Various methods of auditing the Exchange Server
environment exist to gather and store records of network and Exchange
Server access and to assist with the monitoring and tracking of SMTP
connections and message routing.
Typically used
for identifying security breaches or suspicious activity, auditing has
the added benefit of allowing administrators to gain insight into how
the Exchange Server 2010 systems are accessed and, in some cases, how
they are performing.
This article focuses on three types of auditing:
Audit logging— For security and tracking user access
SMTP logging— For capturing SMTP conversations between messaging servers
Message tracking— For tracking emails through the messaging environment
Audit Logging
In
a Windows environment, auditing is primarily considered to be an
identity and access control security technology that can be implemented
as part of an organization’s network security strategy. By collecting
and monitoring security-related events, administrators can track user
authentication and authorization, as well as access to various directory
services (including Exchange Server 2010 services).
Exchange Server 2010
relies on the audit policies of the underlying operating system for
capturing information on user access and authorization. Administrators
can utilize the built-in Windows Server event auditing to capture data
that is written to the security log for review.
Enabling Event Auditing
Audit policies are the
basis for auditing events on Windows Server 2003 and Windows Server 2008
systems. Administrators must be aware that, depending on the policies
configured, auditing might require a substantial amount of server
resources in addition to those supporting the primary function of the
server. On servers without adequate memory, processing power or hard
drive space, auditing can potentially result in decreased server
performance. After enabling auditing, administrators should monitor
server performance to ensure the server can handle the additional load.
To enable audit policies on a Windows Server 2008 server, perform the following steps:
1. | On the server to be audited, log on as a member of the local Administrators group.
|
2. | Select Start, Administrative Tools, and launch the Local Security Policy snap-in.
|
3. | Expand Local Policies and select Audit Policy.
|
4. | In the right pane, double-click the policy to be modified.
|
5. | Select to audit Success, Failure, or both.
|
6. | Click OK to exit the configuration screen, and then close the Local Security Policy tool.
|
Figure 1 shows an example of typical auditing policies that might be configured for an Exchange server.
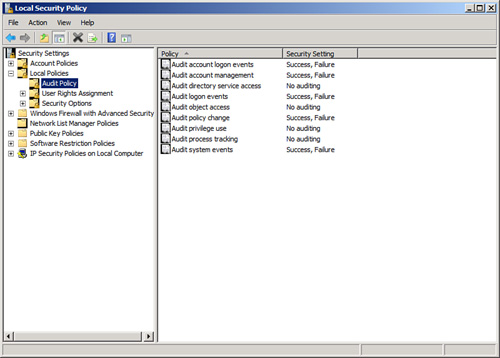
These audit policies can
be turned on manually by following the preceding procedure, configuring a
group policy, or by the implementation of security templates.
Note
After enabling
audit policies, Windows event logs (specifically the security log) will
capture a significant amount of data. Be sure to increase the “maximum
log size” in the security log properties page. A best practice is to
make the log size large enough to contain at least a week’s worth of
data, and configure it to overwrite as necessary so that newer data is
not sacrificed at the expense of older data.
Viewing the Security Logs
The
events generated by the Windows Server 2003 and Windows Server 2008
auditing policies can be viewed in the security log in the Event Viewer.
Understanding the
information presented in the security log events can be a challenge. The
event often contains error codes, with no explanation on their meaning.
Microsoft has taken strides to make this easier by providing a link to
the Microsoft Help and Support Center within the event.
When an administrator
clicks on the link, the Event Viewer asks for permission to send
information about the event to Microsoft. Administrators can select the
option to always send information if they want, and can then click Yes
to authorize the sending of the data. A connection is made to the Help
and Support Center, and information about the Event ID is displayed.
This information can be invaluable when trying to decipher the sometimes
cryptic events in the security log.
Administrators can use
the Filter feature (from the View menu) to filter the events based on
various fields. In addition, when searching for a specific event within a
specific time frame, administrators can select a specific window of
time to filter on.
For an extensive list of security event IDs and their meaning in Windows Server 2008, go to http://support.microsoft.com/kb/947226.
The information
supplied here on viewing security log Event IDs is intended to help
administrators get a basic understanding of the topic. There is much
more that can be learned on the subject of security auditing and event
monitoring, and the Microsoft website is an excellent resource for doing
so.