7. Terminal Services Group Policy Options and Changes
Just like most aspects of
Windows Server 2008, Group Policy plays a big role. Within Windows
Server 2008, there is such a vast array of available information,
including setup options and application/desktop customizations, that
Group Policy infiltrates virtually the entire enterprise. On the
Terminal Services and application levels, you can use Group Policy for
deploying, publishing, and assigning applications access scripting and a
cacophony of other easily (or not so easily) assignable policies. At
the enterprise level, you need to pay close attention to three very
important types of policy settings: Easy Print, TS Gateway
configuration, and RemoteApp client settings.
7.1. Terminal Services Easy Print
Before Terminal Services
Easy Print (or just Easy Print), printing could be a bit of a hassle
with Terminal Services-based applications. The reason for this is that
at the end of the day the application is actually on the server. So,
what happens when the server is told to print? The server prints, of
course! It finds whatever locally installed printer is available and
goes to town. Obviously, this may not be what the user desires. In fact,
it's sort of funny to imagine a high-powered executive flying
first-class from London to New York while accessing a Terminal Services
program and continuously hitting the Print button but not understanding
why, for some reason, his portable printer isn't working. Meanwhile,
back at the ranch, the print room keeps receiving dozens of requests for
a 100-page spreadsheet. Good times.
To avoid these
escapades, Microsoft really thought through Easy Print when it
implemented the feature in Windows Server 2008. Easy Print works by
using whatever locally installed drivers are available on the machine
that is remotely connecting to the Terminal Services server. When it
connects, it does so either through Group Policy or through a user
interface tool that is customizable from the local machine. What makes
this exceptionally grand is that Easy Print functions by proxy and
supports almost all printer types, legacy or not. Thus, it really makes
it a matter of pointing and clicking, without the hassle of installing
drivers.
For the exam, you need to be
familiar with the changes that were made in Group Policy (GP), because
there's a strong chance you will be tested on them.
The
first change Microsoft came
up with is a way for you to forward only the default printer—instead of
all printers—to the client machine. The policy is located at
AdministrativeTemplates\Windows Components\Terminal Services\Terminal
Server\Printer Redirection.
This is quite convenient if you don't want all your printers forwarding to just one spot.
The second major change that
Microsoft made (which was conveniently explained by the Microsoft
Terminal Services team during beta 3—many thanks to them) is called printer scope redirection.
In Windows Server
2003, whenever printers were redirected with Terminal Services, an
administrator could see every single redirection that happened, and it
became a very big headache. Now, in Windows Server 2008, printer
redirection is treated very much the same way as drive redirection, so
printers now have a session ID based on their session in the list of
Windows Server access control lists.
Along with printer
scope redirection and default printer forwarding, Microsoft introduced
per-session default printers. How this works in a nutshell is that it
allows a different default printer to be established for each unique
session that a user establishes.
The last major change in
Windows Server 2008 is that the name of a redirected printer is much
shorter. Now, instead of using the full printer name followed by the
client name as in Windows Server 2003, the printer names in the Terminal
Services session show up in this format: Printer Name (SessionID). For
example, the ink-jet printer in the session ID number 1 would be
Inkjet(1).
7.2. TS Gateway Policy
Just when you thought you
were done with (and understood) Terminal Services Gateway servers, they
raise their ugly heads again! Well, they are really not that ugly—in
fact, they are quite convenient once you understand them. The important
thing to remember about TS Gateway servers is that there are a lot of
new Group Policy settings available and we need to understand them.
First and foremost, all policies implied on a gateway come in one of two forms: enabled and enforced. Enabled group policies are there for the users to implement if they desire. Enforced
policies, on the other hand, are demands that Windows Server 2008
places on users to require them to go along with certain policies.
Three Group Policy
settings—which apply regardless of whether a particular policy is
enabled or enforced—are important for you as an administrator of Windows
Server 2008. They are as follows:
Set TS Gateway Authentication Method
This Group Policy
setting allows you to set and specify the type of authentication method
users will need to implement when they are connecting to your TS Gateway
server from remote locations.
