DCM operations in ConfigMgr are defined by two object types:
Instances of these two object types are often called configurations collectively because they define a specific system configuration.
Microsoft built DCM knowing that every IT
environment is unique and that configuration standards and requirements
in each IT environment are different. Thus, DCM gives you the tools to
create configuration items and baselines from scratch according to your
individual needs and wants. The built-in editor is straightforward and
easy to use, allowing you to create simple to complex configuration
items and anything in-between.
Configuration Items
Configuration items encapsulate the checks that
DCM makes against a system to determine its compliance. Collectively,
these checks are called evaluation criteria.
To view or edit the configuration items present in a site, navigate to
Site Database -> Computer Management -> Desired Configuration
Management -> Configuration Items in the ConfigMgr navigation tree.
There are four types of configuration items:
Application—
A configuration item of this type checks for the existence of an
application and its associated settings. The application’s existence can
be assumed, checked by Windows Installer detection, or determined by a
custom script.
Operating Systems—
This type of configuration item checks for a specific operating system
version and settings relevant to that version. The operating system
version can be set by choosing from a drop down list of pre-configured
operating systems or by directly setting the version values.
Software Updates— These configuration items check the patch or update level of a system.
General— You can use this open-ended configuration item type for any purpose.
Software update configuration items are a
special type of configuration item, as they are not listed with the rest
of the configuration items in the console and you cannot directly create
them like the three other types. These are created when defining a
baseline, with their only evaluation criteria the installation status of
a specific software update chosen from the update repository. To use
software update configuration items, the ConfigMgr Software Update
feature, must be properly configured and working not only to
define the software update configuration item, but also to detect its
installation status.
There are two property types used to represent the evaluation criteria implemented by a configuration item:
Objects—
Objects check for the existence of discrete entities including files,
registry keys, and assemblies in the Global Assembly Cache (GAC), which
is the machine-wide cache used to store assemblies designed for sharing
by multiple applications on a system. Additionally, objects can also
check for the existence of specific permissions on registry keys, files,
and attributes on files.
Settings—
These evaluate the return value of queries made against Active
Directory, the Internet Information Services (IIS) metabase, the Windows
Registry, SQL Server databases, the Windows Management Instrumentation
(WMI) repository using WMI Query Language (WQL), or an eXtensible Markup
Language (XML) file.
Settings can also use custom
VBScript, JScript, or PowerShell scripts to determine compliance. In
addition to validating specific values, settings can check the number of
values returned from the query or script; referred to as the instance count of criteria validation.
Although not a perfect analogy, you can think of
objects as “physical” or tangible items that the operating system uses
and manipulates. Settings on the other hand describe how or with what
parameters the operating system or an application goes about its many
tasks.
Note: Using PowerShell Scripts
Unlike VBScript and JScript, PowerShell is not a
core component on all versions of Windows. Thus if you use a PowerShell
script, be sure that it is in fact installed on all of the systems
where the configuration item will be applicable.
The validation of each criterion and instance
count is configured individually to contribute to the compliance status
of the configuration item as a whole. Each configuration item has four
potential severity levels of non-compliance:
If
any criterion fails, the configuration item as a whole is marked as
non-compliant for that system. The highest severity level for any failed
check, including instance count checks, is used as the severity level
for the configuration item. Results of these checks are sent back to
ConfigMgr for reporting. Each failed check also produces an event
message in the Windows Application Event Log, except for the
Information—no Windows event message level.
The combination of the Objects and Settings
property types provide a wide range of criteria that DCM can check to
determine compliance. The addition of custom scripts, often used with
Microsoft sample baselines, gives DCM unlimited customizability and
flexibility.
DCM can restrict the evaluation of application
and general configuration items based on Windows platform applicability.
This configuration checks for specific Windows platforms and prevents
evaluating the configuration item on platforms not specified.
You can organize configuration items in several
ways. This includes categories and hierarchies and combining them into
baselines:
Assigning categories—
You can assign categories to configuration items (and baselines) to
improve filtering and searching in the console and reports, but they
ultimately serve no functional purpose. These categories cannot be
exported or imported and only exist on the server. Four default
categories are created at installation time:
Client
IT Infrastructure
Line of Business
Server
You can use these categories, delete them, or add new ones; no special functionality is associated with these categories.
Creating hierarchies—
You can organize configuration items into hierarchies by creating child
configuration items. Child configuration items inherit all the
evaluation criteria of their designated parent; these inherited criteria
cannot be changed or removed in the child. You can add additional
criterion, differentiating the child item from its parent.
One
common use of child configuration items includes specialization of a
more general configuration item. As an example, you may create a generic
configuration item that checks for organizationwide security standards.
