One
of the most powerful troubleshooting tools at the disposal of
SharePoint and ISA administrators is the logging mechanism, which gives
live or archived views of the logs on an ISA server, and allows for
quick and easy searching and indexing of ISA Server log information,
including every packet of data that hits the ISA server.
Note
Many of the advanced features of ISA logging are only available when using MSDE or SQL databases for the storage of the logs.
Examining ISA Logs
The ISA logs are accessible via the Logging tab in the details pane of the Monitoring node, as shown in Figure 1.
They offer administrators the ability to watch, in real time, what is
happening to the ISA server, whether it is denying connections, and what
rule is being applied for each Allow or Deny statement.
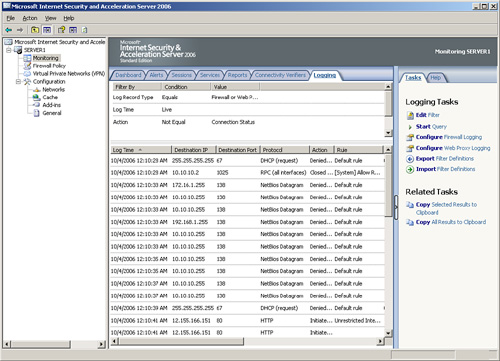
The logs include pertinent information on each packet of data, including the following key characteristics:
Log Time— The exact time the packet was processed.
Destination IP— The destination IP address of the packet.
Destination Port— The destination TCP/IP port, such as port 80 for HTTP traffic.
Protocol— The specific protocol that the packet utilized, such as HTTP, LDAP, RPC, or others.
Action— The type of action the ISA server took on the traffic, such as initiating the connection or denying it.
Rule— The particular firewall policy rule applied to the traffic.
Client IP— The IP address of the client that sent the packet.
Client Username— The username of the requesting client. Note that this is only populated if using the Firewall Client.
Source Network— The source network from which the packet came.
Destination Network— The network where the destination of the packet is located.
HTTP Method— If HTTP traffic, the type of HTTP method utilized, such as GET or POST.
URL— If HTTP is used, the exact URL that was requested.
By
searching through the logs for specific criteria in these columns, such
as all packets sent by a specific IP address, or all URLs that match http://sharepoint.companyabc.com, advanced troubleshooting and monitoring is simplified.
Customizing Logging Filters
What is displayed in the
details pane of the Logging tab is a reflection of only those logs that
match certain criteria in the log filter. It is highly useful to use the
filter to weed out the extraneous log entries, which just distract from
the specific monitoring task. For example, on many networks, an
abundance of NetBIOS broadcast traffic makes it difficult to read the
logs. For this reason, a specific filter can be created to only show
traffic that is not NetBIOS traffic. To set up this particular type of
rule, do the following:
1. | From the ISA Admin console, click the Monitoring node from the console tree, and select the Logging tab in the details pane.
|
2. | On the Tasks tab in the tasks pane, click the Edit Filter link.
|
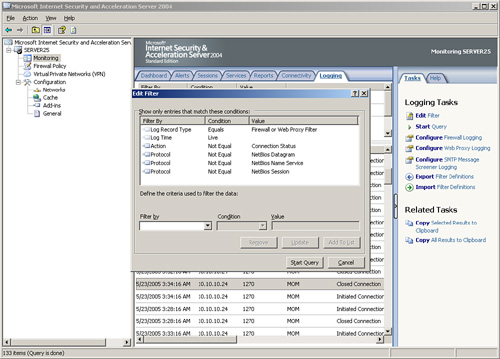
3. | In
the Edit Filter dialog box, change the Filter by, Condition, and Value
fields to display Protocol, Not Equal, NetBios Datagram, and then click
Add to List.
|
4. | Repeat for the NetBios Name Service and the NetBios Session values, so that the dialog box looks like the one displayed in Figure 2.
|
5. | Click Start Query.
|
Note
It
cannot be stressed enough that this logging mechanism is quite
literally the best tool for troubleshooting ISA access. For example, it
can be used to tell if traffic from clients is even hitting the ISA
server, and if it is, what is happening to it (denied, accepted, and so
on).