After the SPNs have been set, the next step is to
enable trust for delegation in Active Directory. You can do so in the
Active Directory Users and Computers MMC snap-in. This usually requires
domain administrator privileges because enabling it incorrectly could
result in a malicious user “borrowing” credentials of other users. The
first place that trust for delegation needs to be set is on the user
account that the PPS service application uses for its application pool.
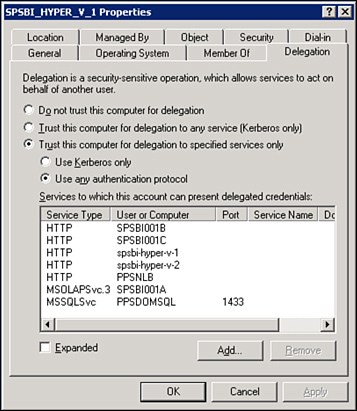
The user needs to be trusted for
delegation to any SPNs configured in the previous step. For maximum
security, select the Trust This User for Delegation to the Specified
Services Only option and the Use Any Authentication Protocol option when
enabling this, as shown in Figure 1. Doing so enables the user account to impersonate the user accessing the dashboard to the data source.
The other place where trust
for delegation needs to be configured is for all servers in the farm
hosting the PPS service. The steps are nearly identical to setting trust
for the user account, except this is on the computer account. This
enables the application server to impersonate the user accessing the
dashboard to the data source.
Tip
If you do not see the
Delegation tab when viewing the user or computer accounts in the Active
Directory Users and Computers snap-in, check your SPNs. This tab appears
only when SPNs are detected for the account being viewed.