You could then create child configuration items to check for the more
rigorous security standards of the Accounting and Human Resource
departments. This scenario prevents duplication and reduces effort when
an organizationwide setting requires changing, because you only need to
update the parent to update all the child configuration items. If you
are familiar with object-oriented programming, then this concept is very
similar to class specialization through inheritance.
Combining CIs— You
can combine configuration items into configuration baselines and then
assign the configuration baselines to collections for evaluation.
Configuration items can be part of multiple baselines, and multiple
configuration items typically combine to create a baseline. The next
section discusses baselines.
|
DCM and configuration items are foundational
for software updates management and the drivers catalog in operating
system deployment; software updates and drivers are actually stored as
configuration items in the database. This is most evident when setting
granular permissions on classes and instances in the console—there are
no entries for software updates, because these are all encapsulated by
the generic configuration item type.
|
Configuration Baselines
As stated earlier in the “Configurations”
section, configuration baselines group configuration items together;
the baselines are then assigned to collections for evaluation.
Configuration items are assigned to baselines using rules. Each rule is a
list of a specific type of configuration item. Rules available include
the following:
Operating system configuration items present and properly configured
Application and general configuration items required and properly configured
Optional application items that are properly configured
Software updates present
Application configuration items not present
In addition to the configuration item rules, an
additional rule exists to include other baselines. This essentially
groups the baselines together and combines their evaluation.
To create a new baseline, perform the following steps:
1. | Right-click
Site Database -> Computer Management -> Desired Configuration
Management -> Configuration Baselines in the ConfigMgr console
navigation tree and select New Configuration Baseline. This launches the
Create Configuration Baseline Wizard.
|
2. | The first page, the Identification page, allows you to specify a name for the baseline and choose a category.
|
3. | The second page of the wizard, titled “Set Configuration Baseline Rules” (shown in Figure 1),
allows you to define the rules previously introduced in this section.
You set them by clicking the blue underlined hyperlinks. These launch
one of three dialog boxes, depending on the rule you clicked:
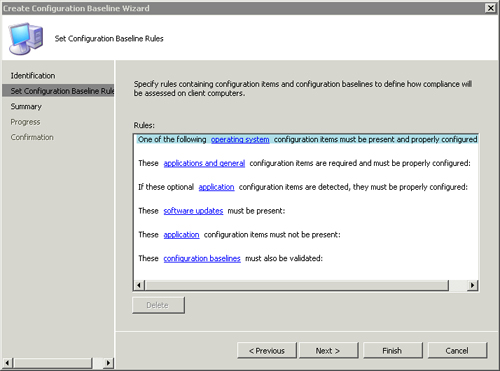
Each of these dialog boxes allows you to specify the object indicated by its name using sorting and filtering.
|
To modify an existing baseline, navigate to Site
Database -> Computer Management -> Desired Configuration
Management -> Configuration Baselines. Right-click the desired
baseline in the Details pane and then choose Properties from the context
menu. The baseline properties dialog box contains the following pages:
General—
Displays general metadata about the baseline, including creation and
modification times. This page also allows you to set or remove
categories from the baseline.
Rules—
Similar to the Set Configuration Baseline Rules page used during the
creation of the baseline, this page displays the configuration items and
baselines included and allows you to add more by clicking hyperlinks.
Relationships— This page displays the names of other baselines that include the currently viewed baseline.
Assignments—
This page displays all collections to which the baseline is assigned.
You also use the Assignments tab to modify and delete previously created
assignments for the baseline.
Security—
This page displays the class and instance security rights for the
baseline and is identical to every other security page in ConfigMgr.
You
can also view information from all these tabs by selecting any baseline
in the Details pane. This displays a Details pane at the bottom of the
window with four tabs corresponding to those listed previously (with the
exception of the Security tab). These tabs are view-only and offer a
quick way to view the details of a baseline without opening the
Properties dialog box.
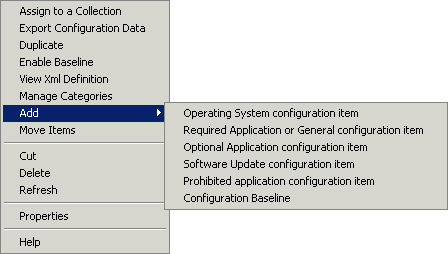
In addition to using the Rules tab of a
baseline’s Properties dialog box to add rules, you can select Add from
the context menu of a baseline. This gives you a flyout menu (shown in Figure 2)
with a choice for each of the rule types listed. Selecting one of these
works the same as selecting a hyperlink under the Rules tab.
Assigning a baseline is what triggers its
evaluation against a set of systems. Collections, being the standard
targeting mechanism for ConfigMgr, are what baselines are assigned to.
