8. How to Configure User Account Control
You
can use Group Policy settings to granularly configure UAC behavior.
Additionally, you can disable UAC by using the Control Panel,
msconfig.exe, or by directly editing registry settings. The sections
that follow describe each of these techniques in more detail.
Group Policy settings
You can configure UAC using local or Active Directory Group Policy settings located in the following node:
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options
You can configure the following settings:
User Account Control: Admin Approval Mode for the Built-in Administrator account
This policy applies only to the built-in Administrator account, and not
to other accounts that are members of the local Administrators group.
When you enable this policy setting, the built-in Administrator account
has UAC Admin Approval Mode enabled, just like other administrative
accounts. When you disable the setting, the built-in Administrator
account behaves just like it did in Windows XP, and all processes run
using Administrator privileges. This setting is disabled by default.
Note
To minimize the risk
of abusing the built-in Administrator account, the account is disabled
by default. If Windows Vista determines during an upgrade from Windows
XP that the built-in Administrator is the only active local
administrator account, Windows Vista leaves the account enabled and
places the account in Admin Approval Mode. The built-in Administrator
account, by default, cannot log on to the computer in safe mode. If the
last local administrator account is inadvertently demoted, disabled, or
deleted, safe mode will allow the disabled built-in Administrator
account to log on for disaster recovery. |
User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode
By default, this setting is set to Prompt For Consent, which causes the
UAC prompt to appear any time a process needs more than standard User
privileges. Change this setting to Prompt For Consent to cause Admin
Approval Mode UAC prompts to behave like prompts for standard users,
requiring the user to type an administrative password instead of simply
clicking Continue. Change this setting to Elevate Without Prompting to
automatically provide administrative privileges, effectively disabling
UAC for administrative accounts. Choosing Elevate Without Prompting
significantly reduces the security protection provided by Windows Vista,
and might allow malicious software to install itself or make changes to
the system without the administrator’s knowledge.
User Account Control: Behavior of the elevation prompt for standard users
By default, this setting is Prompt For Credentials in workgroup
environments and Automatically Deny Elevation Requests in domain
environments. Prompt For Credentials causes UAC to prompt the user to
enter an administrative user name and password. You can change this to
Automatically Deny Elevation Requests to disable the UAC prompt.
Disabling the prompt can improve security; however, the user might
experience application failures because of denied privileges. If users
do not have access to administrative credentials, you should disable the
elevation prompt, because the user would not be able to provide
credentials anyway. If you do not disable the prompt, users are likely
to call the support center to ask for administrative credentials.
User Account Control: Detect application installations and prompt for elevation
By default, this setting is enabled in workgroup environments and
disabled in domain environments. When enabled, UAC will prompt for
administrative credentials when the user attempts to install an
application that makes changes to protected aspects of the system. When
disabled, the prompt won’t appear. Domain environments that use
delegated installation technologies such as Group Policy Software
Install (GPSI) or SMS can safely disable this feature because
installation processes can automatically escalate privileges without
user intervention.
User Account Control: Only elevate executables that are signed and validated
If your environment requires all applications to be signed and
validated with a trusted certificate, including internally developed
applications, you can enable this policy to greatly increase security in
your organization. When this policy is enabled, Windows Vista will
refuse to run any executable that isn’t signed with a trusted
certificate, such as a certificate generated by an internal Public Key
Infrastructure (PKI). All software with the Certified For Windows Vista
logo must be signed with an Authenticode certificate, though you might
have to configure your domain PKI to trust the certificate. This setting
is disabled by default, which allows users to run any executable,
including potentially malicious software.
User Account Control: Only elevate UIAccess applications that are installed in secure locations
This setting, which is enabled by default, causes Windows Vista to
grant user interface access (required for opening windows and doing
almost anything useful) to only those applications launched from Program
Files, from \Windows\System32\, or from a subdirectory. Enabling this
setting effectively prevents non-administrators from downloading and
running an application, because non-administrators won’t have the
privileges necessary to copy an executable file to one of those folders.
