This
article discusses transport rules and how you can use them to apply messaging
policies on both Hub Transport and Edge Transport servers. You can use Windows
Rights Management Services (RMS) to configure
Information Rights Management (IRM) so that your users can
send secure IRM-protected messages. The RMS prelicensing agent
is installed in Exchange Server 2010 to enable you to do this. The lesson looks at
how you use transport protection rules to configure rights protection.
Moderated transport is a new feature in Exchange Server 2010 that enables a
moderator to intercept and check mail to a specified recipient (typically a
distribution group) and allow or block delivery depending on the acceptability of
the message. This lesson discusses how moderated transport works, how you configure
a moderated recipient and specify a moderator, and how you configure an additional
arbitration mailbox.
1. Using Transport Rules
Your organization may be required by law, regulatory requirements, or company
policies to apply messaging policies that limit interaction between recipients
and senders (both individual senders and departmental groups). Such limitations
can apply both inside and outside the organization. In addition to limiting
interactions inside the organization, you also need to prevent inappropriate
content from entering or leaving the organization, filter confidential
information, track or archive specified messages, redirect inbound and outbound
messages so that they can be inspected, and apply disclaimers to messages as
they pass through the organization. The mechanism that enables you to accomplish
all these aims is the transport rule.
You can use transport rules to apply messaging policies to email messages that
flow through the transport pipeline on Hub Transport and Edge Transport servers.
These rules permit you to comply with messaging policies, secure messages,
prevent information leakage, and protect messaging systems.
You create a transport rule by specifying rule conditions, exceptions, and
actions. The transport rule agent (on Hub Transport servers) or the edge rules
agent (on edge servers) processes the transport rule. If the condition is
satisfied and none of the exceptions apply, the action is performed.
1.1. Transport Rule Conditions
You
use transport rule conditions to identify messages to which a transport rule
action is applied. A condition consists of one or more predicates that
specify which parts of a message should be examined. Predicates can examine
message fields or headers, such as To, From, or Cc. They can also examine
message characteristics, such as message subject, message size, message
body, attachments, and message classification. If appropriate, you can
specify a comparison operator, such as equals, does not equal, or contains,
and a matching value.
For example a predicate could be MessageSize,
From, FromMemberOf,
FromScope, SubjectContains,
FromAddressContains,
SubjectMatches, and so on. Some predicates can be
used only on Hub Transport servers, whereas others can be used on both Hub
and Edge Transport servers. You can obtain list of transport rule predicates
by entering the following Exchange Management Shell (EMS) command:
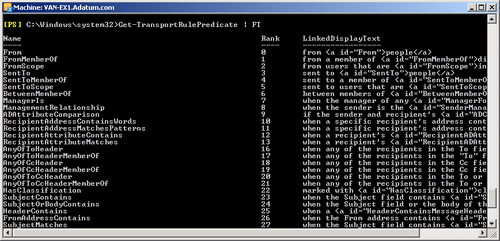
Get-TransportRulePredicate | FT
Figure 1 shows some of the
output from this command run on the Hub Transport server VAN-EX1. The output
you obtain from the command depends on whether you run it on a Hub Transport
or an Edge Transport server. If you want to save this list in a convenient
format, you can redirect the output of the command to a text file.
1.2. Transport Rule Exceptions
Transport rule exceptions are based on the transport rule predicates that
you use to build transport rule conditions. However, unlike conditions,
exceptions identify messages to which transport rule actions should not be
applied. If an exception is met, this prevents the actions specified in the
transport rule from being applied to an email message, even if that message
matches all configured conditions.
Exceptions include, for example, ExceptIfFrom,
ExceptIfFromMemberOf,
ExceptIfFromScope,
ExceptIfAttachmentContainsWords,
ExceptIfAttachmentSizeOver,
ExceptIfSCLOver, and so on. As with predicates, the
name of the exception is typically self-explanatory.
1.3. Transport Rule Actions
A transport rule action defines the action that is applied to messages
that match the transport rule conditions and do not match any exceptions.
You can use a transport rule to reject, delete, or redirect a message; to
add recipients; to add prefixes in the message subject; to insert
disclaimers and personalized signatures in the message body; and to apply a
message classification . You can obtain a list of
transport rule actions by entering the following EMS command:
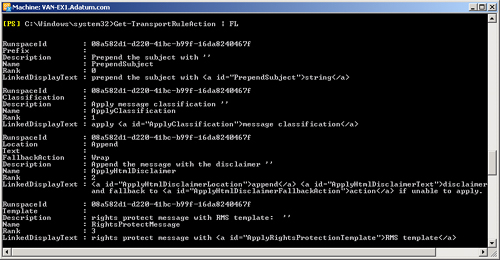
Get-TransportRuleAction | FL
Figure 2 shows some of the output
from this command run on a Hub Transport server. As with transport rule
predicates, the output you obtain from the command depends on whether you
run it on a Hub Transport or an Edge Transport server. If you want to save
the list in a convenient format, you can redirect the output of the command
to a text file.
Figure 2. Listing transport rule actions
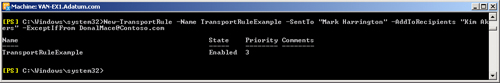
You can use a command based on the New-TransportRule
EMS cmdlet to create a transport rule and specify conditions, exceptions,
and actions. For example, the following command creates the transport rule
TransportRuleExample, which adds Kim Akers to the recipients of any email
messages sent to Mark Harrington except for messages that are sent by the
external user [email protected]:
New-TransportRule -Name TransportRuleExample -SentTo "Mark Harrington" -AddToRecipients
"Kim Akers" -ExceptIfFrom [email protected]
The output from this command is shown in Figure 3. If you want to try out this
command, you need to first create the Mark Harrington mailbox.