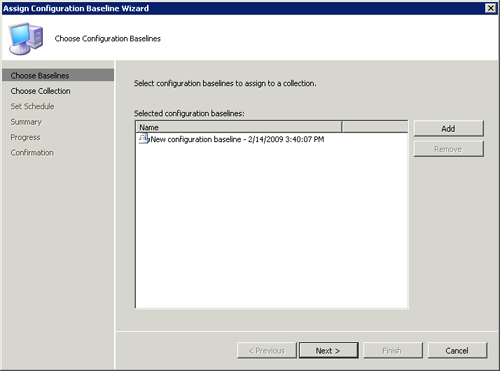
To assign a baseline to a collection, right-click it and then choose
Assign to a Collection. This launches the Assign Configuration Baseline
Wizard, as displayed in Figure 3. This wizard contains the following pages:
Choose Baselines—
Although you launch this wizard by clicking a single baseline, you can
select additional baselines for assignment on this first page of the
wizard.
Choose Collection—
Using this typical ConfigMgr page, you select which collection to
assign the baselines to and whether or not to include subcollections.
Set Schedule— This last page of the wizard includes two choices:
Simple schedule
Custom schedule
By
default, the value is set according to the schedule chosen on the
Desired Configuration Management Client agent.
Using DCM, configuration baselines are assigned
to ConfigMgr collections. The settings and values defined in each
configuration item in a baseline are compared against the current
configuration of the systems in the collection, according to the
evaluation schedule
for that baseline. The results of this comparison are returned to
ConfigMgr, where you can run a variety of reports to determine how the
systems fared on these comparison tests; this is also known as the compliance status of the system.
In addition to simply reporting on the
compliance status of systems and collections, you can build collections
using this same data to create remediation mechanisms. Because automatic
remediation of discrepancies is not a function of DCM, you must
implement some other mechanism to correct the configuration of systems.
The synergistic functions of ConfigMgr 2007 allow you to create software
distribution packages and programs to make these corrections.
As an example, if you create and assign a
baseline that checks for the existence of an antivirus product on every
workstation in a collection, any systems that fail this check are deemed
noncompliant. Typically, an organization reporting the noncompliant
status of systems will want to correct those as soon as possible. The
approach then is to create a new collection that queries the compliance
status of systems against this baseline, and use a software distribution
package to install the preferred antivirus product and assign the
package to the collection.
Microsoft understands there are many
similarities and common requirements between IT organizations, and has
released a large number of configuration baselines to use as a starting
point, as a reference, or as complete solutions. These baselines are
encapsulated in configuration packs (CPs). Types of available CPs include the following:
Regulatory compliance—
Configuration packs intended for regulatory compliance, such as SOX,
HIPAA, and the European Union Data Protection Directive (EUDPD).
Best practice—
CPs based on best-practice configurations used by Microsoft’s internal
IT department for major products such as Exchange, SQL Server, and
Windows Server.
Third-party software and hardware—
As with the development of OpsMgr management packs, many third parties
are starting to create and release CPs to help with your configuration
enforcement efforts while using their products.
To import a baseline downloaded from the
catalog, you must first extract it from the downloaded Microsoft
Installer package. These installer packages do not actually install the
configuration pack; they merely extract the necessary cabinet (.CAB)
compressed file (similar to a self-extracting executable) to a folder of
your choosing. Once this is extracted, perform the following steps to
import the CP into ConfigMgr:
1. | Navigate
to and expand Site Database -> Computer Management -> Desired
Configuration Management in the ConfigMgr navigation tree.
|
2. | Right-click
either Configuration Baselines or Configuration Items and choose Import
Configuration Data. This launches the Import Configuration Data Wizard
displayed in Figure 4.
|
3. | Click Add to launch an Open dialog box. Find and select the CAB file for the CP you previously extracted and click Open.
You can add CABs from additional configuration packs by clicking Add again.
To remove a previously chosen CP, select it in the list box and choose Delete.
|
4. | Clicking Next takes you to a summary page listing the configuration items and baselines that will be imported.
|
5. | Finally, click Finish to import the chosen CPs.
|
Configuration items in imported CPs are locked,
preventing you from modifying them in any way. Locked configuration
items are displayed with a lock icon. To use one of these configuration
items as a starting point, duplicate it by right-clicking it and
choosing Duplicate from the resulting context menu. The duplicated
configuration item will be fully editable. It is also recommended to
duplicate an existing, known-good configuration item or baseline before
editing it. (Known-good refers to an
item that has already successfully worked in an environment.) Using this
approach provides a solid rollback and baselining mechanism.
Although the CPs available from Microsoft’s
Configuration Pack Catalog are quite useful, they do not cover every
possibility and are somewhat generic at times. Eventually, you will want
to create your own criteria by modifying the CPs provided by Microsoft,
or creating your own to evaluate your systems. The next sections
discuss this activity, known as authoring.