A firewall is used to prevent unauthorized users from
accessing private networks that are connected to other networks.
Typically, a firewall prevents external users from accessing an internal
corporate network from the Internet. All e-mail messages that enter or
leave the intranet pass through the firewall, which blocks messages that
do not meet specified security criteria.
How a Firewall Works
A firewall can act as a packet filter,
reviewing each data packet that enters or leaves the network. It can
allow or prohibit packets based on source address, destination address,
or port number. It can scan for viruses (if the appropriate software is
installed) and destroy any virus before it enters or leaves your
network. A firewall can act as a proxy server, hiding true network addresses and filtering out packets that contain inappropriate or corrupted data.
An Exchange
organization that accesses external networks should be protected by a
firewall. In particular, back-end servers that contain private stores
need strong protection. Front-end servers typically require weaker
protection and more functionality. Therefore, many organizations
implement light (or no) firewall protection between front-end servers
and the outside world, and strong firewall protection to protect
back-end servers and other sensitive parts of the intranet. The
front-end servers are then said to be in a demilitarized zone (DMZ),
also known as a perimeter network.
Exchange is inherently
an application-specific proxy server that understands mail protocol and
data and can determine if data is corrupted or from an unacceptable
source. If Exchange is configured correctly, you do not need a separate
proxy server.
TCP Port Filtering
Transmission
Control Protocol (TCP) enables two hosts to establish a connection and
exchange data. A TCP port provides a specific (abstract) location for
the delivery of the TCP segments. TCP ports are identified for a
specific application or service that uses TCP. For example, the HTTP
service uses TCP port 80, and Simple Mail Transfer Protocol (SMTP) uses
TCP port 25.
You can
secure network applications and services by restricting connections to
their associated ports. TCP port filtering enables you to control the
type of network traffic that reaches your Exchange servers and network
devices.
You can use a firewall
to allow only essential Internet traffic to pass through specified TCP
ports. You could, in theory, configure your network to allow only SMTP
traffic to pass through your firewall on port 25. In practice, Exchange
traffic requires additional ports to be opened to allow remote clients
and servers to communicate with your network. You can, however, filter
traffic through these ports (for example, by source address or domain
name) and prohibit traffic through ports that you are not using. Table 1 lists TCP ports and their associated services.
Table 1. Exchange Server 2003 Ports and Services
| Port | Service |
|---|
| 25 | SMTP |
| 80 | HTTP |
| 88 | Kerberos |
| 102 | Message Transfer Agent (MTA) - X.400 connector over TCP/IP |
| 110 | Post Office Protocol version 3 (POP3) |
| 119 | Network News Transfer Protocol (NNTP) |
| 135 | Client/server communication |
| | RPC |
| | Exchange administration |
| 143 | Internet Message Access Protocol version 4 (IMAP4) |
| 389 | Lightweight Directory Application Protocol (LDAP) |
| 443 | HTTP using Secure Sockets Layer (SSL) |
| 563 | NNTP using SSL |
| 636 | LDAP using SSL |
| 993 | IMAP4 using SSL |
| 995 | POP3 using SSL |
| 3268 and 3269 | Global catalog lookups |
Important
Table 11-1
lists all the ports that Exchange Server 2003 uses for all modes of
operation. However, this does not imply that you should open all these
ports in your firewall. For example, if you do not support IMAP4 or POP3
clients, the corresponding ports should be closed. In general, open as
few ports as necessary. |
MAPI Client Connection Through a Firewall
You can allow messages sent
by a MAPI client (such as Outlook) to connect to an Exchange Server
2003 server through a firewall by configuring RPC over HTTP. You can
also configure static port assignments for the Information Store (IS) by
adding entries to the Windows registry or configure Microsoft Internet
Security and Acceleration (ISA) Server to route all Internet traffic,
but the recommended option is to configure RPC over HTTP. This
eliminates the need for a virtual private network (VPN) connection when a
user is accessing Exchange information. Users running Outlook can
connect directly to an Exchange server over the Internet by using HTTP,
even if both the Exchange server and Outlook are behind firewalls and
located on different networks.
When you deploy RPC over
HTTP, you configure your Exchange front-end server as an RPC proxy
server. The RPC proxy server specifies what ports the RPC client uses to
communicate with domain controllers, global catalog servers, and the
Exchange servers. You can locate the RPC proxy inside the firewall or on
the DMZ.