User Account Control: Run all administrators in Admin Approval Mode This setting, enabled by default, causes all accounts with administrator privileges except
for the local Administrator account to use Admin Approval Mode. If you
disable this setting, Admin Approval Mode is disabled for administrative
accounts, and the Security Center will display a warning message.
User Account Control: Switch to the secure desktop when prompting for elevation
This setting, enabled by default, causes the screen to darken when a
UAC prompt appears. If the appearance of the entire desktop changes, it
is very difficult for malware that hasn’t been previously installed to
impersonate a UAC prompt. Some users might find the secure desktop
annoying, and you can disable this setting to minimize that annoyance.
However, disabling this setting decreases security by making it possible
for other applications to impersonate a UAC prompt.
User Account Control: Virtualize file and registry write failures to per-user locations
This setting, enabled by default, improves compatibility with
applications not developed for UAC by redirecting requests for protected
resources.
To disable UAC, set the User Account Control:
Behavior Of The Elevation Prompt For Administrator In Admin Approval
Mode setting to No Prompt. Then, disable the User Account Control:
Detect Application Installations And Prompt For Elevation and User
Account Control: Run All Administrators In Admin Approval Mode settings.
Finally, set User Account Control: Behavior Of The Elevation Prompt For
Standard Users setting to Automatically Deny Elevation Requests.
Additionally, you can configure the credential
user interface using the following two Group Policy settings located at
Computer Configuration\Administrative Templates\Windows
Components\Credential User Interface:
Require Trusted Path For Credential Entry
If you enable this setting, Windows Vista requires the user to enter
credentials using a trusted path, which requires the user to press
Ctrl+Alt+Delete. This helps prevent a Trojan horse program or other
types of malicious code from stealing the user’s Windows credentials.
This policy affects non-logon authentication tasks only. As a security
best practice, you should enable this policy to reduce the risk of
malware tricking the user into typing her password. However, users who
need elevated privileges regularly will find it annoying and
time-consuming. Figures 8, 9, and 10 show the dialog boxes that appear each time a user must elevate privileges when this setting is enabled.
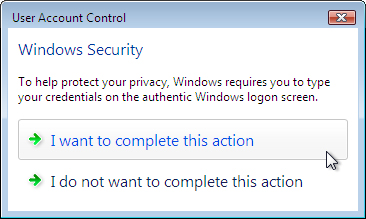
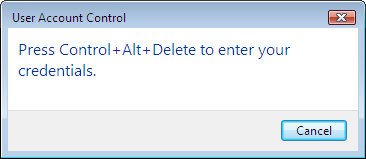
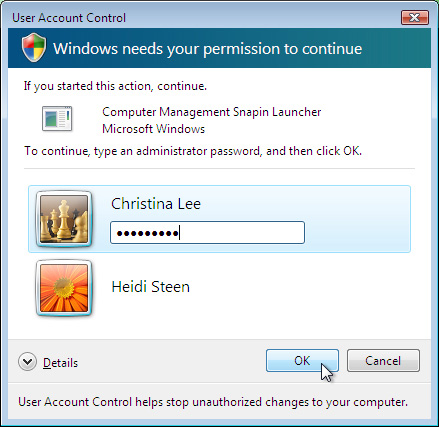
Enumerate Administrator Accounts On Elevation By
default, this setting is disabled, which causes the UAC prompt to list
all administrator accounts displayed when a users attempts to elevate a
running application. If you enable this setting, users are required to
type both a user name and password to elevate their privileges.
Control Panel
Group Policy is the best way to configure UAC
in Active Directory environments. In workgroup environments, you can
disable UAC on a single computer by using Control Panel:
1. | In Control Panel, click User Accounts And Family Safety.
|
2. | Click User Accounts.
|
3. | Click Turn User Account Control On Or Off.
Note Though the link appears on a single user’s Control Panel page, it will affect all users. |
|
4. | Clear the Use User Account Control (UAC) To Help Protect Your Computer check box, and then click OK.
|
5. | When prompted, restart your computer.
|
To re-enable UAC, repeat these steps and select the Use User Account Control (UAC) To Help Protect Your Computer check box.
