Most administrators know that users should
log on to their computers using accounts that are members of the Users
group, but not the Administrators group. By limiting your user account’s
privileges, you also limit the privileges of any applications that you
start—including software installed without full consent. Therefore, if
you can’t add a startup application, neither can a malicious process
that you accidentally launch.
With earlier versions of Windows, however, not
being a member of the Administrators group could be very difficult, for a
few reasons:
Many applications would only run with administrative privileges.
Running
applications with elevated privileges required users to either
right-click the icon and then click Run As or create a custom shortcut,
which is inconvenient, requires training, and requires that the user
have a local administrator account (largely defeating the purpose of
limiting privileges).
Many common operating system tasks, such as changing the time zone or adding a printer, required administrative privileges.
UAC is a feature of Windows Vista that improves
client security by making it much easier to use accounts without
administrative privileges. At a high level, UAC offers the following
benefits:
Most applications can now run without administrative privileges
Applications created for Windows Vista should be designed to not
require administrative credentials. Additionally, UAC virtualizes
commonly accessed file and registry locations to provide backward
compatibility for applications created for earlier versions of Windows
that still require administrative credentials. For example, if an
application attempts to write to a protected portion of the registry
that will affect the entire computer, UAC virtualization will redirect
the write attempt to a non-protected area of the user registry that will
only affect that single application.
Applications that require administrative privileges automatically prompt the user for administrative credentials
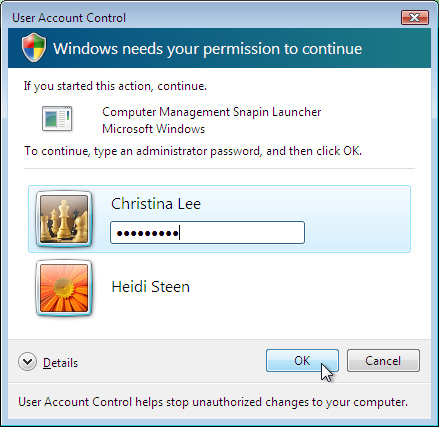
For example, if a standard user attempts to open the Computer
Management console, a User Account Control dialog box appears and
prompts for administrative credentials, as shown in Figure 1.
If the current account has administrative credentials, the dialog box
prompts to confirm the action before granting the process administrative
privileges.
Users no longer require administrative privileges for common tasks Windows
Vista has been improved so that users can make common types of
configuration changes without administrative credentials. For example,
in earlier versions of Windows, users needed administrative credentials
to change the time zone. In Windows Vista, any user can change the time
zone, which is important for users who travel. Changing the system time,
which has the potential to be malicious, still requires administrative
credentials, however.
Operating system components display an icon when administrative credentials are required
In earlier versions of Windows, users were often surprised when an
aspect of the operating system required more privileges than they had.
For example, users might attempt to adjust the date and time, only to
receive a dialog informing them that they lack necessary privileges. In
Windows Vista, any user can open the Date And Time properties dialog
box. However, users need to click a button to change the time (which
requires administrative privileges), and that button has a shield icon
indicating that administrative privileges are required. Users will come
to recognize this visual cue and not be surprised when they are prompted
for credentials.
If
you log on with administrative privileges, Windows Vista will still run
applications using standard user privileges by default Most
Windows Vista users should log on with only standard user credentials.
If users do log on with an account that has Administrator privileges,
however, UAC will still launch all processes with only User privileges.
Before a process can gain Administrator privileges, the user must
confirm the additional rights using a UAC prompt.
Table 1 illustrates the key differences in the behavior of Windows Vista with UAC installed when compared to Windows XP.
Table 1. Behavior Changes in Windows Vista with UAC
| Windows XP | Windows Vista with UAC |
|---|
| When
logged on as a standard user, administrators could run administrative
tools by right-clicking the tool’s icon, clicking Run As, and then
providing administrative credentials. | Standard
users open administrative tools without right-clicking. UAC then
prompts the user for administrative credentials. All users can still
explicitly launch an application with administrative credentials by
right-clicking, but it is rarely necessary. |
| Using a standard user account could be a nuisance, especially for technical or mobile users. | The
same number of security prompts are required for standard and
administrative accounts, and standard accounts can perform many tasks
that previously required elevation. |
| When
a user was logged on as a standard user, an application that needed to
change a file or setting in a protected location would fail. | When
a user is logged on as a standard user, UAC provides virtualization for
important parts of the system, allowing the application to run
successfully while protecting the operating system integrity. Some
applications may still fail, however. |
| If a specific Windows feature required administrative privileges, the entire tool required administrative privileges. | Windows Vista displays the UAC shield on buttons to warn users that the feature requires elevated privileges. |
| When a user was logged on as an administrator, all applications ran with administrative privileges. | When
a user is logged on as an administrator, all applications run with
standard user privileges. UAC confirms elevated privileges before
launching a tool that requires administrative privileges. |
The sections that follow describe UAC behavior in more detail.