1.4. Applying Messaging Policies
Transport rules allow you to apply
messaging policies to messages in the transport pipeline. Actions such as
redirecting a message or adding recipients, rights-protecting a message, and
rejecting or silently deleting a message can be taken on messages that match
the conditions and none of the exceptions defined in the rule.
The transport rules agent applies transport rules on
a Hub Transport server and fires on the OnRoutedMessage
transport event. All messages in an Exchange Server 2010 organization pass
though at least one Hub Transport server before they are delivered, whether
they are internal messages or messages to and from external users.
Active Directory stores transport rules that are configured on Hub
Transport servers so that these transport rules are accessible to all Hub
Transport servers in the organization through Active Directory replication.
This lets you apply a single set of rules across an entire organization. Hub
Transport servers query Active Directory to retrieve an organization’s
current transport rule configuration and then apply the rules to
messages.
The scope of transport rules applied to Hub Transport servers is the
entire exchange organization, and they can be applied to all message types
except system messages. These transport rules can expand distribution group
membership and access Active Directory attributes, and they can inspect or
modify IRM-protected message content. IRM, RMS templates, and transport
protection rules are discussed later in this lesson.
Note:
Bear in mind that a transport rule can block delivery of email
messages to an Exchange Server 2010 organization. However, it cannot
prevent users from communicating through networked file shares,
newsgroups, and forums.
Note:
ACTIVE DIRECTORY REPLICATION
For more information about Active Directory replication, see
http://go.microsoft.com/fwlink/?LinkId=129505.
The edge rules agent processes transport rules on
Edge Transport servers and fires on the EndOfData
transport event. You should, as much as possible, apply messaging hygiene
and policy to inbound Internet email on Edge Transport servers so that
unwanted messages are not sent to your internal servers. The edge rules
agent can also remove or block messages that contain harmful or
objectionable content and can help block messages that contain viruses,
worms, and other types of malicious code. This is particularly important
during the interval between the creation of malicious code and updates to
your organization’s antivirus software. In addition, the edge rules
agent can mitigate the impact of denial of service attacks by blocking
traffic from a source that is sending an excessive number of
messages.
Outbound Internet email can also be subjected to policy-based scrutiny at
Edge Transport servers, and you can prevent harmful or objectionable content
from leaving your organization.
Message content can be checked to prevent sensitive information from being
leaked to external recipients.
Transport rules that are configured on Edge Transport servers are stored
in Active Directory Lightweight Directory Services (AD LDS), formerly known
as Active Directory Application Mode (ADAM), on each server. Rules
configured on one Edge Transport server do not automatically replicate to
other Edge Transport servers in an Exchange organization. You may decide to
configure each Edge Transport server with identical transport rules, and you
can use the EMS commands based on the
Export-TransportRuleCollection
and Import-TransportRuleCollection cmdlets to do so.
You also have the option of configuring different transport rules on each
of your Edge Transport servers to address the email message traffic patterns
of each server. The scope of a transport rule configured on an Edge
Transport server is the local server. Edge server transport rules apply to
all types of message, cannot expand distribution group membership, cannot
access Active Directory attributes, and cannot inspect or modify
IRM-protected message content.
1.5. Expressions in Transport Rules
When you are matching text patterns in different parts of a message (such
as message headers, sender, recipients, message subject, and body) as
specified in a transport rule, you can use expressions in transport rule
predicates to determine whether a configured action should be applied to an
email message.
You can use simple expressions or regular
expressions. A simple expression is a specific value that you
want to match exactly in a message. For example, a simple expression could
be the title of a document such as Sales_Forecast.doc. Data in an email
message identified by a simple expression must exactly match that simple
expression to satisfy either a condition or an exception in a transport
rule.
A regular expression contains flexible notation that you can use to find a
text pattern in a message. The notation consists of literal characters and
metacharacters. Literal characters must exist in
the target string. They are normal characters, as typed. Metacharacters are
special characters that indicate how the text can vary in the target string.
For example the \d character matches any single numeric digit (note that
metacharacters are case sensitive), the \D pattern string matches any
nonnumeric digit, the \s pattern string matches any single white-space
character, the \S pattern string matches any single character that is not a
space, and so on.
For example, the following
EMS command creates a transport rule named “Check For Number
Pattern” that redirects any email message containing a number in the
format xx-xxx-xx-xxxx in its subject or body to the Kim
Akers mailbox:
New-TransportRule -Name "Check For Number Pattern" -SubjectOrBodyMatchesPatterns
'\d\d-\d\d\d-\d\d-\d\d\d\d' -RedirectMessageTo "Kim Akers"
1.6. Coding a Transport Rule That Uses an Expression
Because regular expressions can appear to be complex and lead to lengthy
EMS commands being written to interpret such expressions, administrators
often write code in the EMS to implement such rules. This code is not
complex programming but consists mainly of defining variables that simplify
the final statement of the rule.
A typical example detects that a number pattern is in the format of a U.S.
Social Security number. For the benefit of those not based in the United
States, Social Security numbers take the form
xxx-xx-xxxx (for example, 123-45-6789). The
transmission of such numbers in email messages is typically prohibited. The
following code, entered into the EMS, creates a transport rule that
prohibits the transmission of a U.S. Social Security number:
$Condition = Get-TransportRulePredicate SubjectMatches
$Condition.Patterns = @("\d\d\d-\d\d-\d\d\d\d")
$Action = Get-TransportRuleAction RejectMessage
$Action.RejectReason = "You are not permitted to transmit Social Security Numbers."
New-TransportRule -Name "Block Social Security Numbers" -Condition $Condition -Action
$Action
Note that this code, given as an example, blocks email messages that
contain any number that takes the form xxx-xx-xxxx.
Code that can specifically identify Social Security numbers by detecting
their valid prefixes would be much more complex.