Task for full-featured
tasks.
The Summary (home) page that shows up
whenever you start Task Scheduler and have the top node selected
displays a summary of task status for the system that includes how many
tasks ran, how many succeeded or failed, and a list of currently active
tasks that are not disabled or expired.