1. UAC for Standard Users
Microsoft made many changes to the operating
system so that standard users could perform almost any day-to-day task.
Tasks standard users can do without receiving a UAC prompt that required
administrative privileges in Windows XP include:
- View the system clock and calendar
- Change the time zone
- Connect to wired or wireless networks
- Connect to virtual private networks (VPNs)
- Change display settings and the desktop background
- Change their own passwords
- Install critical Windows Updates
- Add printers and other devices that have the required
drivers installed on computer or have been allowed by an administrator
in Group Policy
- Install ActiveX Controls from sites approved by an administrator
- Play or burn CDs and DVDs (configurable with Group Policy settings)
- Connect to another computer with Remote Desktop
- Configure battery power options on mobile computers
- Configure accessibility settings
- Configure and use synchronization with a mobile device
- Connect and configure a Bluetooth device
- Restore backed-up files from the same user
Additionally, disk defragmentation is scheduled
to automatically happen in the background, so users do not need
privileges to manually initiate a defragmentation.
Some of the common tasks standard users cannot do include:
- Install and uninstall applications
- Install device drivers
- Install non-critical Windows Updates
- Install ActiveX controls from sites not approved by an administrator
Note
To install ActiveX
controls in Internet Explorer, launch Internet Explorer by
right-clicking the icon and then clicking Run As Administrator. After
installing the ActiveX control, close Internet Explorer and reopen it
using standard privileges. Once installed, the ActiveX control will be
available to standard users. |
- Change Windows Firewall settings, including enabling exceptions
- Configure Remote Desktop access
- Create scheduled tasks
- Restore system files from a backup
The Power Users group still exists in Windows
Vista. However, Windows Vista removes the elevated privileges.
Therefore, you should make users a member of the Users group and not use
the Power Users group at all. To use the Power Users group on Windows
Vista, you must change the default permissions on system folders and the
registry to grant Power Users group permissions equivalent to Windows
XP.
2. UAC for Administrators
UAC uses Admin Approval Mode to help protect
administrators from malicious and potentially unwanted software. When an
administrator logs on, Windows Vista generates two access tokens:
Standard user access token
This token is used to launch the desktop (Explorer.exe). Because the
desktop is the parent process for all user-initiated processes, any
applications the user launches also use the standard user access token,
which does not have privileges to install software or make important
system changes.
Full administrator access token This token has almost unlimited privileges to the local computer. This token is used only after the user confirms a UAC prompt.
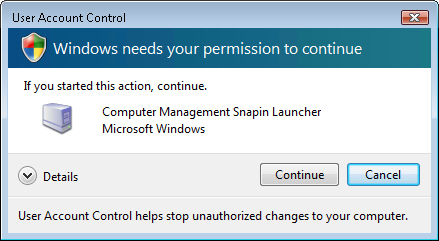
If
the administrator attempts to launch an application that requires
administrative rights (as identified in the application’s manifest,
described later), UAC prompts the administrator to grant additional
rights using the consent prompt, as shown in Figure 2.
If the user chooses to grant elevated privileges to an application, the
Application Information service creates the new process using the full
administrator access token. The elevated privileges will also apply to
any child processes that the application launches. Parent and child
processes must have the same integrity level.
Note
The Application Information service must be running to launch processes with elevated privileges. |
Command prompts require special consideration,
because UAC will not prompt you to elevate privileges if you attempt to
run a command that requires administrative rights. To run a command with
administrative rights, right-click Command Prompt on the Start menu,
and then click Run As Administrator. The command prompt that opens will
include Administrator: in the title, helping you identify the window on
your taskbar.
Admin Approval Mode does not apply to
the built-in Administrator account. To protect this account from attack,
the built-in Administrator account is disabled by default.