4. Allowing Connections Through the Firewall
In some situations,
you want to allow other computers to initiate a connection to your
computer. For example, you might use Remote Desktop, play multiplayer
games, or chat via an instant messaging program; these types of programs
typically require inbound connections so that others can contact you.
The simplest way to
enable a connection is to click Allow A Program Or Feature Through
Windows Firewall, a link in the left pane of the main Windows Firewall
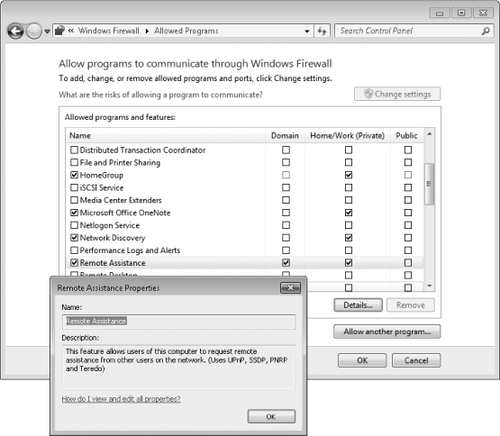
window. The list of programs and features that initially appears in
Allowed Programs, shown in Figure 2,
depends on which programs and services are installed on your computer;
you can add others, as described in the following sections. In addition,
program rules are created (but not enabled) when a program tries to set
up an incoming connection. To allow connections for a program or
service that's already been defined, simply select its check box for
each network location type on which you want to allow the program.
(You'll need to click Change Settings before you can make changes.)
In each of these cases,
you enable a rule in Windows Firewall that pokes a small hole in the
firewall and allows a certain type of traffic to pass through it. Each
rule of this type increases your security risk to some degree, so you
should clear the check box for all programs you don't need. If you're
confident you won't ever need a particular program, you can select it
and then click Remove. (Many of the list items included with Windows
don't allow deletion, but as long as their check boxes are not selected,
there's no danger.)
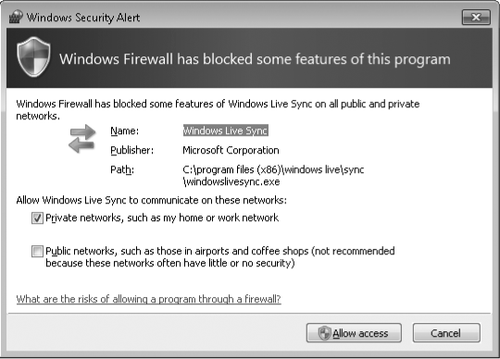
The first time you run a program
that tries to set up an incoming connection, Windows Firewall asks for
your permission by displaying a dialog box similar to the one shown
below. You can add the program to the allowed programs list by clicking
Allow Access.
When such a dialog box appears, read it carefully:
Is the program one that you knowingly installed and ran?
Is it reasonable for the program to require acceptance of incoming connections?
Are you currently using a network location where it's okay for this program to accept incoming connections?
If the answer to
any of these questions is no—or if you're unsure—click Cancel. If you
later find that a needed program isn't working properly, you can open
the allowed programs list in Windows Firewall and enable the rule.
Alternatively, you can set up the program from Allowed Programs, the window shown in Figure 15-6, without waiting for a Windows Security Alert dialog box to appear. Follow these steps:
Click Allow Another Program. The Add A Program dialog box appears.
In
Add A Program, select the program for which you want to allow incoming
connections. Or click Browse and navigate to the program's executable
file if it isn't shown in the Programs list.
Click Network Location Types.
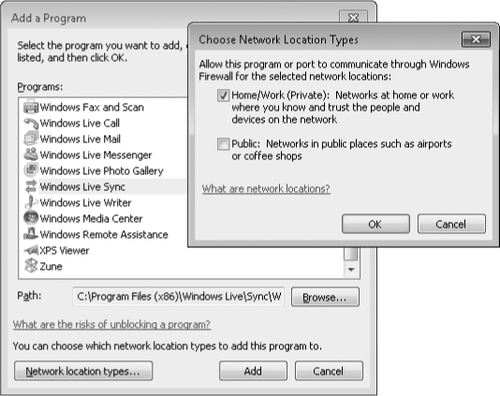
Select
the network location types on which you want to allow the program,
click OK, and click Add. (You can also select network locations in
Allowed Programs after you add the program.)
5. Restoring Default Settings
If you've played around a
bit with Windows Firewall and perhaps allowed connections that you
should not have, you can get back to a known, secure state by clicking
Restore Defaults in Windows Firewall. Be aware that doing so removes all
rules that you've added for all programs. Although this gives you a
secure setup, you might find that some of
your network-connected programs no longer work properly. As that
occurs, you can re-add each legitimate program that needs to be allowed,
as described on the previous pages.
6. Advanced Tools for Managing Windows Firewall
If you have any
experience at all with configuring firewalls, you'll quickly realize
that the Windows Firewall application in Control Panel covers only the
most basic tasks. Don't take that as an indication that Windows Firewall
is underpowered. To the contrary, you can configure all manner of
firewall rules, allowing
or blocking traffic based on program, port, protocol, IP address, and
so on. In addition, you can enable, disable, and monitor rules,
configure logging, and much more. With advanced tools, you can also
configure Windows Firewall on remote workstations. Because the interface
to these advanced features is rather daunting, Windows Firewall
provides the simplified interface described on the preceding pages. It's
adequate not only for less experienced users, but also for performing
the routine firewall tasks needed by information technology (IT)
professionals and others.
Nonetheless, our tour of
security essentials would not be complete without a visit to Windows
Firewall With Advanced Security, a snap-in and predefined console for
Microsoft Management Console (MMC) that offers granular control over
rules, exceptions, and profiles. To open it, in Windows Firewall click
Advanced Settings. (If you're using a standard account and you haven't
yet entered administrative credentials during this Windows Firewall
session, you'll need to enter them now.) Windows Firewall With Advanced
Security appears, as shown in Figure 3.
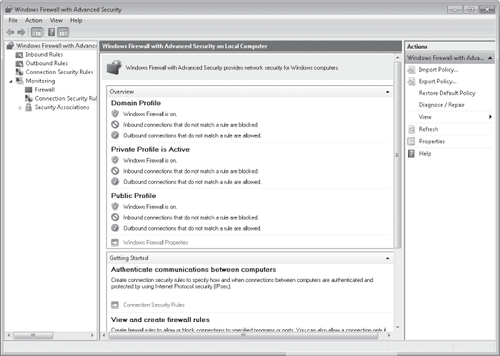
The initial
view presents information similar to that shown in Windows Firewall. Go
just a few steps further into the cave, however, and you could be lost
in no time. The "Windows Firewall with Advanced Security Getting Started
Guide" can brighten your path; view it at w7io.com/1502.
|
You don't need to open Windows Firewall to get to Windows Firewall With Advanced Security. In the Start menu search box, type wf.msc and press Ctrl+Shift+Enter to run it as an administrator.
|
If you're not intimidated by the Windows Firewall With Advanced Security console, you might want to try the command-line
interface for managing Windows Firewall. Because it can be scripted, it
can be useful if you need to make firewall settings repeatedly, whether
on a single computer as conditions change or on a fleet of computers.
To use the command- line interface, you use the Netsh command with the
Advfirewall context. You can get some terse help by typing netsh advfirewall
in a Command Prompt window.