6. Using Transport Protection Rules
Email messages and attachments typically contain business critical
information, including personally identifiable information (PII), such as
contact details, credit card numbers, and employee records. Industry-specific
and local regulations govern the collection, storage, and disclosure of PII.
Organizations create messaging policies that provide guidelines about how to
handle sensitive information. In Exchange Server 2010, transport protection
rules implement messaging policies by inspecting message content, encrypting
sensitive email content, and using rights management to control access.
Transport protection rules are transport rules that apply an AD RMS rights
policy template to protect messages through the IRM.
Exchange Server 2010 ships with the Do Not Forward template. When this
template is applied to a message, only the recipients addressed in the message
can decrypt it. These recipients cannot forward the message to anyone else, copy
content from the message, or print the message. Additional RMS templates can be
created using your organization’s AD RMS server to meet your rights
protection requirements.
6.1. Creating a Transport Protection Rule
You can use transport protection rules to apply persistent rights
protection to messages based on message properties such as sender,
recipient, message subject, and content. You can use either the EMC or the
EMS to create a transport protection rule. To use the EMC, carry out the
following procedure:
Open the EMC and expand the tree on the Console pane.
Under Organization Configuration, click Hub Transport.
Click New Transport Rule on the Actions pane. This opens the New
Transport Rule Wizard.
On the Introduction page, provide a name and, optionally, a
comment. If you do not want the new rule to be enabled automatically
when it is created, clear the Enabled check box.
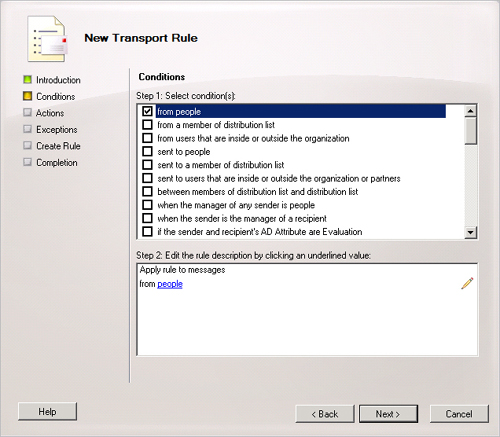
Click Next. On the Conditions page, shown in Figure 9, complete the following
fields:
In the Step 1. Select Condition(s) box, select all the
conditions that you want to apply to this rule. Note that if
you do not select any conditions, all messages handled by
Hub Transport servers are IRM protected. In a production
environment, this can lead to a considerable resource
requirement.
If you selected conditions in the Step 1. Select
Condition(s) box, click each blue underlined word in the
Step 2. Edit The Rule Description By Clicking An Underlined
Value box.
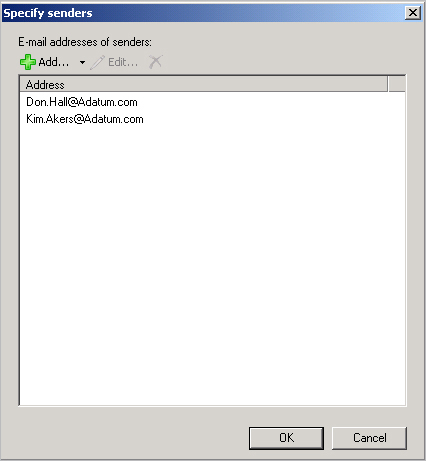
When you click a blue underlined word, a window opens, as shown in
Figure 10, to prompt you
for the values to apply to the condition. Select the values that you
want to apply or type the values manually. If the window requires
that you manually add values to a list, type a value and then click
Add. Repeat this process until you have entered all the values and
then click OK to close the window.
Repeat the previous step for each condition that you selected.
After you configure all the conditions, click Next on the Conditions
page.
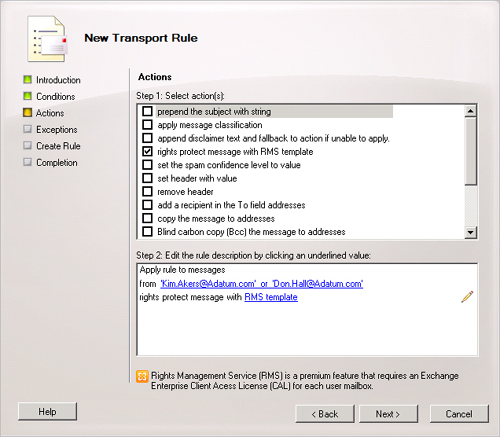
On the Actions page, shown in Figure 11,
complete the following fields:
In the Step 1. Select Actions box, select the Rights
Protect Message With RMS Template check box.
In the Step 2: Edit The Rule Description By Clicking An
Underlined Value box, click the underlined words RMS
Template.
In the Select RMS Template dialog box, select an available RMS
template and then click OK.
Click Next. Optionally, on the Exceptions page, select an
exception you want to use and specify the appropriate value as
required.
Click Next. On the Create Rule page, review the Configuration
Summary. Make sure that the RMS template selected is the one you
intend to use.
Click New to create the transport rule.