Inside the Firewall
You can deploy ISA
Server in the DMZ and configure the RPC proxy server on an Exchange
front-end server inside the firewall. This eliminates the need to open
the ports for the RPC proxy server to communicate with other computers
because the ISA server is responsible for routing RPC over HTTP requests
to the Exchange front-end server. When you choose this option, you can
configure the RPC proxy server to use all the ports it needs within the
specified range.
On the DMZ
You can configure the
RPC proxy server on an Exchange Server 2003 front-end server located on
your DMZ. When using this option, you should limit the number of ports
that the RPC proxy server uses.
Practice: Configuring Exchange Server 2003 to Use RPC Over HTTP
To configure Exchange Server 2003 to use RPC over HTTP, you need to complete the following steps:
- Configure your Exchange front-end server (Server02) as an RPC proxy server.
- Configure basic authentication in the RPC virtual directory in Internet Information Services (IIS).
- Modify
the registry on the Exchange back-end server (Server01) that
communicates with the proxy server to use a specified number of ports.
- Open the specific ports on the internal firewall on the back-end server.
- Create an Outlook profile for your users to use with RPC over HTTP.
Exercise 1:Configure a Front-End Server to Use RPC Over HTTP
To configure your Exchange front-end server to use RPC over HTTP, perform the following steps:
1. | Ensure that your Windows 2003 Server installation CD is in the CD-ROM drive on Server02.
|
2. | On Server02, double-click Add Or Remove Programs on the Control Panel.
|
3. | Click the Add/Remove Windows Components icon.
|
4. | In the Windows Components dialog box that appears, select Networking Services, and then click Details.
|
5. | In the Networking Services Component dialog box, select RPC Over HTTP Proxy, and then click OK.
|
6. | In
the Windows Components dialog box, click Next to install the RPC over
HTTP Proxy Windows component. Follow the steps in the Configure
Components Wizard. Click Finish to close the wizard.
|
Exercise 2: Configure the RPC Virtual Directory
To configure the RPC virtual directory on the RPC proxy server (Server02), perform the following steps:
1. | On Server02, open the IIS Manager console.
|
2. | Navigate to Server02\Web Sites, expand Default Web Site, right-click Rpc, and then click Properties.
|
3. | Click the Directory Security tab on the Rpc Properties page, and then click Edit in the Authentication And Access Control pane.
|
4. | Disable
Anonymous Access and select Basic Authentication in the Authentication
Methods window. If a warning box appears, then click Yes to close it.
Click OK.
|
5. | Click OK to close the IIS Manager console.
|
Exercise 3: Configure the RPC Proxy Server to Use Specific Ports
In
this exercise, you configure the RPC proxy server (Server02) to use
specified ports. In your test network, you can configure the same ports
on Server01. In a real-world scenario, you need to repeat the
configuration on all the servers with which your frontend server
communicates.
To configure the RPC proxy server to use a specified number of ports for RPC over HTTP, perform the following steps:
1. | On Server02, from the Start menu, click Run, type regedit in the Run box, and then click OK.
Caution Take care when editing the registry. Incorrect registry changes can damage your operating system. |
|
2. | Navigate to the registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Rpc\RpcProxy.
|
3. | Right-click the Valid Ports registry key and click Modify.
In the Edit String window, in the box under Value Data, enter the following information: Server01:593;Server01:6001-6004
Note Server01
is also the domain controller and catalog server on your test network.
In a production network, you need to include all the domain controllers
(including the global catalog server) and back-end Exchange servers with
which your RPC proxy server communicates. |
|
4. | Close the registry editor on Server02.
|
5. | To
configure the back-end Exchange server (Server01) to use specified
ports for RPC over HTTP requests, start the registry editor on that
server.
|
6. | Navigate to the registry key HKEY_LOCAL_MACHINE\SYSTEM\ CurrentControlSet\Services\MSExchangeSA\Parameters.
|
7. | Right-click Rpc/HTTP NSPI Port, and then click Modify.
Note If
Rpc/HTTP NSPI Port does not exist, then you need to create it. In this
case, click Edit, click New, and then select DWORD Value. |
|
8. | In the Base window, select Decimal.
|
9. | In the Value Data field, enter 6003, as shown in Figure 1, and then click OK.