Msconfig.exe
Msconfig.exe is a troubleshooting tool that can
be useful for temporarily disabling UAC to determine whether UAC is
causing an application compatibility problem. To make the change,
msonfig.exe simply modifies the registry value. To disable UAC with
msconfig.exe, follow these steps:
1. | Click Start, type msconfig and then press Enter.
The System Configuration tool opens.
|
2. | Click the Tools tab.
|
3. | Click Disable UAC, and then click Launch.
|
4. | A
command window appears, and shortly thereafter, a notification bubble
appears informing you that UAC is disabled. Restart your computer to
apply the change.
|
To re-enable UAC with msconfig.exe, follow the preceding steps, clicking Enable UAC instead of Disable UAC.
Registry
To disable UAC using the registry, change the following registry value to 0:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\EnableLUA
Note
During the early Windows Vista beta period, UAC was known as Limited User Account or Limited User Access (LUA). |
To re-enable UAC, change that registry value to 1. Restart the computer to apply the change.
9. How to Configure Auditing for Privilege Elevation
You
can enable auditing for privilege elevation so that every time a user
provide administrative credentials or an administrators clicks Continue
at a UAC prompt, an event is added to the Security event log. To enable
privilege elevation auditing, enable success auditing for both the Audit
Process Tracking and Audit Privilege Use settings in the Local
Policies\Audit Policy node of Group Policy. Note that you should only
enable auditing when testing applications or troubleshooting problems;
enabling these types of auditing can generate an excessive number of
events and negatively affect computer performance.
To enable auditing on a single computer, use the
Local Security Policy console. To enable auditing on multiple computers
within a domain, use Group Policy settings. In Group Policy, auditing
settings are located within Computer Configuration\Windows
Settings\Security Settings\Local Policies\Audit Policy node. After
changing auditing settings, you must restart the computer for the change
to take effect.
After enabling Audit Privilege Use, you can
monitor Event IDs 4648 and 4624 in the Security event log to determine
when users elevate privileges using the UAC consent dialog. Event ID
4648 will always precede 4624, and will have a process name that
includes Consent.exe, the UAC consent dialog. These events will not
appear if a user cancels the UAC consent dialog. Events with Event ID
4673 will appear if the user cancels a consent dialog; however, that
same event will appear under different circumstances as well.
After enabling Audit Process Tracking, you can
monitor Event ID 4688 to determine when administrators make use of Admin
Approval Mode to provide full administrator privileges to processes.
The description for this event includes several useful pieces of
information:
Security ID The user name and domain of the current user.
New Process Name
The path to the executable file being run. For more information about
the new process, look for an event with Event ID 4696 occurring at the
same time.
Token Elevation Type A number from 1 to 3 indicating the type of elevation being requested:
Type
1 (TokenElevationTypeDefault) is used only if UAC is disabled or if the
user is the built-in Administrator account or a service account. This
type does not generate a UAC prompt.
Type
2 (TokenElevationTypeFull) is used when the application requires (and
is granted) elevated privileges. This is the only type that generates a
UAC prompt. This type can also be generated if a user starts an
application using RunAs, or if a previously elevated process creates a
new process.
Type 3
(TokenElevationTypeLimited) is used when the application runs using
standard privileges. This type does not require a UAC prompt.
Note
that many events with Event ID 4688 won’t be applications launched by
the user. Most of these events are generated by background processes and
services that require no interaction with the user. To find the most
interesting events, filter the Security event log using Event ID 4688.
Then, use the Find tool to search for the phrase
“TokenElevationTypeFull”.
10. Other UAC Event Logs
Besides security auditing (which is not enabled by default), UAC provides two additional logs within Event Viewer:
Applications and Services Logs\Microsoft\Windows\UAC\Operational Logs UAC errors, such as processes that fail to handle elevation requirements correctly.
Applications and Services Logs\Microsoft\Windows\UAC-FileVirtualization\Operational Logs UAC virtualization details, such as virtualized files that are created or deleted.
If you are experiencing a problem and
you think it might be related to UAC, check these logs to see if there
is any related information.