On the Completion page, if the status is Failed, click Back and
review your settings. Otherwise, the status is Completed, in which
case click Finish to close the wizard.
You
can also use the EMS to create a transport protection rule. The following
command creates the transport protection rule Protect-Confidential. The rule
IRM-protects messages that contain the word “Confidential” in
the Subject field using the Do Not Forward template:
New-TransportRule -Name "Protect-Confidential" -SubjectContainsWords "Confidential"
-ApplyRightsProtectionTemplate "Do Not Forward"
6.2. Protecting Outlook and OWA Messages
Outlook and OWA users can apply IRM protection to messages by applying an
AD RMS rights policy template. However, this gives users the option of
sending messages in clear text without IRM protection. In organizations that
use email as a hosted service, information leakage can occur as a message
leaves the client and is routed and stored outside the boundaries of the
organization. Email hosting companies might have well-defined procedures and
checks to help mitigate the risk of information leakage, but an organization
loses control of the information after a message leaves its boundary.
Outlook protection rules can help protect against
this type of information leakage.
Outlook protection rules help an organization protect against the risk of
information leakage by automatically applying IRM protection to messages. In
Outlook 2010, messages are IRM-protected before they leave the Outlook
client. This protection is also applied to any attachments using supported
file formats. When you create Outlook protection rules on an Exchange Server
2010 server, these rules are automatically distributed to Outlook 2010 by
Exchange Web services. Outlook 2010 can then apply the rule, provided that
the AD RMS rights policy template is available on client computers.
Outlook protection rules are applied in Outlook 2010 before the message
leaves the user’s computer. Messages protected by an Outlook
protection rule enter the transport pipeline with IRM protection already
applied and are saved in an encrypted format in the Sent Items folder of the
sender’s mailbox.
If you use transport protection rules, users have no indication of whether
a message will be automatically protected on the Hub Transport server. When,
on the other hand, an Outlook protection rule is applied to a message in
Outlook 2010, users know whether a message will be IRM protected. If
required, users can also select a different rights policy template.
You can use the EMS but not the EMC to create an Outlook protection rule.
For example, the following command creates the Outlook protection rule
MyProject. This
rule protects messages sent to the TechnicalAuthors distribution group with
the AD RMS template Do Not Forward:
New-OutlookProtectionRule -Name "MyProject" -SentTo "TechnicalAuthors"
-ApplyRightsProtectionTemplate "Do Not Forward"
You can specify whether the user can override the rule, either by removing
IRM protection or by applying a different AD RMS rights policy template. If
a user overrides the IRM protection applied by an Outlook protection rule,
Outlook 2010 inserts the X-MS-Outlook-Client-Rule-Overridden header in the
message. This allows an administrator to discover that the user overrode a
rule.
You can use the Get-OutlookProtectionRule EMS cmdlet
to obtain the configuration of an existing Outlook protection rule and the
Set-OutlookProtectionRule EMS cmdlet to change that
configuration. You can also use the EMS
Remove-OutlookProtectionRule cmdlet to remove an
Outlook protection rule. For example, the following command removes the
MyProject Outlook protection rule:
Remove-OutlookProtectionRule -Identity "MyProject"
6.3. Enabling or Disabling IRM in OWA
If you enable IRM in OWA in your organization, OWA users can IRM-protect
messages by applying an AD RMS template created on your AD RMS cluster. This
also enables OWA users to view IRM-protected messages. Note that before you
enable IRM in OWA, you must add the Federated Delivery mailbox to the super
users group on the AD RMS cluster, as described earlier in this
lesson.
You can use commands based on
the Set-IRMConfiguration EMS cmdlet to enable or
disable IRM in OWA for your entire Exchange Server 2010 organization. You
can also control IRM in OWA at the following levels:
Per-OWA virtual
directory
To enable or disable IRM for an OWA virtual directory, use the
Set-OWAVirtualDirectory cmdlet and set
the IRMEnabled parameter to $true (the default) or $false. This
allows you to disable IRM for one OWA virtual directory on a
Client Access server while keeping it enabled on another virtual
directory on a different Client Access server.
Per-OWA mailbox
policy
To enable or disable IRM for an OWA mailbox policy, use the
Set-OWAMailboxPolicy cmdlet and set the
IRMEnabled parameter to $true (the default) or $false. This
allows you to enable IRM in OWA for one set of users and disable
it for other users by assigning them a different OWA mailbox
policy.
You can use the EMS but not the EMC to enable or disable IRM in OWA. The
following command enables IRM in OWA for an entire Exchange Server 2010
organization:
Set-IRMConfiguration -OWAEnabled $true
The following command disables IRM in OWA for the virtual directory
MyVirtualDirectory on Client Access server VAN-EX1:
Set-OWAVirtualDirectory -Identity VAN-EX1\MyVirtualDirectory -IRMEnabled $false
Note:
Note that the Set-IRMConfiguration cmdlet
supports the OWAEnabled parameter, whereas the
Set-OWAVirtualDirectory and
Set-OWAMailboxPolicy cmdlets support the
IRMEnabled parameter.