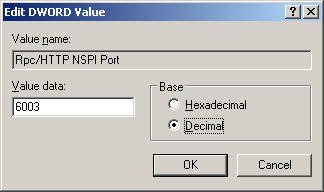
|
10. | To set the port for DS Referral, right-click HTTP Port, and then click Modify.
|
11. | As before, select Decimal in the Base window, type 6003 in the Value Data field, and then click OK.
|
12. | To use the Exchange Store, navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\MSExchangeIS\ParametersSystem.
|
13. | Right-click RPC/HTTP Port, and then click Modify.
|
14. | Select Decimal in the Base window, type 6001 in the Value Data field, and then click OK.
|
15. | Close the registry editor on Server01.
|
Note
The
above exercise is a simplified procedure to illustrate this technique
on a test network. For more details about configuring RPC over HTTP,
search www.microsoft.com for the Microsoft Exchange Titanium Getting Started Guide. |
Exercise 4:Create an Outlook Profile to Use with RPC Over HTTP
For users to use RPC
over HTTP from their client computers, they need an Outlook profile that
is set to use RPC over HTTP. This is normally done on a client
computer. If you want to practice the technique on your test network,
you can perform the steps on Server01.
Note
Server01
is a domain controller. On a production network, you would be unlikely
to install a modem on a domain controller or to use it as a client. Here
you are using a two-computer network for learning purposes only. |
To create an Outlook profile to use RPC over HTTP, perform the following steps:
1. | On Server01, from the Start menu, click Control Panel.
|
2. | If
you are using Category View in Control Panel, then click Other Control
Panel Options in the See Also pane, and then select Mail.
|
3. | If you are using Classic View in Control Panel, then select Mail.
|
4. | Click Show Profiles.
|
5. | In the Mail dialog box, click Add.
|
6. | In the New Profile dialog box, enter a name for this profile in the Profile Name box—for example, RPC over HTTP.
|
7. | In the New E-Mail Accounts Wizard, select Add A New E-Mail Account, and then click Next.
|
8. | On the Server Type page, select Microsoft Exchange Server, and then click Next.
|
9. | In the Exchange Server Settings dialog box, shown in Figure 2, enter Server01 and the account user name where appropriate. Click Check Name. Click OK.
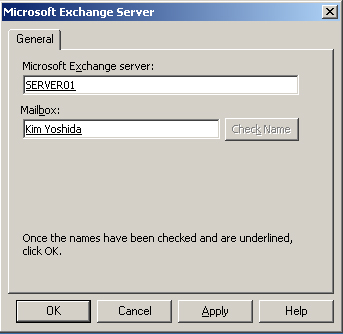
|
10. | Click More Settings.
|
11. | On the Connection tab, in the Connection pane, select Connect Using Internet Explorer’s Or A 3rd Party Dialer.
|
12. | In the Modem pane, select Connect To My Exchange Mailbox Using HTTP.
|
13. | Click Exchange Proxy Settings.
|
14. | On the Exchange Proxy Settings page, in the Connections Settings window, enter server01.tailspintoys.com in the Use This URL To Connect To My Proxy Server For Exchange box.
|
15. | Select Connect Using SSL Only.
|
16. | Select Mutually Authenticate The Session When Connecting With SSL.
|
17. | Enter msstd:server02.tailspintoys.com in the Principal Name For Proxy Server box.
|
18. | On
the Exchange Proxy Settings page, in the Proxy Authentication Settings
window, select Basic Authentication from the Use This Authentication
When Connecting To My Proxy Server For Exchange drop-down menu.
|
19. | Click OK.
|
20. | Click Finish.
|
Exercise 5: Configure an Internet Connection Firewall
You may choose
to use a hardware firewall supplied by a manufacturer such as Cisco or
SonicWALL. In that case, refer to the manufacturer’s instructions for
configuration. However, you may choose to configure Microsoft Internet
Connection Firewall (ICF) that is supplied with Windows 2003 Server.
To enable and configure ICF, perform the following steps:
1. | On Server01, access the local area connection that connects to Server02.
|
2. | Right-click the connection icon and click Properties.
|
3. | On
the Advanced tab, select the Protect My Computer And Network By
Limiting Or Preventing Access To This Computer From The Internet check
box, and then click Settings.
|
4. | On
the Services tab of the Advanced Settings dialog box, select the
services that you want to pass through the firewall. This dialog box is
shown in Figure 3. You can add services and specify ports by clicking Add.
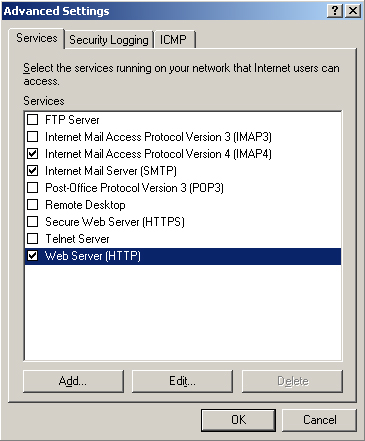
|
5. | |
6. | Click OK to close the Local Area Connection Properties box. |