Set the TS Gateway Server Address
I bet you can guess what
this one does! This Group Policy setting tells the user what connection
method they should use whenever an internal resource is unavailable
through a direct connection. It's a nice trick, because it makes users
default to this location whenever they cannot connect, thus prioritizing
it for the network.
Enable Connections Through The TS Gateway
This Group Policy setting actually allows
users to connect to a TS Gateway server. Ordinarily, administrators
will use the policy in conjunction with the Set The Gateway Server
Address setting. This is because in order to connect, you have to
specify a gateway. It's sort of like saying "OK, connect to a gateway"
and then saying "Use the gateway specified at this location."
7.3. Controlling Client Behavior for RemoteApp Programs
This sounds a lot fancier
than it really is. In reality, "controlling client behavior" just means
that you as an administrator can specify certain Group Policy settings
to ensure that resources are assessed in a certain way. For the exam,
just remember that RemoteApp program client behavior can be adjusted by
specifying a publisher as trusted or blocked from certain resources.
8. Terminal Services Maintenance and Error Recovery
If you remember the fundamental
law of the universe known as Murphy's law, you will remember that if
anything can go wrong, it will. That's not actually true, but it's
certainly funny, and for computers in general it seems all too accurate.
I'm happy to report that Windows Server 2008 gives us some procedures
to use in case we see errors or problems with Terminal Services. In
fact, in Windows Server 2008 Microsoft introduced a new mode to make
logging maintenance issues even easier. I'll discuss it now.
4.8.1. Terminal Services' Terminal Server Drain Mode Feature
Back in the "old days" of
Windows Server 2003, administrators would sometimes have to take servers
hosting Terminal Services down for maintenance. Usually, this was a big
hullabaloo and involved logging on to the server and using the command
line to disable every single connection logging into the server and then
bringing the server offline to do the maintenance. Now, with Windows
Server 2008, there is a new and improved way of isolating problems using
the Terminal Server Drain Mode feature.
The Terminal Server Drain
Mode feature allows an administrator to shut down any new sessions being
established with a server. This is useful because it doesn't cut off
currently existing sessions. It just makes it impossible for new
sessions to be established. You can put your server in the Terminal
Server Drain Mode feature in one of two ways: either through the GUI or
through the command line. Either way produces the same results. It's a
matter of personal preference. Some administrators like to do everything
via the command line, and some prefer to use the graphical user
interface.
Using the GUI, you can go to
Terminal Services configuration from the Terminal Services menu in
Administrative Tools and then double-click Terminal Server Drain Mode,
as shown in Figure 3, which brings you to a dialog box.
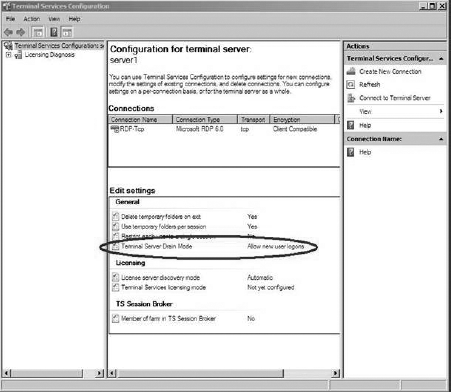
Alternatively, you can use the command line with the change logon command, chglogon.exe.
8.2. Common Event Codes
One of the best tricks you can
do for yourself—both in order to pass the exam and to become a better
administrator—is to memorize certain event codes. The reason for this is
twofold. First, it helps you pass your exam. Second, if you immediately
recognize an event code and don't have to look it up in Microsoft's
documentation, you will save yourself a lot of research time.
8.2.1. Remote Desktop Event ID 1041
When this event occurs, the
message "Autoreconnect failed to reconnect user to session because
authentication failed. (%1)" usually appears. All this means is that on
the initial attempt to authenticate, the process failed. The best way to
resolve this error is to start a new session and try the process again.
By default, Remote Desktop connections will try to reestablish
themselves.
The most important thing to
remember is that this error code is, surprisingly, not for
troubleshooting—it's a security feature. If this code is occurring many
times in your event log, there is a strong chance that someone is trying
to access your server with evil intent.